Here are the ways to unlock Windows XP. Windows is blocked: what to do, how to unblock it? How to unblock the system
Once you launch an unknown program, your computer stops responding to commands, and your desktop takes on a characteristic appearance:



This means that you have become a victim of Trojan.WinLock, or simply a nasty Trojan that will tempt you to pay the evildoer a pittance for the opportunity to exploit your PC. This situation is not uncommon, although the Windows blocking epidemic has already passed. In an hour of using this method of health care, much evidence has been accumulated to reveal and “reveal” this kind of infection, aka, prote, the method of blocking Windows, the criminals will thoroughly research it to this day.
It is necessary to say that regardless of the threat of data loss on the PC once the “fine” is not paid, nothing like this is ever expected. And with a quick approach, it is possible to quickly remove the lock without having to reinstall the system. If you see the nasty “Computer Blocked” banner on your screen, don’t rush to hand over your cybercrime money - you won’t get the code to unlock it.
So that you don’t feel hopeless in such a situation, we have prepared for you a description of the methods used by Trojans and a number of ways to combat them.
See the system blocking
We are reviewing the methods used to block your computer under Windows XP.
- Modification of the head backup record (MBR), which, as you remember, occupies the first sector of the hard drive. In this case, the important code is rewritten or moved to another place, and instead of this, it is practical that after turning on the PC, the control unit will open the corrupted program. This type of malware has been renamed Trojan.MBRlock.
- Locking the desktop by modifying the system registry, or more precisely, the areas responsible for starting Windows and automatically starting applications. In this case, system files are replaced, and a Trojan program is launched along with them.
- Rewriting (patching) files that are critical for running Windows. With this method of blocking, there is no need to modify the registry, as well as poor code, records in system files, and control is lost in any case, and the blocker will be much more complex. Consider using Userinit.exe, Explorer.exe, LogonUI.exe, Taskmgr.exe, and others for distribution.
- This is a method of blocking Windows, such as preventing the launch of any programs and the execution of any actions on the computer, in addition to reading the information about the benefits of the locker. In this case, you can safely close it, but it’s still not possible to run it on your PC - if you try to work, you will be “blocked by the administrator.” Windows appears to be blocked through group policies. This principle is followed by Trojan-Ransom.Win32.Krotten (classified by Kaspersky Lab).

In addition to the overprotection of “pure” types of blocking, they are sharpened and more sophisticated, which means there are several ways to autorun the Trojan code. For example, changing the registry and patching system files, as well as placing multiple copies of the Trojan on the hard drive, all of which can be replicated one after another.
Favorite places for spreading Trojan files in Windows XP are these directories:
C:\Documents and Settings\Potochny koristuvach\Local Settings\Application Data
C:\Documents and Settings\All Users\Local Settings\Application Data
C:\Documents and Settings\Temporary Internet Files\Local Settings\Temporary Internet Files
C:\Documents and Settings\All Users\Local Settings\Temporary Internet Files
C:\Documents and Settings\Potochny koristuvach\Local Settings\Temp
C:\Documents and Settings\All Users\Local Settings\Temp
C:\Windows
C:\Windows\Temp
C:\Windows\System32
C:\Documents and Settings\Potochny koristuvach\Main menu\Programs\Autozavantazhenya
C:\Documents and Settings\All Users\Main menu\Programs\Automatography
And autorun requires additional entries to the following sections of the registry:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
Parameters: Userinit, UIHost, Shell.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\userinit.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\explorer.exe
Debugger parameter
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows
AppInit_DLLs parameter
What's wrong, is Windows XP blocked?
Most blockers operate not only in normal mode, but also in safe mode, and in some cases they simply turn on the ability to engage in safe mode, in various other sections of the registry. If you have a blocked Windows XP, you may have to solve the problem by using alternative portable media - so-called live disks (Live CD) with a wireless operating system. By using this type of computer, you can deny access to a hard drive that appears to be blocked. Later we will figure out how to work from a Live CD, but for now we are trying out simpler methods, which will always work, but in many cases they will work.
The simplest method for unblocking a computer
This method was discovered by the Koristuvachs in an experimental way. In cases of folding blocking, it is unlikely that it will help, but if you try all one product, then all the steps will take you no more than 5 minutes.
- Having seen the “Windows blocked” banner on the screen, restart your computer and go to BIOS Setup before starting the system. On the first tab "Main" (in Avard BIOS - menu item "Standard CMOS Feature") move the system date 2 - 3 years forward or backward. To exit the settings for saving, press F10 and “Y”.

