A look at cost-free tools for pentesting web resources and not only v2. [email protected]- Scanning documents as needed
For some richly functional attachments, the browsers give software security, you can start by pressing the “Scan” button, the document is put into the folder or folder or fencing resource, and then the helper can easily take the document through the border. But not all attachments can have such functions, so in this video we can look at the program that allows you to scan in the distance, tobto. according to measure. Do not require physical presence at the computer, to which the scanner is connected rich functional attachment, so that you don’t respect the practitioner who works.
And with the help of the TWAIN Web program, you can get it from the official site of retailers http://unit6.ru/twain-web. The main advantages of this program are those that it is absolutely cost-free and easy to use, which means that only the server part is installed on the computer, to which it is connected to the attachments that are scanned.
We could, on the server, the scan can be installed operating system Windows XP and older, as well as .NET Framework 2 and higher, and on the client there is no browser and access to the scanning server.
Download the program and run the installer ( Expansion nalashtuvannya \ Way too much quantity \ Specify the port). For locking, port 80 is required, but I don’t mind yogo, so that this port can be already used by Skype or a web server. If you know for sure that neither the web server nor Skype will be installed on this machine, you can lock out port 80. I'll assign 81.
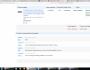
The page is taken from the web interface for scanning. On scho to us varto turn respect, tse at the address http://127.0.0.1:81/ [email protected] Vlasne at the address tsієї storіnki mi і we will knock from other computers, schob vikonati skanuvannya. More precisely, correcting the IP address of the computer on which the program is running. Here we have the addresses 127.0.0.1, these are the addresses of the local machine, so we went on our own at once.
We also need to create a rule in the Windows firewall, or in third party firewall You must not override the standard Windows Firewall. (Start\Control Panel\ Windows Firewall \ Additional parameters\ Rules for incoming connections \ Create a rule \ For programs on port \ TCP 81 \ Allow connections \ For all profiles )
Now try to scan the document from client computer, for which address row introduced http://192.168.0.4:81/ [email protected] (192.168.0.4 - IP addresses of the scanning server). The Internet interface appeared, which means that the service is running on the server and the firewall let us through.
Scan parameters:
- select scanner- Here, sound the presence of 2 extensions, not the TWAIN driver, which is supplied by the WIA driver. I especially had to scan only through WIA, so I choose it. When switching, you can tell which range is allowed to be trimmed, as you can see, the TWAIN driver sees unrealistic numbers, and WIA is similar to the truth;
- I have that number;
- allowed DPI- Sound enough 150, so the file is small and everything can be looked at;
- color, output file type and paper format.
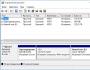
If you want to scan a piece of documents later, then the item "Batch scanning". Here, you should indicate the number of scanned documents and the amount of time between scans, tobto. hour, which will be needed to replace the arkush on the scanner in seconds. This blockage is also eliminated during the first scan, so that you can get to the scanner and put the document.
And here is your own subtlety, you can provide scanned documents from savings in the environment jpeg file s. Ale, in Internet Explorer, you will soon be able to download it, save the file or open it, then all the same you will have to go to the computer to select a file. In this situation, you can save documents in pdf file, then after the completion of the scanning of all documents, you will be asked to save the document.
If you need to scan the leather arkush into an okremium jpeg file, then you can speed it up Google browser Chrome, documents are automatically saved from the appointment of the father, without asking. That and vzagali, in Chrome everything is more adequate, as you Internet Explorer, I didn’t specify the name of the file that numbering, but here everything is miraculous. Another varto vrahuvat, scho file numbering continues for the rest of the scan, navit if you haven’t scanned.
Now, we can just create a shortcut on the work table for a given side, and as you have a border with a domain, for help group policy you can spread this label on all computers for the treatment of infirmity!
In this rank, you can scan scans from such attachments like telephones and tablets, one mind, so that the stench was in one measure, and then it was the same through the browser.
If you need to change the port every hour, on which the server part of the program works, you can change it at any time ( Start \ Programs \ [email protected]\ Configuration)
It is also possible to specify an automatic restart of the scanning service, in case of failures (Start \ Control Panel \ Administration \ Services \ [email protected]\ Startup type: automatic \ Update: on all failures - service restart
And just as you have wine like a food proposition, go to the retailers, stink of similar initiatives!
Dr.Web CureIt is a cost-free anti-virus scanner for home koristuvannya based on the kernel antivirus software Dr.Web, which can be effectively misinterpreted on the same computer without installing the Dr.Web anti-virus itself.
Luxurious Dr.Web CureIt utility you can see the file viruses, Trojans, macro viruses, viruses that infect MS Office documents, spyware programs- Spyware, programs, password recovery, advertising programs - Adware, hacker utilities.
Be warned that the Doctor Web Kurate utility does not attack in real time. CureIt's anti-virus databases are not automatically upgraded, so that the computer of the attacker needs to re-enable Dr.Web CureIt with new anti-virus databases.
Dr.Web CureIt free download
Get Free Dr.Web CureIt- A utility that is good for your computer. Our site provides all updates to the software so that you have the latest version of Doctor Web Curate.
Do you need a term to download Doctor Web? Remember that your previously installed anti-virus package does not cope with the workload on a new job and misses goals at the gates of the OS?
For the very purpose of which we are giving you the opportunity to take the mitte to help.
On the side, you need to know a utility in such situations, so that you can perform a background scan of your system in order to reveal scrambled files.
Why is it special
Doctor Web can, however, if you need an offline version, the Doctor Web scanner is right for you. The very simplicity of the word is the key to understanding, all that matters to you, so just grab the Doctor Web scanner. Being completely autonomous, we do not have the ability to install and carry out all our operations in background mode. Availability and a lot of optional configurations possible do a deep scan of the OS. This "little giant" can create healthy competition with a full-fledged anti-virus software package. A guarantee that viruses, like stinks, will be detected - is issued a certificate of the retailer for safe scanning (ICSA). 
Goodwill
Your greater "vagovitia" protection (already installed on the PC firewall) does not remember what it is for the new robot and becoming a defense against virus attacks. This option has the ability to blame "welds" between programs disabled. If you blame the power supply, then it’s a well-organized summary of the operations, so it’s possible to turn the computer into a virus Doctor Web.
Choose the required mode, and the decision will be broken for you
Before that, as you will give a hint, let Dr Web Scanner proceed to its direct bindings, select one of the three modes of conducting the scan.

