Zakhist bezdartovyh merezh Wi-Fi.
submit Golovna Basic functionality
Vitannya!
Having prepared an article that will summarize all the main points and most effectively satisfy your needs,

How to steal Wi-Fi from a network
.
Who are we kidnapping?
The type of neighbors is obvious, but if you need to steal the Wi-Fi network in the office, then from colleagues from the other company:).

Well, if it’s serious, then the nutrition of the protection of dart-less measures is now even more relevant, which I have earned for the article in which I have described.
The article quickly became popular and received a lot of comments.
We set a password to access the Wi-Fi router

The first thing you need to do is to set up a drone-free Wi-Fi network.
By increasing this function, you can connect to the router any device whose MAC address is specified in the settings and permissions.
This is a very effective protection, but if you often connect new devices, it will not be very easy to immediately go into setting up the router and assign the MAC address to the device.
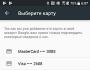
To get started, you need to find out the MAC addresses of the devices you want to allow connection to the Wi-Fi network. You can look at them in the settings, read the report. Whether it’s a phone or a tablet, you can look at the address in settings, in the “About phone” section.
And if the device is already connected to the router, all necessary information can be found on the “DHCP” tab – “DHCP Clients List”.

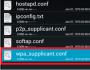
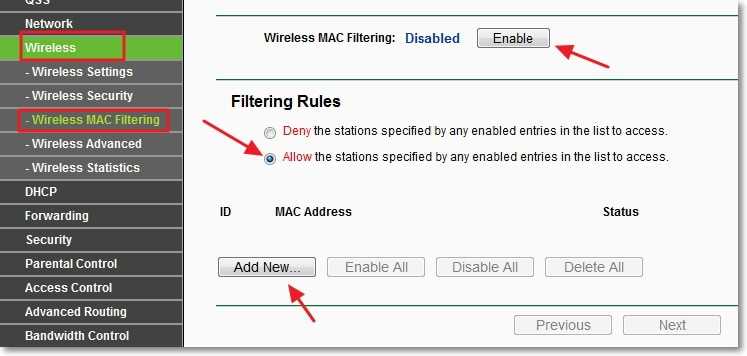
Now, go to the “Wireless” tab and go to “Wireless MAC Filtering”.
You can enable this service right away by pressing the “Enable” button.
Then we set the icon to the item
“Allow the stations specified by any enabled entries in the list to access.”

.
This means that only devices on the list can connect to Wi-Fi.
I press the “Add New...” button to add the MAC addresses of the devices that need to be allowed access.
Enter the MAC address, description (behind the rules), disable the Enable status and press the “Save” button. This method allows you to add all the devices you want to allow to connect to your router. Enable QSS (WPS) service
Password and MAC-address filtering are responsible for protecting you from the evil one.
It is true that the greater peace is at your discretion.
Unprecedented security methods, a simple password and easy setting of third-party hackers at home give attackers additional opportunities to attack.
In this article you will learn how to clear a WEP password, what filters you should follow, and how to ensure your drone-free security from all sides. Protection from uninvited guests Your line is not protected, so it’s too early for a third-party merchant to arrive at your drone-free line - perhaps not on purpose, even smartphones and tablets will automatically connect to unprotected lines.
Yakshcho at your non -honey -melted vicoristovye is the non -cultivated Z'ydnannya, a boti by special with the amendments with the content, the fading of the Iz fads, the suchist without a bunny vin is known in the all -north -winged cesnials.
However, in the Windows XP Home operating system, the situation with hidden access is simply catastrophic: behind the scenes, you cannot set passwords - this function is only available in the professional version.
In this case, all the measures will be completed through the non-theft of the guest account.
You can secure a boundary in Windows XP with the help of a small manipulation: launch the command line, enter “net user guest Your new password” and confirm the operation by pressing the “Enter” key.
After Windows is re-enabled, it will be possible to deny access to edge resources only if you have a password; unfortunately, it is not possible with more fine-tuning in this version of the OS.
Particularly popular among cybershares is the Aircrack-ng software package, which includes an add-on for adding and modifying WLAN adapter drivers, and also allows you to update the WEP key.
One of the evil methods is PTW and FMS/Korek attacks, in which traffic is swarmed and the WEP key is calculated based on its analysis.
In this situation, you have only two options: first, you should look for the latest firmware for your device, which supports new encryption methods.
If the generator does not update, it is better to consider using such a device, even in which you jeopardize the safety of your home.
It is a popular idea to shorten the radius of Wi-Fi, which reduces the visibility of the attack. Neighbors can still connect to your range, and criminals often use Wi-Fi adapters with a large operating range.
Public access points Places with free Wi-Fi attract cybershares, so a lot of information passes through them, and they can quickly use tools for evil people.
WPA 2
The greatest protection will be provided by WPA2 technology, which has been introduced by computer technology manufacturers since 2004.
Most devices support this type of encryption.
However, like other technologies, WPA2 also has its own weak point: with additional attacks on the dictionary or the brute force method, hackers can hack passwords - however, less often due to their unreliability.
Dictionaries simply sort through the keys in the databases - identify all possible combinations of numbers and names.
Passwords for the password “1234” or “Ivanov” are guessed by the computer so that the attacker’s computer never gets warm.
The bruteforce method transfers a random ready-made database, and, as a result, selects a password by searching all possible combinations of characters.
With this method, the thief can figure out any clue - the food will depend on how much time you need it.
Once you secure your router with a reliable password and use WPA2 encryption, you will no longer face any risk of security.
Just be sure you don’t give your password to other accounts.
Friends who have their smartphones, tablets or laptops want to access the Internet through your connection is a risk factor. For example, you cannot turn off the possibility that their devices are infected with unwanted programs.
However, you won’t be able to tell your friends through this, because top models of routers, such as Belkin N or Netgear WNDR3700, have guest access specially for such situations. The advantage of this mode lies in the fact that the router creates a close barrier with the user's password, and the home system does not get corrupted.
Reliability of security keys WEP (WIRED EQUIVALENT PRIVACY).
Vikorist pseudo-padded number generator (RC4 algorithm) for deleting the key and initialization vector.
The remaining components are not encrypted, but third parties can be used to create a WEP key.
Never leave your edge open.
If your home WiFi is not encrypted, this is not correct.