- Install Windows, since there is no banner on the desktop, download a free antivirus utility, for example, Kaspersky Virus Removal Tool or else Dr.Web CureIt! and carry out a scan. Should you download these programs if you already have an antivirus? For those who change the date, it certainly doesn’t matter.
- After removing the Trojan, go back to the BIOS settings and change the current date. That's it.
Online services of antivirus companies for unlocking Windows
If the previous steps did not help you get past the “Computer Blocked” banner, you can try to find an unlock code using the online services of anti-virus companies. This option helps with 50 – 70% of the losses, but it will only work if you have another PC (phone, tablet, etc.) with Internet access. Below are instructions sent for using these services.
Trojan.WinLosk deactivation service "Kaspersky Lab"
- Rewrite the text of the notification as you read it on the screen, then paste it in the appropriate field.
- In the recipient's field, enter the telephone number, instructions from the acquaintance who are requested to transfer the money.
- Click the "Remove unlock code" button and try to remove the banner.
- After logging in to Windows, carry out an anti-virus scan of your PC, the fragments of the Trojan blocker file will still be on the system and can be blocked again.
- Enter your phone number or contact number in the field provided and press the “Search Code” button.
- If nothing is registered, you can try to find the confirmation code by looking at the banner.
- After unlocking, scan your computer for viruses.
- Enter the notification text from the “Windows blocked” banner and the phone number listed there in the field provided.
- Press the “Send” button and try to quickly register with the codes.
- After the computer is unlocked, scan it for virus.
Design for automatic PC unlocking
If previous visits did not cause any problems with your PC, as before, blocking, you can remove the banner using additional specialized programs on downloadable disks (Live CD). Below are the tools that allow you to automatically unblock Windows XP and eliminate the Trojan program.
AntiSMS
A completely automatic utility that detects all types of modifications of trojans and updates the standard settings of the system. Recommended for homeowners who do not have access to PC administration. The entire robot program is logged in and launched by double-clicking on the shortcut on the desktop of the vanity wearer.

Another valuable disk can help if your Windows XP has become blocked. The utility will automatically find and remove the Trojan program, as well as update corrupted files and the system registry. On a commercial basis, AntiWinLocker can be used to protect Windows from blockers by installing your computer.
To remove a banner for this additional program, you need a minimum of actions:
- sign up for AntiWinLockerLiveCD, accept the license agreement and click the “Start” button;

- select the “Automatic start” item from the menu;

- wait for the option to replace files (if necessary) by marking them in the list and clicking “Viconty”;

- After completing the program, start the computer from the hard drive - the blocking will be removed.
Another universal tool that can help not only with outbreaks, if the computer is blocked, but also for any virus infection. Equipped with the function of updating virus databases via the Internet.

To scan, just launch the scanner from the desktop, select the scanning area and click “Start scan”.

The instrument that is no less simple is the one in front. It also allows you to easily detect various virus problems on your PC, including when your login to Windows XP is blocked. There is a possibility of “intellectual scanning”, which is useful for searching for unknown and unwanted objects.

Manually unlocking Windows XP when using Live CD
Now let's look at the manual methods of removing corrupt code, which is important to Windows XP. In order to use them, it is necessary to have at least a sufficiently verified PC, otherwise problems after trying a remote banner may be larger, or at first. For the first method, clean your computer with additional professional utilities Universal Virus Sniffer(uVS) we need some kind of fancy disk based on OS Windows. We are speeding up Alkid Live CD.
Alkid Live CD and uVS
This method, one might say, is the most labor-intensive, since all operations have to be completed manually. However, in extreme situations, if the original Windows XP is blocked, there is no choice, and we will choose those that are at hand. Come on, let's see.
- Download it on another computer and unpack the uVS program onto a flash drive (as you don’t have another PC, you can use it on Alkid Live CD after setting up an Internet connection).
- Connect the flash drive to the locked computer.
- Get excited about Alkid Live CD.
- Run the file start.exe from the uVS directory (which in our case is located at the address F:uvs).
- In the "Startup mode" window, click the "Select Windows directory" button and go through Explorer to the Windows folder of the locked system. Click "OK".
- Click “Run under the exact tool.”