We will help you to protect your PC again
Tim is no less, the utility cannot be called a panacea for successful bids, but there is no need to check for the presence of previously zipped files in the system, but you can’t help online. For more roaring software, you still have to get the Dr. Web scanner, only new version- . We will help you with cherries and food, you can easily find the shards of yoga in our library.
For the sake of it) and sent її to the competition for the SekLab (and published the request, but for all reasonable reasons її did not win anyone). The competition is over, the results have been announced, and in all honesty I can publish this article on Habri.
Web add-on pentester tools without cost
In this article, I'll tell you about the most popular tools for pentesting (penetration tests) of web stunning with the "black screen" strategy.For whom we look at utilities, which will help us in our kind of testing. Let's take a look at the following product categories:
- Merezhev scanners
- Scanner of breaches in web scripts
- Exploiting
- Automazation injection
- Debuggery (sniffer, local proxy only)
Merezhev scanners.
The main task is to open the available services, install their versions, and select the OS as well.IP tools

IP-Tools - such a collection of various merging utilities, which is supplied with GUI, is “assigned” to windows to koristuvachs.
Port scanner, global resources scanner (shared printers/folders), WhoIs/Finger/Lookup, telnet client and much more. Just a handy, quick, functional tool.
There is no special sensation to look at other goods, but the oscalls are rich in utilities and all stinks can have a similar principle of robotics and functionality. All the same, nmap is the most victorious.
Scanner of breaches in web scripts
Trying to know popular inconsistencies (SQL inj, XSS, LFI / RFI only) or pardons (not deleted clock files, directory indexing only)Acunetix Web Vulnerability Scanner - please note that this is an xss scanner, but I don't know that. No-cost version, available on request, giving great functionality. Call the people, as you launched your scanner for the first time and the first time you took the call for your resource, you are shocked by a small shock, and you will understand why, robbivshi tse. This is an even more difficult product for analyzing just all the quirks on the site, and it works not only with sites that are familiar to us in php, but with other languages (if you want to see the language, it’s not ostentatious). There is no instruction to describe especially the sensation, the scanner's oscillators are simply “fucking up” dії koristuvach. It is similar to "dalі, dalі, dalі, ready" for a typical installation of any software.
Nikto

