Nashtuvannya comodo 5.12 firewall for maximum zakhistu. Installed and adjusted programs (look around): firewall (firewall) Comodo Firewall (completed). Context menu extension
The main firewall modes for advanced settings are: Set rules, if for all programs that do not have a border rule, you will be blamed, and Safe mode, if trusted programs for locking are allowed to close. Reporting the order of stosuvannya rules. Dodatkovі, malovikoristovuvanі modes: More blocking, if pripinyaєka be-like merezhna aktivnіstі, nezalezhno vіd rules, that mode navchannya, if yakі zadnannya are allowed that automatically svoryuyuyutsya allowed rules.
The option "Create rules for safe programs" is punished in "Safe mode" not only to allow regular activity to trusted programs, but also to automatically create rules for them. I do not recommend including, like i . This option does not apply to the robot in the “Setting the rules of the koristuvach” mode.
If the option "Don't show alerts" is set, then the alert will be set to the selected action: split building or blocking. New rules don't work for anyone. I recommend setting the mode "Do not show alerts: Block water" after setting all the necessary rules.
As if in case of confirmation of the commencement, in the new option “Remember my choice”, then the rule will be created. The "Alert frequency equal" option is set, but we will go into more detail as a rule. If, for example, set the rіven "Duze low", then the rule is permissible or defensible in the case of any kind of activity. I recommend the “Duzhe high” rіven: the same rule is to set the IP address and port.
If the option "Automatically display private measures" on the tab "Zones" is marked, then when connected to new lines z'appear, scho proponuє vzazati її status. What happens when new entry the list of border zones, and if you select the status of “home” or “working” borders, the allowed rules will also be created for it. As soon as the option “Do not show notifications, if you are connected to the Internet...” is enabled, then new records about the area limits and allow rules for them will be created automatically, without notification. I recommend including offending options: at times, the connection will be made without notification and creation of new rules, that is. merezha will be taken as “suspіlna”.
When connected to unprotected Wi-Fi Merezhi Blame the warnings for the proposition of being a paid service Trustconnect. The display of these alerts is mimicked as a separate option.
In order to control the loopback in the middle of the computer (for example, to block the access to the Internet through a local proxy server), you need to check the option "Enable loopback traffic filtering" (recommended).
To control the traffic for the IP protocol version not only IPv4, but also IPv6, set the option “Enable IPv6 traffic filtering” (recommended).
The option "Block fragmentation of IP traffic" protects against an attack based on the forwarded TCP packet, the fragmented layer is strong, so it is not possible to determine the header that belongs to the TCP session. I recommend you take a look.
The option “Analyze the protocol” orders the skin packet to be checked for compliance with the protocol standards, the updated packets are blocked. I recommend you take a look.
Here, the "Enable ARP spoofing spoofing" option protects the ARP table from being changed by an attacker, which controls the "mimic ARP spoofing" (spoofing without prompting). I recommend you take a look.
The creation of firewall rules
Addendum rules
The usual order for creating a rule for a program is:
- open the "Rules for programs" tab, click "Add";
- Please enter a program, can you please different ways:
- squeeze Looking around → Filey then select a file;
- squeeze Look around → Running processes ta vibrati appendage;
- squeeze looking around choose a group of files;
- directly in the field "Im'ya" enter the way (otherwise a template from different characters * and? that changeable medium);
- set the rules:
- or click on “Victory set of rules” and select the required set from the list;
- or press “Vykoristovuvaty vlasny set of rules” and add vlasny rules (you can copy any type of set);
- Press "OK" and sort out the rules for the programs using the "Up"/"Down" buttons.
When adding a free rule, it is necessary to indicate:
- dіyu: “Permit”, “Block”, or “Power”;
- straight: entry (tobto іnіtsiyovany vіddaleno), vyhіdniy (tobto іnіtsіyovaniya na this computer) or be it;
- description: text that represents the rule; if you do not specify, then the list of rules will be displayed report description;
- to the address of dispatch and the address of recognition;
- protocol:
- IP, you will be able to specify the protocol on the “IP Details” tab;
- ICMP, at this option on the "ICMP details" tab you can specify the type of ICMP notification;
- TCP and/or UDP, in which case you can set the dzherela port and the port of recognition;
- option to register merezhevu activity in the journal.
I will designate that as the address of the managed/assigned address, you can act not only as a single IP address, but also as a zone, and anonymous other objects, and you can also invert the selection of the “Turn off” option. Similarly, dzherela/appointed ports can have a set of ports, zokrema. inverted. Next check that the address for holiday- ce "Addresses of recognition", and the distance for the entrance - ce "Addresses of the administration"; similarly to ports. To that, in a flash of seeming, one hour he allowed the incoming and outgoing days to be like a remote node, two rules are set:
- one rule allows entry from a remote node to any address;
- Otherwise, allow you to leave any address at the same distant university.
When given a set of s kіlkoh rules, they should be ordered їх s looking at those that may have priority, as a rule, more.
Global rules
Global rules override local computer activity, and global rules may take precedence over addendum rules. Fences, set in global rules, effective, lower in addendum rules. Zocrema, globally attached ports to make the computer invisible when trying to scan.
Established sets of global rules. Interface switching between views as a choice for the visibility mode of a computer in a group: Block entrances or Notify about entrances ( Golovne vіkno → Manager → Firewall manager → Take porti).