- After scanning, a list of suspicious files will appear in front of you, and in a prominent place is our Trojan-magazine.

- To view reports about this file, click on a new window - a window will open, where, in addition, the method of autorun will be indicated. Our example has a registry key that launches Windows Explorer (explorer.exe).

- Now let's move on to removing the Trojan and updating Windows to normal startup. Close the window of authority and click on the file with the right mouse button. Select the command “Delete all messages at once from a file” from the context menu.

- To update the changes to the registry key, select “Tweaks” from the top “Additional” menu.

- Click the button “Discard Winlogon keys at the cob mill.”

- Close the program and recover the computer from the hard drive. You won’t see the banner anymore.
Important! If you include a system file in the list of suspects, especially Userinit.exe, LogonUI.exe, Explorer.exe or Taskmgr.exe, you are likely to change and replace the blocking code. Such files need to be replaced with their clean copies, which are stored in the folder C:WindowsSystem32dllcache.
ERD Commander 5.0
If you have this wonderful Windows XP update tool at your fingertips, you can get to the “Computer Blocked” banner much easier, for example, by using the system update function. To deny access to it, download the PC from the ERD Commander version 5.0 disk and proceed to the next steps.
- Press the “Start” button (analogous to start), select “System Tools” from the menu, and then “System Restore”.

- Launch a familiar system update program. Select an appropriate control point and click “Next”. After the procedure, remove the disk from your hard drive. The “Windows blocked” banner will no longer bother you.

Removal of free code from MBR
As soon as you turned on your PC, even before you became hooked on Windows XP, you were greeted with the following picture:

This means that you have suffered from a malicious Trojan that has registered itself in the MBR. You can remove the bad code from all the costs that have been reinstated here - for which you need high-quality anti-virus products, which are called below. And now let’s give a few compliments to someone who is not ready to work in this situation.
The surest way to get Windows XP without any restrictions
Many people know the purpose of the fixmbr console command - it is used to overwrite the first sector of the hard drive. And, in a good way, it is my responsibility to renew the corrupted code, immediately seeing the Trojan sitting there. Alas, that was not the case. In the process of rewriting a non-standard MBR (and if it is infected with a Trojan, it will be non-standard), the partition table that is located on the hard disk after the MBR code has been modified is often damaged.

If we ignore the console update and quit fixmbr, instead of informing about those that the computer is blocked, it is best to do the following:
What does it mean to corrupt the partition table? Well, we can’t fascinate the system anymore.
Clean the MBR for additional anti-virus utilities
For a correct and safe update of the head image, you can use the following entry:
- AntiSMS;
- Kaspersky Rescue Disk;
- Dr.Web Live CD;
- LiveCD ESET NOD32.
These tools are more than enough to unblock Windows XP, including the like.
How to unblock Windows?
It’s unlikely that you’ll want to worry that it’s much easier to avoid infecting your computer with Trojans and then fight them. To make sure your PC doesn’t get blocked, follow these awkward rules:
- install a reliable antivirus and do not forget to update its database regularly;
- Before launching an unknown file, do not hesitate to scan it for safety;
- do not follow unknown messages sent to you by mail or through instant messengers, from your accounts;
- Install Windows XP updates promptly - this will close a lot of holes through which bad programs enter the system. And we hope that you will never see the “Windows blocked” notification on your laptop again.
Of course, you felt that you might have ended up in such a situation if you downloaded a file or submitted something suspicious to a site on the Internet.
The PC immediately became unprotected and a banner appeared asking you to enter a code in order to unlock the computer, which can be unlocked by sending an SMS or renewing your phone account for a sum of money.
Why bother? Do you still have a chance to unblock your computer without SMS? Let's look at a number of options for our actions in order to avoid becoming a “milking cow” for scammers.
Even after the stench has increased, you will already recognize your phone and, moreover, will be able to log in with your telephone operator. This means that taking money from your phone is not going to be a big problem. Otherwise, let’s not get into trouble and just try to deal with the problem on our own. Ozhe, yak?
Try unblocking the banner through the dispatcher
This is one of the simplest methods. Who knows, maybe the shahrays are not that literate and are more likely to bluff? So, click on the task manager and select the task when we close our browser. For this purpose we immediately press the Ctrl+Alt+Del keys (pluses, of course, do not press). Then the window presses “Start dispatcher”:

All this time, different things can be hidden from the operating system, but I believe the essence is clear. Then the department manager appears. Here we are responsible for clearing the settings of our browser. Click on the row next to the browser and then click on the “Set assignment” button:

Before speaking, this method can be applied both for this purpose and for any other purpose. To close a program that has frozen, for example. It is important to say that you should not quit the first test, when the dispatcher window flashes and disappears again.
In such cases it happens that repeated pressure helps Ctrl+Alt+Del and more than once, and up to 10 times after! More, melodious, lacks sense. Viishlo - good. No – the house is far away.
Try to unblock your computer through the registry
Now we are trying the next option - a more folding one. We place the cursor at the field for entering the code, press Ctrl+Alt+Del and respectfully look at the banner.
Of course, it will not be the same as mine, but the option to send an SMS or add the number and line for entering the code or password will be obligatory. If, as a result of our actions, the cursor disappeared, it means that the keyboard switched to the task manager:

Now you can press Tab, and then Enter and an empty work table will appear in front of you, which will do everything, without “Start”. As it happened, now in order to “unblock our problem” you need to go to the registry, the remains of the virus will be registered there.
Onslaught Ctrl+Alt+Del. Then “Start task manager”. In the new window - "File", then in the drop-down menu "New task (Visconati...)":

Next we enter the command “regedit” and then press “OK”:

The "Viconati" command can be accessed simply by pressing the Win+R button on the keyboard. For those who don’t know, Win is a button in the small Windows box, click on the bottom left end of the keyboard.
Once everything has worked out, we will update it in the registry editor. Here, be very respectful and careful. Don’t touch anything fancy. Incorrect actions can lead to unacceptable, and sometimes untransferable, results from the computer.
So we need to go here: HKEY_LOCAL_MACHINE/SOFTWARE/Microsoft/Windows NT/CurrentVersion/Winlogon. I will show you two windows so that you understand where and what to press to complete this thread.
At the first window, find the row with the inscription "HKEY_LOCAL_MACHINE" and click on the trikutnica icon next to it:

The list below will flare up next to you. There you need to know the “SOFTWARE” row and also click on the jersey:

Don’t worry about the lists there, they’re too big, don’t forget about the bottom line - break it down so you can complete the entries again.
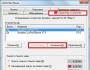
If you go to Winlogon in this manner, you are already pressing not on the trikutnik of evil, but on the word Winlogon itself. After this, shift your gaze to the right panel, you will need to check the parameters: “Shell” and “Userinit” (If you can see it badly, click on the picture - it will get bigger):