Nikto is an Open Source (GPL) web crawler. Allows for routine manual work. Searching the target site for unseen scripts (such as test.php, index_.php, etc.), database administration tools (/phpmyadmin/, /pma and similar), etc., so that the resource is sorted into the most common pardons, like winickles sound through the human factor.
Plus, if you know what a popular script is, then you can check it for exploits that happened (like in the database).
Inform about the available "nebazhan" methods, such as PUT and TRACE
Well, and so on. It’s more convenient, as you are working as an auditor that day, you conduct an analysis of sites.
Z minus hotiv bi signifies a high vіdsotok hibnyh spratsovuvan. For example, if your site is a 404 pardon (if it can be blamed) it looks like a headache all the time, then the scanner will tell you that your site has all the scripts and all the inconsistencies from yoga base. In practice, it is not so often mentioned, but as a fact, it is rich in the structure of your site.
Classic vikoristannya:
./nikto.pl -host localhost
Wikto
Wikto - Nikto under Windows, but with some extras, like "fuzzy" logic when translating the code for pardons, GHDB tweaking, sending folders to the resource, real-time monitoring of HTTP requests / requests. Wikto is written in C# and powered by the .NET framework.
skipfish

skipfish is a web crawler by Michal Zalewski (known as lcamtuf). Written in C, cross-platform (Cygwin is required for Win). Recursively (for a long time, close to 20-40 years old, although the last time I worked at 96 years old) bypass the entire site and know all the powers that be in safety. It also generates a lot of traffic (per gigabyte of input/output). Ale, everything is good, more time, even more hours and resources.
Typical vikoristannya:
./skipfish -o /home/reports www.example.com
The "reports" folder will have the HTML name, butt .
w3af
- Web Application Attack and Audit Framework, an open-source web quirk scanner. Maє GUI, but you can pratsyuvati z-pіd console. More precisely, the framework, p.
You can tell about yoga for a long time, it’s better to try yoga:]
A typical robot with it is brought up to the choice of profile, marking, marking, power, launch.
Mantra Security Framework

Mantra is a dream that came true. A collection of free and critical IB tools that can be inserted into a web browser.
Dzhe korisnі when testing web zastosunkіv at all stages.
The prompt will run until the browser is installed and launched.
Indeed, there are a lot of utilities in this category and it is easy to see their specific list. Most often, the leather pentester determines the set of required tools.
Exploiting
For automated and manual sampling of inflections software security In scripts, write exploits, which would be more necessary to pass parameters in order to break through security. And є products, yakі pozbavlyayut manual search for exploits, and then zastosovuyut їх "on the fly". About this category at once.Metasploit Framework

The Metasploit® Framework is such a monster in our right. Win so vmіє, scho іnstruktsіya viyde on kіlka articles. Let's take a look at automatic exploitation (nmap + metasploit). The bottom line is, Nmap will analyze the port we need, install the service, and metasploit will try to get to the new exploit, with the service class (ftp, ssh just). Instead of text instructions, I will insert a video to report more popularly on the topic autopwn
And you can easily automate the robot we need exploit. For example:
Msf > use auxiliary/admin/cisco/vpn_3000_ftp_bypass
msf auxiliary(vpn_3000_ftp_bypass) > set RHOST
msf auxiliary(vpn_3000_ftp_bypass) > run
Indeed, the possibilities of this framework are already great, to that, as if they were wrong to get lost, let's go for help
Armitage

Armitage - OVA cyberpunk GUI for Metasploit. Visualize the goal, recommend exploitation and hope to expand the capabilities of this framework. Zagalom for those who love, so that all the garno looks spectacular.
Screencast:
Tenable Nessus®

Tenable Nessus® vulnerability scanner - there are a lot of things, but we need one possibility - a target, for some services - exploit. No-cost version of the product "home only"
Victory:
- They took over (under their system), installed, registered (the key came to the mail).
- Launched the server, added a koristuvach to Nessus Server Manager (Manage users button)
- We go for the address https://localhost:8834/ and we need a flash client from the browser
- Scans -> Add -> save the fields (choose the appropriate scan profile for us) and emboss Scan
To check the practicality of services before exploits, you can twist more than Metasploit Framework descriptions, or try to know the exploit (for example, Explot-db, packet storm, explot search, etc.) and twist it manually against own systems
IMHO: too bulky. Grafting him as one of the leaders in the software industry directly.
Automation of injections
Poshuk іnєktsіy roam a lot of web app sec scanners, but stinks are still just bad scanners. And є utilities, yakі without intermediary are engaged in a search and exploitation іn'єktsіy. About them at once and timetsya.sqlmap