Vibіr mode "Inform about the entrances" znіmaє global fence vhіdnih zadnaє and put further control on the rules of the program. However, bezpechnіshe all the same allow entry only on the songs to spoil and / or from the song lines, and otherwise block. So, the screenshot shows the global rules with the minimum quota of inputs, necessary only for ping-request requests. local lines, to allow access from it to files, the bachelor name of the measure sharpened for the robotic torrent client.

The creation of their own light rules viroblyaetsya similarly , vіdrіznyаієsya vіdsutnіstyu vіdustnіstyu infusion "Zapitati".
Groups of files, divisions of zones, sets of ports and sets of rules
You can speed up anonymous operations of the same type and achieve the best representation of the rules, thus creating your own groups of files, partitions of zones, sets of ports and your own sets of rules.
Groups of files are formed on tabs File rating → File groups, named sets of ways in their templates with different substitution symbols * i? that zminnih middle. For example, it allows you to create rules for the robotic auto-updating of the Flash player or Java, so that during these processes the file names are changed and the names are changed, which are created at the same time. It is possible to specify templates of names without different groups of files, however, the groups override the signs of sharpness, compactness, and also the possibility of denoting a foreign genus at the same time in different components of zakhistu. For example, you can create a "NoInternet" group, which will immediately block the internet connection, DNS requests, BITS service call, browser launch and memory access.
On the “Set of Rules” tab, you can check how the rules are set in the firewall policies, as well as change the policies or create the power. You can then assign these policies to add-ons: through the “Add-ons Rules” tab or through firewall alerts. I will designate that in the notifications only those policies are promoted, in which an unambiguous decision is made for the measure activity: I allowed or the fence. For example, if the program tries to reach the web server on port 80, then the policy will not be requested in the notification. Postal client”, but the “Web browser”, “FTP-client” and “in” policies will be.
On the "Sets of Ports" tab, you can group a combination of ports into a set of names, so that you can then select it in the rules as a port of management or recognition. When folding sets, you can combine single ports, ranges of ports, as well as their inversions.
The “Zone Zones” tab has the following special features: on it you can not only group addresses in the “zones” name for their subtly different names in the rules (like the addresses are corrected or recognized), but you can also set the status of these zones. So, if you create a zone, and then add it to the “Zone Blocked” tab, all the connections with it will be blocked, regardless of the rules. In addition, the Merezha zone can be recognized with the status of Merezha access».
The order of setting firewall rules
When the activity is detected, the merezhі spochatka is checked to see if the address lies far away. If you lie down, then z'ednannya be blocked. Yakshcho ni - pochinaetsya look global rules.
The global rules are viewed from the bottom to the bottom. As for the incited view of the blocking, the first rule is the blocking rule, blocking be harrowed. As a rule, you should not know the first rule, but the first rule is allowed - it starts looking rules for supplements.
If the program needs to install restrictions (permitted by global rules), the list of addenda and rules for them is visible to the beast down. At the first known zbіgu (so if you get mad given program Otherwise, a group of programs that retaliate, and inquiring the type of attack) is determined by, is assigned in the rules: allow, block or show alert(if the option “Do not show alerts” is enabled in the settings, then the alerts will be checked for, it is set in this option: split building or blocking).
If the list of firewall rules does not contain a valid one, then the entry will be automatically allowed in such situations:
- if the firewall works in the “Startup Mode” (in which case the rule can be created);
- if the option "Don't show alerts: Allow to ask" is enabled;
- if the firewall is running in "Safe Mode", the option "Do not show alerts" is disabled, and the program is trusted to be checked off the real medium;
- if the firewall works in "Safe mode", the program is trusted and vikonuetsya in a real environment, and zadnannya, scho zaptuetsya outside.
In other cases, the alert is blamed, or, as the option “Do not show alert: Block the drink” is marked, it is blocked.
Zocrema, I'll designate that the programs that are installed virtually are controlled by the firewall regardless of their rating. So, if you want to use the firewall in the "Safe Mode", you need to create the allowed rules to be protected by browsers.
You can respect that the firewall does something illogically for the "Safe Mode" entry z'ednannya trusted programs Mabut, tse bug.
Access to local resources
Behind the rules of the firewall, the firewall was allowed to remove information about the border, allowing local access to files and so on. If you don't need it, it's possible to use a network of vikoristovuetsya only for access to the Internet.
The status of "trusted measure"
Allowed for the local merezhі in the simplest way to create a recognized status of "trusted". You can work in different ways.
As the option “Automatically display new private measures” on the “Merezhniy zones” tab is highlighted, then when connecting to a new fence, you will receive an alert, in which case you need to indicate your nationality. The status "trusted" is assigned by choosing the options "at home" or "on the job". I have created a set of global rules before setting up a bet, which allow whether there are holidays or whether there are entrances with a network of fences, such as similar rules for the System process (“System”). When choosing the option "in community» New rules don't work.