I'm surprised at the Shell parameter - it has no more meaning than "explorer.exe". Userinit" may look like this: "C:\WINDOW\Ssystem32\userinit.exe," .
For example, after “exe” there is a coma! If there are other values there, we correct them at the destination. To do this, just click on “Shell” or “Userinit” with the right mouse button, click “Change”, and write the required values in the pop-up window.
This, I think, does not pose any special difficulties for you.
Final tasks and actions in case of failure
In some situations, it happens that this is the parameters of the section. Then we have the following section: HKEY_LOCAL_MACHINE / SOFTWARE / Microsoft / Windows NT / CurrentVersion / Image File Execution Options and it will be lit. If explorer.exe appears there, it will be removed without regret. Well, we have saved everything in order to unblock our “tangle.”
Now you can restart your computer. Since the virus is no longer approachable, everything may return to its place. If so, then we can laugh in grief - SMS - cheers. Well, it’s imperative that after all the work, you need to perform a new antivirus scan. It’s not a good idea to walk through a cleaner before using it - like CCleaner.
Since nothing helped, because you don’t dare to describe the whole thing, you’ll go crazy. Ale SMS, do not force it at all times. You can also learn about other methods of unblocking the Trojan Winlock Virus on the VirusStop website or on the Kaspersky website.
That's all. Now you know how to unlock your computer without SMS. It would be better if you didn’t need someone to work on your computer.
Hello, my readers! It’s unlikely that the average user of the Windows operating system can be incentivized to spend pennies on the help of the cheap Winlock Trojans, better known to people as “Windows blockers.”
And it’s not surprising, even if there were other uninformed traders who ignored the importance of the safety of their computer, automatically adding themselves to the long list of swindlers who, as practice shows, can easily “cheat for pennies” from scammed and ruined newcomers How to not know how to react for a similar situation.
This is why they ask: how can you avoid becoming a victim of deception? And what should I do if Windows is blocked? I advise you to carefully read the lower material, which guarantees that you will avoid the problem of bear clicks.
Why does it all begin?
As if in the evening, when you look at different sites on the Internet, reading the news page, your computer may freeze. And in the center of the screen, a greedy banner may appear that overshadows the entire desktop and asks you to send an SMS (as, obviously, not without cost) or ask you to renew the instructions on your mobile number. Otherwise, all materials from the computer will be automatically deleted.
I will give you a lot of listening pleasures to work, like blocking Windows and asking for a code. I will provide the best options for unblocking the system.
Without any qualms
Fortunately, for some Trojans you can easily select an unlock code, whichever you want, otherwise the virus will be removed from the system.
You can select the required code using any of the available anti-virus databases (and more specifically, you can find the key data on the main pages).
Windows unlocking service available from the company:
- "Doctor Web"
- « Kaspersky Lab»
Open the required page at the drop-down if your system is locked, you can use any other PC, tablet or phone.
Important! Once you have unlocked access to the system, do not proceed immediately. The next step is to check the disk with the help of an antivirus program.
System upgrade
First of all, go to the complex and cunning methods of special software, try to root out the problem using obvious methods at hand, and more precisely, call the dispatcher in a special way for you (use Ctrl+alt+Del).
Why? Then, you see on the right from the intersectional and simple Trojan, which can be easily seen and quickly.
- The list of processes shows a suspicious third-party process.
- Primus completes this.
An example of what your virus looks like.
Most often, the third-party process has an invisible name and appears without description. Find them on the list and finish them off. Raju works completely and consistently until the banner disappears.
If it doesn’t work out, and the task manager doesn’t respond, then I suggest you go to the stage of using a third-party process manager Explorer.exe, which can be done for you. The program can be launched using the additional command “Viconati” (printed Win+R).
In the explorer.exe directive, a suspicious process can be detected very easily.