At any time we can connect to you and use your access to the Internet for our own purposes.
2. If possible, select the encryption type WPA2-PSK

If your router is configured for WEP encryption, you must change it to WPA2, since WEP (Wired Equivalent Privacy) is outdated and has serious consequences.
And WPA2 is the strongest in Vikoristan right now.

WPA is only suitable if you have devices that do not work with WPA2.
3. Turn on WPS.

If you do not use the WPS function, you must enable it.
In some models of routers, there is a serious spillover through the standard configuration.

As practice shows, 90% of WPS failures do not fail.
4. Change your SSID name for details.

The most commonly used SSID (Service Set Identifier) is the droneless router model, which makes Wi-Fi easier for the attacker.

Therefore, it is obligatory to change it to something else.
How can it be a word in Latin and numbers.
Most routers allow administrators to remotely connect from the Internet to the web interface or command line of the device.
If you do not need to, enable this function.
Through local adjustments, the device will be available.
So, having spent a lot of money to make sure that our home WiFi network is adjusted to the optimal level of security, you can avoid problems and avoid them.
Let us briefly explain what WEP, WPA and WPA2 are and what the difference is between them. WEP Decoding: Wired Equivalent Privacy. Shifts like
Security equivalent to dart connection
.
Let us briefly explain what WEP, WPA and WPA2 are and what the difference is between them. Obviously, the winemakers overestimated the trustworthiness of this defense if they gave it a name.
WEP is an old-fashioned security mode.
- Ensures a low level of zakhista.
- In Windows, WEP security mode is often called Open.
under closed type.
WPA
Wi-Fi Protected Access (Wi-Fi access theft)
Divided into 2 subtypes:
WPA-Personal (-Personal Key or -PSK)
WPA-Enterprise.
WPA-PSK
This option is suitable for home vikoristan. For authorization, you will still need a security key. WPA-Enterprise This is a more immediate and time-saving option for corporate measures to ensure a higher level of security.:
A Radius server is required for authorization.
WPA2
WPA2 is the current and shortened version of WPA security.
You can do this in both modes: PSK and Enterprise.
This means that it supports the AES type of CCMP encryption.
Due to the old technology, WPA2-PSK today is “stuck through”.
These are somewhat outdated methods that require you to write down a login and password, as well as encrypt confidential data during reception and transmission, seem, it seems, like childish babble.
I axis why.

Rіznovidy zakhista
Of course, it is clear that until recently the most secure connection technology relied on the WEP structure.

It advocated verification of the integrity of the key during a drone-free connection of any device and was based on the IEEE 802.11i standard.
The protection of the WPA2-PSK WiFi network works, in principle, in the same way; the verification of the access key works on the level of 802.1X.
In other words, the system checks all possible options.

However, there is a new technology that is called WPA2 Enterprise.
For WPA admin, it requires not only the need for a personal access key, but also the presence of a Radius server that grants access.
In addition, the system itself transmits the entire hierarchy of keys to the division of keys, as well as techniques that eliminate the so-called transferability problem.
In other words, if, for a drone-free network, the WPA2-PSK security system is used, the password is set in a sequence like “123456789”, it is not important to guess that the same key and password generator programs are we call you KeyGen or we hope for someone’s kshtalt, By entering the first four characters, four steps can be automatically generated.
Here, it seems, there is no need to be unique in order to guess the type of sequence that is being analyzed.
Ale tse, melodiously, already understood, the simplest butt.
As long as the date of the koristuvach’s people is included in the password, it will not be discussed.
You can easily be counted for these very registration data at social networks.
Digital passwords of this type themselves are completely unreliable.
It is better to use numbers, letters, and also symbols (you may be disappointed with the use of hot keys) and spaces.
However, such an approach can be blamed for the evil WPA2-PSK.
Here we will explain the methodology of the system itself.
On the right, when the QoS router mode is enabled, you can not only read the information that is transmitted, but also replace it with fragmented information.

In 2009, Japanese fachians presented a technology that allows the evil hour to shorten to one hour.
And in 2010, information appeared in Merezhi about the easiest way to hack the Hole 196 module, which is found in WPA2, using a private key.
There is no mention of how keys were handed over to the generated keys.

Initially, the attack on the dictionary is carried out using “brute force”, and then the expanse of the drone-free connection is scanned by re-storing the packets that are transmitted and their subsequent recording.

It is enough to create a connection, as you will immediately be subject to de-authorization and re-storage of the transmission of email packets (handshake).
After this (if the user has already passed authorization when connecting), the user can easily be connected to the network.
In this case, when logging in again, the system will repeat the login authorization, after which all access passwords can be recovered.
Then show up with a “handshake”.