As soon as new tacks were revealed, the tacks were previously recognized as “suspended”, following the “Management of treads” window ( Golovne vikno → Manager → Firewall manager), mark the item "Trust the measure" and press "Ok". The result will be similar to the front.
In order to turn the neutral status of the measure, simply select the “Block the measure” item in the “Manage the measure” window, and then, in the window, open the tab Merezhevі zones → Blocked zones that vidality given merezh call.
Є Bug: if a fence zone is not created for the active fence and in fact the fence is processed as “suspended”, then the window “Management of fences” will show the status of “trusted” for the fence.

Respect! As soon as you press the “Ok” button in such a way, then the measure will be active and rightly “trusted” to you. a new entry will appear in the list of merging zones and the firewall rules will be created that allow the merging zones to be opened. If you do not need to check the borders, then close the "Management of borders" window with the "Checkout" button.
The butt is allowed for access to the local border
It is possible to establish trust in local borders only in the first place and in full security. To that it is recommended to recognize neutral status (community space), turn it on, and then add the necessary permission. Ring for access to border resources necessary, in addition to the obvious rules, allow Process System("System") next incoming order (abbreviated "addresses of the office" - local border):
- UDP communication with gerel port 137 and recognition port 137: to be able to reach computers with NetBIOS names;
- UDP communication with dzherela port 138 and recognition port 138: schob bachiti border;
- TCP connection over port 445: Authorizes general access to files.
So, when creating the rules, select "System" as a program, it is necessary to select it from running processes.
All qi were allowed to be dubbed according to the global rules. Also, they have the following allow ICMPv4 logins, which are controlled from the local network with the help of "request-request"; It is not necessary only for the possibility of pinging a ping-request, but for providing a secure access to files. An example of a set of global rules.
Firewall Features
The Comodo firewall does not control loopback entry (but only exit control). So, if the local proxy is different, it is sufficient to allow only access to the Internet for the proxy server and access to "localhost" for the browser (although many other firewalls can still allow access to "localhost" for the proxy server).
Ownership ruled: as indicated by the rules as the address domain name, then CIS will know the minimum and maximum IP-addresses for this name, and then all the intermediate IPs will be considered valid.
The peculiarity of the version of CIS 10, which can be called goodness, began to show the dependence of ICMP traffic on various add-ons. Many versions of CIS (and, for example, Windows Firewall) have taken all the traffic that the System.
Content filter
The "Content-filter" component blocks access to websites for their addresses. To ensure the security of the address, the lists of Comodo are updated, and you can also set the lists of the koristuvach. If you try to check the fences, the site of the koristuvach should be added to the side with information about the blocking, as well as, fallow in the case of the installation, from the proposition of Timchasovo and ignore the fence, or put the whole site at the blame.
Categories. Import lists of koristuvach
Lists of addresses or їх (what are the symbols * ta?) are called categories. Comodo's top categories are "Safe Sites", "Phishing Sites" and "Shky Sites". The stench is updated automatically, it's impossible to look over and change. Other categories - available for changing the content - are set on the "Content filter" > "Categories" tab. In the beginning there is the category "Disabled", before it is taken down by sites that are disabled from blocking through notifications in the browser.
It is possible to add categories to the lists of shkіdlivih sites from іnshih gerel. Recommended lists are those of Symantec WebSecurity. For the rest of the trail, visit the MalwarePatrol website.
To create a supplementary list, go to the "Categories" tab through the context menu to create a new empty category, and then import the list from the file. When selecting a file, it is necessary to specify the format to the list, otherwise the content filter is incorrect ( typical pardon koristuvachiv).