Military strategy
Another way to get rid of a virus is to use several standard programs, such as Notepad or Wordpad.
For what you need to “naoslip” (either close or grab the banner, you won’t leave yet) you will need:
- Run the Viconati utility (Win+R)
- Write “notepad” in it and click on the “Enter” key.
- Ideally, a new text file will be launched under the banner window, in which you will type whatever (it doesn’t matter what) text and press the “Enable Live” button on the system unit.
- Then all the processes running in the system will begin to end, except for the notepad, which will ask you to “save” or “close without saving” the document (which we, of course, can still delete without changes).
- After deactivating the virus, as in the previous method, find a place to remove the Trojan and find it.
More inserted method
For hacker viruses, “unrealistically complex” Trojans, the method of preventing the task manager or other system components will not help.
Now, it’s time to move on to important artillery, or rather to safe mode.
Pokrokov's instructions:
- We restart the computer, and at the time the operating system is restored, press the F8 key (another button that belongs to your PC).
- In the new window (which transfers the choice of the mode of attraction), select “Safe mode + command row”.
- After opening the command line, type regedit, press Enter and launch the registry editor.
- We analyze the registry editor of running programs on a PC.
For everything, you will get a new way to the Trojan files that have been downloaded from the Shell key and from the Userinit glc. In "Shell" the virus is registered instead of explorer.exe, and in "Userite" the instructions after the coma. - It is copied outside of the virus to the clipboard.
- Enter del in the command line, press the spacebar and use the right mouse button to click on the context menu.
- In the menu window, select the “Insert” command and press Enter.
Voila, the first Trojan file has been successfully deleted. We carry out a similar operation with other and offensive ones (as such).
Well, that’s all, the main ways to update access to the data that I have registered. Since everything described in this situation is difficult for you through ignorance and fear of making things even worse, I recommend that you take the initial course “ computer genius" We will help you gain courage and learn the basics of PC training.
I hope that now I can be calm for you and for saving your information. It is obligatory to share this valuable information with friends on social media. between the lines, melodiously, this material will also be pre-verbal. Don't forget to pay for blog updates and install a reliable antivirus! Until new zustrich!
Thank you! Abdulin Ruslan
As a rule, this is a Trojan from the Winlock family. It’s easy to identify: whenever an image of a pornographic or business nature appears on the screen, and in which the computer responds to commands, that’s our client.
The banner often displays the message “Your computer is blocked” and offers the option to send a paid SMS or deposit money into the deposit boxes, but after this, the bad banner (and with it the blocking of the PC) is no longer known. In the image there is a field where you need to enter a special code that may come after the withdrawal of valuables. The principle of operation of such useless elements comes down to replacing the Shell parameters in the operating system shell and eliminating the functions of the Windows Explorer
There are several generations of viruses. Some of them can be completed in a couple of clicks, while others require serious manipulations. We will show you the ways in which you can fight against any Trojan of this kind.
Method No. 1
Dispatcher
This method works against primitive Trojans. Try clicking on the primary task manager (key combination CTRL+ALT+DEL or CTRL+SHIFT+ESC). If you want to, find out at the flow of processes those that are innocently running, and finish them.
If the dispatcher does not call, you can quickly access the process manager using the Win + R keys. In the "Open" field, enter the word "notepad" and press ENTER - this way you will open the Notepad program. In the program window, type additional characters and briefly press the open/close button on your laptop or desktop PC. All processes, malware, and Trojan, will end immediately, otherwise the computer will not turn on. While the virus is deactivated, you can find files that are related to the new one, and liquidate them or stop checking them with an antivirus.
If you have not managed to install an anti-virus software, you are asking: how to remove a virus from your computer? Most often, the evil Winlock family sneaks into the directories of either time-clock files or browser time-clock files. In front of us, turn the tables:
C:\Documents and Settings\directory in which the name of the accountant is entered\that
C:\Users\directory for the user's name\AppData\Roaming\.
There, search for "ms.exe", as well as suspected files with a sufficient set of characters on the command "0.277949.exe" or "Hhcqcx.exe" and delete them.
Method No. 2
Deleting virus files in safe mode
If the first method is not blocked and Windows is blocked - what should you do in such a situation? It’s also not a good idea to get embarrassed here. Well, we stumbled across a Trojan that replaces system components and blocks the launch of the Task Manager.
In this case we have to select the robot in safe mode. Restore your computer. Before Windows starts, press F8. From the menu, select “Safe mode with command line support.”
Then write in the console: explorer and press ENTER - you will launch Explorer. After this, the word “regedit” is written in the command line and ENTER is re-embossed. This is how we contact the registry editor. You will be able to find out the records created by the trojan, and also in the same place, your autorun will be detected.
The paths to the files of the malicious component will be, most likely, in the Shell and Userinit keys (in the first one, explorer.exe is registered, and in Userinit it is easy to identify this one). Next, the procedure is as follows: copy the external name of the detected virus file with the right button to the clipboard, write “del” in the command line, then put a space and paste the copied name. ENTER – and you’re ready. Now you know how to remove the virus-virus.
The same applies to the threat of infectious files.
Method No. 3
System upgrade
Let's start the system in safe mode, as described above. In the command line we write: “C:WINDOWSsystem32Restorestrui.exe”. Current versions are understandable and simply rstrui. Well, of course, ENTER.
The “System Update” window will appear in front of you. Here you will need to select the update point, or more precisely, the date that transmitted the virus to the PC. It could be yesterday, or it could be a month ago. In a word, choose the hour when your computer is 100% clean and healthy. Axis and all unlocked Windows.
Method No. 4.
Emergency disk
This method means that you can download software from another computer or go to a friend for it. Would you like, perhaps, you have already acquired it in amusement?
A special security program for emergency cleaning and system updating with a wealth of packages is supplied directly in anti-virus packages. However, the emergency disk can be downloaded securely - cost-free and without registration.
You can download ESET NOD32 LiveCD, Comodo Rescue Disk or . All these programs follow the same principle and can be placed on CDs, DVDs, or USB drives. They automatically install an integrated OS (usually Linux), block the startup of Windows and, apparently, unwanted elements, scan your computer for viruses, remove unsafe software, and scan for infected files.
The famous Winlock blocker has not been sleeping for a long time, it’s been almost seven years since the “blackmailing” koristuvachs. Today, the representative of the Trojans has achieved clear success - evolution is obvious. Corrupt workers spend at least an hour fighting the virus, and often end up with financial losses. Well, let's face it, there were already a lot of ways to help unlock the system without much fuss. Read on to learn how to unlock Windows 7 independently and absolutely cost-free, and also show respect for the possibility of avoiding this unpleasant moment.
Where can you “underwrite” a Trojan and how does it work?
In fact, any hacker can actually acquire the virus and launch it on his own. The Trojan can sit on any picture or video file. If you are downloading a file from an unknown site, pay attention to the extensions. The standard extension of the representative of the Winlock family of Trojans is .exe. When you start the virus, the active Windows infection phase begins. Koristuvach may not immediately mark the changes, but the Trojan will immediately register in the auto-recorder, and then intersect actions that can create a koristuvach. People can continue to chew on the “wool” of the page if the banner appears on the entire screen and completely blocks the robot. Shut it down or it will burn hard. The images may be of a pornographic nature, or they may be violent, brutally brutalizing the law. I will be obligated to pay a fine or send a payment notification to the registration number. For everything, the Trojan imposes a fine and threatens the consequences of being ignored. Of course, after payment you won’t be told anything, and, of course, you won’t be able to do anything. You should immediately contact the given number and find out about the connection with the mobile operator, then contact your security service. There are problems when the operator immediately dictates the unlocking password, but it’s never that easy.
To unlock the system, you need to remove the virus from auto-recovery and then delete it. There are many ways to earn money.
Diagnosable unlock code
Some antivirus programs can indeed provide a code to unblock windows. After this entry, the Trojans nobly appear in the upper field, and the literal meaning of the word. Never mind, of course. You can find out about this code on antivirus websites. Everything is simple here - enter the instructions on the banner or the phone number to which you are asked to send an SMS, and select a combination of passwords and other entries. You can access the site from another PC or phone.
If you still manage to patch up the Trojan in this way, do not shake your computer after work! Please thoroughly scan your windows for viruses.
Self-correcting
Do not rush to connect additional utilities and click on the master. Try another method. It is necessary to call the dispatcher by pressing CTRL, ALT, DEL or CTRL, SHIFT, ESC. Since it was clear that the problem is not that big. This program is detected during active processes and is deleted. It’s not difficult to find out - most often the lock is suspiciously signed, and the description of the programs is completely daily. If you are in doubt, just finish all unintelligible programs until you see the banner.