- open-source utility for searching and exploiting SQL injections. Supports the same database servers, like: MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, SQLite, Firebird, Sybase, SAP MaxDB.
A typical vikoristannya is built up to a row:
Python sqlmap.py -u "http://example.com/index.php?action=news&id=1"
Vistachaya manualiv, including Russian mine. Softina is even easier for the pentester's robot for an hour of work on the cym directly.
Dodam official video demonstration:
bsqlbf-v2
bsqlbf-v2 – perl script, bruteforcer "blind" Sql injection. Pratsyuє yak i z integer url values, so і z ryadkovymi (string).Supporting the database:
- MS-SQL
- MySQL
- PostgreSQL
- Oracle
./bsqlbf-v2-3.pl -url www.somehost.com/blah.php?u=5 -blind u -sql "select table_name from imformation_schema.tables limit 1 offset 0" -database 1 -type 1
-url www.somehost.com/blah.php?u=5- Posilannya with parameters
-blind u- parameter for injection (the rest of the address row is taken for locking)
-sql "select table_name from imformation_schema.tables limit 1 offset 0"- our full request to the base
-database 1- database server: MSSQL
-type 1- type of attack, "sleep" injection, based on True and Error (for example, syntactical pardon)
debuggery
These tools are mainly vikoristovuyu rozrobniki in case of problems with the results of the coding of your code. But it’s also directly important for pentesting, if you can change the data we need “on the fly”, analyze what our input parameters (for example, when fuzzing) have just.Burp Suite
Burp Suite - a set of utilities that help with penetration tests. At Merezhi lie a garniy look at the Russian view of Raz0r (true for 2008 rec).AT free version enter:
- Burp Proxy - local proxy that allows you to change the already formed requests from the browser
- Burp Spider - spider, shukaє Info files that directory
- Burp Repeater - manual enforcement of HTTP requests
- Burp Sequencer - analysis vipadic values in forms
- Burp Decoder - standard encoder-decoder (html, base64, hex etc.)
- Burp Comparer - component of row setting
Fiddler
Fiddler - Fiddler is a proxy that logs all HTTP(S) traffic. Allows you to keep track of your traffic, set a breakpoint" and "grow" with input or output data.
More Firesheep, Wireshark monster and others, choose for the shorty one.
Visnovok
Obviously, a skin pentester has its own arsenal and its own set of utilities, which is simply impersonal. I have tried to bring some of the best and most popular. If only I could get to know some of the other utilities directly, I’ll bring the power down.Infection pіd hіvіduvannya vіdvіduvannya vіdіv z mobile pіdіvіv
Sites on the Internet are attacked by malicious scammers, as if targeting mobile devices. Seeing such a site from a computer, you will spend on an innocent Internet resource, and visiting the axis on a new smartphone, you will be secretly redirected to the site with an unacceptable "surprise". For the help of evil sites, evildoers can spread all the difference shkidlivі programs The most popular of these and various modifications. Spend the victim lying down because a Trojan of some family gets into your mobile app, - that’s because of a shoddy charge. Read more about this phenomenon in our news.
To the respect of the koristuvachіv mobile annexes!
Install on mobile attachment Dr.Web anti-virus for Android with component URL filter. A gloomy filter to limit access to non-recommended and potentially unsafe sites for dekilkom categories - this is especially important for protecting your children from unsafe Internet content.
URL filter present only in the fully functional version of Dr.Web for Android (it is not available in Dr.Web for Android light). For purchasers of Dr.Web Security Space and Dr.Web Anti-Virus, Dr.Web for Android - without cost.
To the respect of the koristuvachіv PCs and portable computers!
Install Dr.Web Link Checker
These are no-cost extensions for re-checking Internet sites and files that are taken from the Internet. Install an extension to your browser and increase the price All-Sveta cobweb, do not be afraid of a virus attack!
Get Dr.Web Link Checker free of charge for
| Opera |
With the help of the Dr.Web online file scanner, you can freely scan the files that are suspected in you, if they have viruses and malware programs.
You edit your files with the help of your browser, the stench is rushed to our server, the rest version Dr.Web with a new set of additional virus bases, and you accept the results of the scan.
How to scan a file or a few files with Dr.Web Anti-virus online?
- To check 1 file: press the button "Look" and select a file, which is called suspicion. Press the button "Change" to expand the scan.
- The maximum file size is 10 Mb.
- To revise a small file: move the files to an archive (WinZip, WinRar or ARJ format) and extract the archives by pressing the "Look around" button. and click on the button "Change". The verification protocol will be included on the skin file in the archive.
IMPORTANT! Antivirus scanner Dr.Web will help you designate the file(s) that you want to infect, or send you for verification, or not tell you to ask your computer to infect your computer. For re-verification hard drivesі system memory Vykoryst our cost-free utility CureIt! .
You can also check local lines for help centrally kerovan lace utility Dr.Web CureNet!
Upload suspicious file