Format of entries in content filter categories
The record looks at the template and hoards the addresses that I will repeat to this template. For example, the *.example.com entry matches http://test.example.com , not http://test.example.com/404 and not http://example.com .
The entry without the substitution symbols is identical to the pattern taken from the end character * . For example, the records https://example.com and https://example.com* are identical, they match the addresses https://example.com, https://example.com/404 and https://example..example .com. In this rank, the record is like a domain name for the site, and it also catalogs, but not a subdomain.
Set the HTTP protocol for the content filter daytime protocol. For example, records of the form example.com provide the address http://example.com rather than https://example.com . Entries like example.com/* matches http://example.com/404. Respect! The addresses http://example.com are valid for the records http*example.com* and */example.com* , then. scho vengeance if only part of the vkazіvki protocol.
The HTTPS protocol is indicated explicitly, but behind additional templates. For example, https://example.com entries match the addresses https://example.com , https://example.com/404 and so on. *//example.com entries match https://example.com rather than http://example.com or https://example.com/404.
Needless to say, the blocking of HTTPS-sides by the content filter can be done without warning about the blocking of the fence. Moreover, blocking HTTPS-sides may not work, it's still in the browser.
Oh, let's say it is necessary to block the site example.com one hour for HTTP protocols and HTTPS, with directories, but without subdomains. In order to collect the most “precisely”, it is included in category 4 of the entry that is blocked:
- example.com?
- example.com/*
- https://example.com?
- https://example.com/*
(Substitute of the sign? The replacement of any letter will be like the symbol * until the end of the row.)
As an option, you can get by with a single entry like *example.com*, or else blocking not only necessary addresses, but also https://www.example.com/404, https://myexample..common.html.
Content filter rules
It is a rule of thumb for the content filter to sweep the list of categories, until such time as they are blocked, that list of coristuvachiv or їх groups from the designated їх obmezhen. Interface change the list of obvious categories.