Since the operation did not go as smoothly as we would have liked, and the dispatcher, not allowing himself to please his presence, will make another attempt to call him. Vikorist the command "Viconati", you can launch it by pressing Win + R.
The primary location of the blocker is the directories of time-clock files in windows and browsers. However, a Trojan can attack copies, so a full check of the system is still necessary.
Another way to remove a simple Trojan
You can get rid of the Trojan (advertising image, for example) by being respectful of the reaction of your programs. For example, having marked the banner, open WordPad or notepad, press win - r and type notepad.
A new text document will appear in front of you, enter some characters and turn on the computer using the Live button. This will cause the termination of all active tasks, such as a virus, so that your PC can continue to function.
You will be deprived of the option of saving or changing your account, now you have entered the banner in a streaming session, which allows you to get in trouble with the virus.
There are more persistent types of Trojan
These Trojans have a strong immunity until they try to protect it. The virus is persistent and blocks any actions, for example, the task manager does not start or it is necessary to replace important components in Windows. In this situation, you will no longer have to restart your PC; press F8 when you wake up. You will see a window with possible options for turning on the system; you need to select row 3. Then write “explorer”, confirm, and then launch the explorer. Next, type regedit and press enter again, you will note the registry editor, which will help you identify the Trojan and tell you to automatically launch the virus.