Koristuvachі those їх groups are added through the context menu at the field "Obmezhennya": "Add" > "Dodatkovo..." > "Types of objects" > select all > "Ok" > "Poshuk" > select required entry> OK.
Sound the victorious group "All". How well it is necessary to set a different exchange life koristuvacham, next obov'yaskovo kazati obmezhennya for dermal z them. Otherwise, it is not included that the coristuvach, which is not subject to the rules, will deny access to sites from the overridden categories to the list for the presence of another confining rule.
Applicable to Windows 8 and higher in the skin rule to the list of koristuvachiv next add the entry "ALL APPLICATION PACKAGES" with the same exchanges as for koristuvachiv. Otherwise blocking will not work for Internet Explorer 11.
For correct work For the blame of blocking, the rule “Allowed sites” can be changed more than the rule “Blocked sites”.
As it seems, the policy is normal, only the axis of the product is paid and after 30 days, stop working, ask for a penny. Say, and є є kishtovny faєrvol such a quality.
Hello friends! Today's article about the popular and cost-free firewall Comodo Firewall.
Popularity on the market of software zahisne software from the company-retailer Comodo Group has gained popularity in software products three important warehouses - the scope of zastosuvannya is demanded, simplicity and clarity of the interface, as well as cost-free rozpovsyudzhennya. Okremo varto signifies the flexibility of the approach of retailers. So, software package for the protection of a computer that consists of antivirus, firewall, "Sandbox" and other modules can be installed as a whole, so and vibirkovo, having installed only a few in the system Okremі modules or Comodo AntiVirus antivirus, or Comodo Firewall. The same about the rest of the details below. Let's take a look at the features of the Comodo Firewall, how to install the program and how to fix it.
The main features of Comodo Firewall
Firewall Comodo Firewall, regardless of those that the product is cost-free, secures full protection of the computer from threats. Moreover, Vіn more than once became a facilitator of various tests, which were carried out by Internet software resources with the method of revealing the best software solution for the Firewall class. Comodo Firewall is a building protection against attacks by hackers and a hacky software that can be expanded as often as possible, on a par with paid firewalls such as Outpost Firewall Pro. To put it simply, this kind of quality is more cost-free, You won’t find software on the market.
Comodo Firewall analyzes the suspected activity of programs on the computer and checks all active components, blocking the launch of anything that can harm the computer. Zavdyaki mode Stealth Mode computer becomes invisible for scanning ports shkіdlivim PZ. Comodo Firewall automatically designates the computer's trusted zones, such as folders and files, as authorized for access to the home or local area.
On the face of its counterpart, which lives in one system not with a skin antivirus, Comodo Firewall is more loyal to this plan. If you don't like the specifics or efficiency of the Comodo AntiVirus anti-virus module, you can install any other anti-virus, Comodo Firewall shards sound not conflict with third-party software.
A sprinkling of robotic and gnuchki modes of setting up Comodo Firewall allow you to set up the firewall's behavior like newbies, so well-known koristuvachs.
Installing Comodo Firewall
Launch the Comodo Firewall downloader.

The process of installation is slightly different from the standard one, the shards are handed over from time to time to set the parameters of the robotic programs. After choosing a mov program, it is necessary to check the installation master, where it is necessary to select some options. Your E-Mail is not binding.
It is possible to remove all installed options without changing anything in such situations:
If the language is about a productive computer or a laptop and a high-speed Internet connection;
You basically want to take the fate of a thoroughly zahisty PZ, Comodo's zocrema products, so that the company would improve the zahisty of koristuvachiv;
You do not trust your ISP's DNS.

Check out the options for installing the program, de-rozrobnik, relying on those that you will quickly carry out the installation and do not dig into the installation settings, preparing for the addition to the Comodo Firewall firewall automatic installation of two more client programs technical support from the Comodo GeekBuddy retailer and a browser with a stronger attack when surfing the Comodo Dragon web. Get in touch with the first program no sense tim, who don't know english movie and do not charge after the end of the cost-free period to pay for Comodo technical support. Another program - the Comodo Dragon browser based on Chromium - you can freely download from the Internet and install it at any other convenient moment, if you become aware of changing the browser.

Now you can boldly press the "Forward" button.

In the coming future, we are faced with the installation of Yandex elements along the way and the entire existence of this search engine in the browser. Seemingly, in view of the services, the shards of її can hardly be called a wasted opportunity in life. Click the button to start the installation at the bottom.

The program will install. After the launch, we need to restart the computer. Press the "Correct" button.

Launch Comodo Firewall
The computer is rebooted, and we can see it on the work table with a lot of vicons Comodo Firewall - informational proof about technology Comodo, gadget robotic software and software front lashings firewall, why do we need to tell us, to what extent the computer is connected - to the home, work or office in a large area, for example, with a Wi-Fi access point.

When the Comodo Firewall lights up in the system tray, you can call the program interface sounds.

On a computer, for which firewalls have not yet created a rule, it is necessary to give you a commendation, so, obviously, there is no possibility of an unauthorized launch.

Compliment the launch on the computer of the skin unknown Comodo Firewall program to happen to doti, the firewall docks do not virob for yourself the rules of conduct for the skin program that are launched. Obviously, it’s easy to mess around, but it’s really a small fee for being able to control Mezhezhі connection.
Installed Comodo Firewall
The Comodo Firewall program is covered by a wide range of options, including new ones, and your computer will be safely loaded from the installed retailer settings. Ale for more informing the coristuvachas, sing-songly, bude will triumph over the possibilities of Comodo Firewall for a hard-hitting computer.
Run the firewall for the help of the yogo shortcut in the system tray. Basically, what was seen in front of us was the status of the program - the computer was under attack. Also, there are a number of merging intrusions, a number of blocking intrusions, and software updates.

For help buttons at the left upper codend we can go to the presentation program of the report link. And then we'll turn again until the fermentation in the short link mode.

In the main window of Comodo Firewall there is an option called "Game mode". Igroviy mode - tse, in fact, the multi-screen mode is not only in games, but I will watch the video every other hour, and also in some other programs, which appear on the whole screen. When switching to this firewall mode, we are not turbulent by our notifications and all decisions are taken by ourselves.

In order to increase the expansion of the firewall, in the main Comodo Firewall window, the Firewall was also added to the reporting links.

You will be asked to configure the firewall in detail, where you can change those and other installed settings.

You can, for example, in the upper part of the window, change the settings for the “Safe Mode” of the firewall robot, if the least activity of the programs that are in the list of trusted ones is allowed, and Comodo Firewall does not interfere with the skin drive, in other modes. For example:
"Outside blocking" - in which mode, if any, the activity is turned off. This mode is simply irreplaceable when a computer is infected with a virus.
“Koristuvachsky set of rules” - as you can see from the name of the regime, vin transferring zhorst control that fate of the koristuvach in adopting a decision on how to skin treadmill, for which the rules were set earlier.
"Startup Mode" - Comodo Firewall does not intervene in the activity of programs that are being launched, but only monitor the progress.
Podbag of previous articles: a clear option to improve and compose the Comodo version internet security 8
Respect! The article is addressed to koristuvachs, who may be aware of the situation with the Comodo Internet Security complex, and they read the previous articles about it. "Beginners" are recommended to drink the product forward. In order to understand that effective choice, the following procedure is suggested:
- connect the computer to the Internet and/or local networks;
- install CIS;
- vіdkriti "Golovne vіkno" > "Zavdannya" > "Expanded zavdannya" > "Expanded nalashtuvannya";
- on tab " Zagalne nalashtuvannya» > "Configuration" robite subway click on the Proactive Security row;
- on the tab "Zahist+" > "Sandbox" > "Auto-Sandbox" uncheck the option "Write Auto-Sandbox";
- on the tab "HIPS" > "Protection of objects" > "Protection of files" through the context menu, add any file;
- through the context menu, replace the input row with ?:\*
- press "OK" to close the opening window;
- vіdkriti "Golovne vіkno" > "Zavdannya" > "Firewall manager" > "Pick up porti";
- select the option "Block the entrance";
- vikonati revantazhennya;
- connect the computer to the measure.
Forward respect
This order of nalashtuvannya should be imposed on a quick look. Meta stats - to give readers a guide to the versatility of Comodo Internet Security's configuration options. It is suggested that readers know about the previous articles and understand the reasons for other recommendations. Here, only the most important details are given. About add-ons, for example, against bypassing the firewall (through cross-process access to memory, DNS-request and BITS), protection from cryptographic servers or keyboard shortcuts is described in the article about the replacement of proactive protection; about access to the local network - in the article about the firewall, etc.
I substantiate that this configuration is not “maximum”, but more or less balanced, more or less balanced, and more victorious. Unknown programs in it automatically virtualize without delay. HIPS alerts are possible, but the stink is rarely blamed.
Proposing a variant of appointments for special zastosuvannya dosvіdchenny koristuvach, but it is not important to adapt yogo for "novices" or koristuvachіv with obmezhennye rights. You can, for example, disable all notifications, or replace the automatic virtualization of unknown programs blocking, or switch the firewall to Safe mode, etc.
As if the following instructions were brought up to some problems, I ask the readers to help in the comments. Information is provided, attached with files to the configuration export, the list of files and CIS skin magazine for the entire period, as well as video recording and/or data remote access for diagnostics
Installed and fixed
Installed
Bazhano install CIS on the system, which is guaranteed not to miss shkіdlivih programs. I’ll guess what is needed to update the system and work backup copy. May sens forward enable "Windows Firewall" through the "Control Panel".
Since the system is clean in the case of shkіdlivih programs, it is necessary to recognize the CIS files on it. To avoid conflicts, for the whole hour you can turn on the protection components: antivirus, Auto-Sandbox, HIPS, firewall and Viruscope. "Reputation scanning" ("Headline" > "Zavdannya" > "Zagalnі zavdannya" > "Scanuvannya") and after that, all files were found to be trusted. Let's start with the launch of various installed programs and their components. Vikonaєmo perekantazhennya. In the extended setting, on the "File reputation" > "File list" tab, all files are visible and through the context menu you can set the trust rating.
Basic setup
After setting up, check the tab "High Settings" > "Configuration" in the window of advanced settings, and select the "Proactive Security" configuration. On the proposition of re-advancement, vіdpovimo "Vіdklasti".
As before, CIS was created, it is imported from the program catalog with the “Proactive Security” configuration under other names that is activated.
As soon as there is a message about the choice of the status of the border - the choice is the option of Hromadske Mіsce.
On the “Content filter” > “Rules” tab, we reconsider that the “Blocked sites” rule is unchecked at the bottom, and change it: add the category “MVPS Hosts list” and “Symantec WebSecurity” and set the type of border not “Block”, but “Power » ».
Context menu extension
To copy files blocked by the antivirus, add a special item context menu. The information required for this material with instructions is filed in the archives.