For everything, you will see the whole way to the virus in the root “shell” and “userinit”. At the root "shell" the Trojan will be in the row instead of explorer.exe, at the "userinit" there will be prescriptions after the coma. Once you know the facts, export the virus name to the buffer exchange by typing del in the command line, pressing the space bar, and right-clicking the mouse to open the menu. Inserts the video and embossed confirmation (enter). Then you remove one virus after another, and so on until it is possible.
The next logical step would be to check the registry for viruses that have been lost, and search for the Trojan. All suspected files are immediately obvious, then make all copies of the created files and folders, and then clean out the folder.
To be on the safe side, use an antivirus and be sure to check any skin patches on your system. It is possible that due to the activity of the virus, the adjustment of the intermediate connection has been disrupted, you can identify them by additionally adjusting the “Windows Sockets API” with the “AVZ” program.
Ground contamination system

In the case of ground-infected windows, it is practical to use a quick spray to correct the problem. A more productive and effective method is to launch a clean system and remove the main one. There are literally no options for this process, but one of the most effective ways is to use a third-party program that is based on Gentoo Linux. There are a number of main file images that are created by burning to disk, or by creating a backup file on a flash drive using the additional program “Kaspersky USB Rescue Disc Maker”.
When you turn on the infected PC, press the appropriate key to enter the BIOS, most often using the F2 or Del button. In settings, select a file and save it by pressing the “F12” key. Current BIOS versions allow you to select hardware devices that do not require basic setup. Just press "F11" or "F12". Immediately after restarting, Kaspersry Rescue Disc will start. The operation transfers automatically or manually to your choice.
See additional threats on the installation disk
The group of Trojans appears to be targeting the MBR system, as you can see in the automatic launch slots. At the initial stage of virus recovery, it is necessary to update the initial MBR password. For Windows XP, this operation is carried out using the additional installation disk, pressing the “R” key, clicking on the update menu and entering “fixmbr” in it, after which the additional “Y” button is used, and finally re-installation. For Windows 7, the same process is followed by BOOTREC.EXE, enter bootrec.exe/Mbr. Thus, you launch Windows and you can find infected files using an additional antivirus.
Work with less productive PCs
On low-security PCs and laptops, the process of updating Windows is a little longer and more complicated. It is explained that there is no difficulty and difficulty in turning over external disks. Effective solutions include removing the infected hard drive and connecting it to another larger PC. It is recommended to use boxes with an eSATA or USB3.0/2.0 interface. To prevent widespread viruses, it is better to enable automatic startup of the HDD on your other PC, which can be done using the additional AVZ program. It is better to use other programs to perform the verification. We go to the menu “Meister search and solve problems”, select "system problems", “All” and press Start. Select an item “HDD autostart permissions” and we correct everything as planned. Before launching the infected device, you must re-convert to ensure that the entire anti-virus database works without interruptions or gaps, so be sure to take this seriously.
If the disk partitions are not detected, execute the following operation: “Start”, “Viscont”, enter and confirm. After this, the sections of the hard drive will be marked with letters.

To prevent the system from becoming infected again, install a good antivirus that requires regular checks. The basic rules of care can be called:
- Koristuvannya PC with shared rights
- It is necessary to check the browsers with a fire protection system
- Vim the Java script of unknown sites
- Mittevo have fun with leaking advertising windows
- Separate disks into personal and system files
- Insert autorun flash drive.
If you need to update your PC in a short period of time, it is recommended to use the following utilities: Symantec Ghost, Acronis True Image, Paragon Backup and Recovery.