Vikoristannya
When the unknown programs are revealed, it is not timidly to be weakened by the zahist, not having changed at the її bezpetsі. The easiest way is to change the program through the context menu. I see that the use of antiviruses is not an absolute guarantee of security. Ale, you can more or less judge the security of the file, as long as you have known it for a long time and conducted antiviruses do not recognize it.
As an addendum, you can run an unknown program in virtual environment, and then add it to VirusTotal instead of the VTRoot directory. You can independently continue the behavior of the program in the virtual environment by turning on Viruscope with the option “Stop Viruscope only to the Sandbox program” and displaying a call about activity. Also Viruscope automatically qualifies the program's behavior as a speed limit.
To install a new safe program, click on the pressed Shift key, on the installer context menu, select the "Run as installer" item. As well as the hour of setting the HIPS vinikne alert, it is possible to enable the new option “Remember your selections” and select the “Set or update” policy. After the installation of the program, it is necessary to perform the first trial run through the context menu item "Run as an installer without privileges" and then close the program. Let's go to the tab "Reputation of files" > "List of files" translating unknown files of the program in trust. Also, if you trust, we add a catalog from the new program.
For an update installed software it is launched by the context menu item “Run as installer”, we will follow the update procedure and similarly transfer new files from unknown to trusted.
The situation is possible, if the program is launched in isolation after entering the trust. As a rule, it is necessary if the program expands 40 MB. Solution - add a path to such a program to the AllowedProgs group.
If so, the program needs to be run at the same time without borders, click on it, pressing Shift , then the context menu selects the item “Run as an installer without changing rights.” It is important to remember that such a program and її child processes can run a file without any interruption.
If there is any ignorance of the file beforehand, it is isolated for the help of Auto-Sandbox, it will be announced. I’m guessing that it’s not safe to press the button “Don’t isolate anymore” on the new one.
As if it were a given, as a matter of fact, to protect against vulnerabilities, for example, by encryption viruses, - add the word “WriteProtected” in the last name of the catalog. Instead of directories on the "C:\Docs\My Projects - WriteProtected" folder, it will be blocked to change whether the program is a crimson explorer. If you need to change the data - either change the directory timely, or move the data to another directory, and after the completion of the work, turn it off.
The next hour, the next hour, the magazine is being watched, especially the firewall and the proactive attack (“Zakhist+”). There you can see what the programs need, add-ons are allowed, for example, for updating. It is also necessary to change the configuration in a different order.
If the program is blocked by an antivirus, we can change it to VirusTotal via the context menu. At the same time, in order to be safe, we add the program to the trust. Yakshcho, regardless of sumniv, the program must be vindicated, copy it to the catalog of vignettes. To click on it, using Shift, in the context menu, select the "Copy infection file..." item and save it to the C:\Exclusions directory. From this directory, the launch program appears to be unknown, in the virtual environment.
At the time of the fight, the program that is running, blocking the OS interface and not allowing the sandbox to be cleared, you can close the hour of the night. Manual way tse robiti the context menu item "Run in the Comodo sandbox as an obmezhene", requests for the article about the virtual environment.
It is necessary to run the summing program in a real environment, working through the extended context menu item "Run Auto-Sandbox without environment". The activity of the program is controlled by additional HIPS alerts. In order to hide these great numbers, you can immediately select the policy of "Deposit additions" or "Isolation" in the alert policy (by enabling the option "Remember vibir"). Respect! The program can run a trusted program, and HIPS no longer controls the activity of the child process, which can be controlled by the root. As a help, you can turn on Viruscope at the same time, so that in more detail you can check the activity of not only a cumulative program, but also її child processes, and if necessary, increase the number of changes.
Sound out the HIPS warning for this configuration, or it can be blamed on the menu item “Run as installer without permission” or, more likely, in the menu item “Run as installer” and “Run as installer without privileges”. However, to remind HIPS about activity unknown programs in other modes - a central signal. Vin may mean that the program was not started before CIS, or it took away the privileges of SYSTEM. I recommend choosing the option “Block and end victoria” in this context (turning on the “Remember vibir” option in the new option), and then pereverit the system for quirks.
Tsey lesson є prodovzhennym statti: Merezhevy screen.
Father, we knew that they downloaded the rest version Comodo Firewall. More than one firewall may be installed on the computer. For the sake of avoiding inter-program conflicts, awakenings windows firewall guilty buti vmkneniy. How to turn off the Windows XP and Windows 7 firewall, you can look at the previous lessons: i. And if we install Comodo Firewall, there is no need for that. The firewall installation wizard itself will not wake up the Windows firewall.
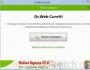
Firewall Control In the illustration, you can see how the firewall has gone over the sample software Nokia phone access the Internet need a program, then press the "Allow" button:

One of the first things you need to do is to allow the Windows system components alg.exe and svchost.exe. The stench is needed for connection to the yard. After installation, Comodo Firewall will re-install and re-install alerts for other programs. As soon as the program is visible to us, it is allowed to ask for a quote. If the program is suspicious, then the "Block" button is pressed. Signifying the ensign check-box "Remember my choice", we fix our choice for what dodatku. І in case of an upcoming call, there will be no notification for this program. Children need to be careful. Allowing us to close the vibir can only be given to us by the programs. If you press on the name of the program, you will see the power of the program.
Just like that, the firewall tells you about the entrances:

On the next illustration, you can see how Comodo Firewall has changed entry package for a popular peer-to-peer client:

On the back, alerting the firewall is something to pick up. Ale mi robimo svіy vybіr і z hour їх є є є less і less.
Malicious programs can masquerade under non-violent software, to fool the firewall and take it to the bottom. Therefore, it is necessary to regularly scan the machine with an anti-virus program. You can read a report about vibir and antivirus robot.
Let's move on to fixing the firewall.
Open Comodo Firewall, just like any other program, by clicking on the icon on the desktop or on the icon in the view area. There is a brand new program with the opened tab "Zvedennya":

Here, information about traffic and system status is displayed. Having pressed on the numbers of the day, you can look over the reports of the active merging connections. Pressing on the button "Supinity all z'ednannya" to pin the least activity. Zastosuvat tsyu funktsіyu can be in case of inadequate behavior of the system - suspect the program robot. For example, the system freezes for a long time and does not recover. Tse mozhe be a little bit of merezhovo activity, be it a shkidlivo program. By blocking the traffic, you can find out the reason for that program, to become a threat. All orders are entered by pressing the "Show all orders" button.
You can change the firewall operation mode by opening the list of what you can see with the "Safe Mode" button.
"Block all" - a mode that does not allow any kind of activity - the equivalent of the "Stop all connections" button.
"Koristuvachska policy" - tse hard mode, in which case the screen will display alerts for skin programs that connect to the Internet. Here, if you need to create the policies of the programs yourself, you should clearly understand what kind of supplements you can allow.
"Safety mode" is installed behind the promotions and є universal. Firewall zastosovuє koristuvach policy - vykonu settings koristuvach for okremih programs, and also itself allows fringe exchange programs, yakі vvazhaє safe. The notification will be small and the firewall will not be very effective.
The "learning mode" is appropriate, if it is necessary to follow various programs, without interfering with their work. Here, Comodo Firewall independently determines the policies of the programs, without displaying daily messages.
In the "Inactive" mode, the screen turns on. Minimize the firewall in case of obvious inter-program conflict, for example, with an anti-virus program or a different screen.
On the next "Firewall" tab, the parameters of the firewall have been changed. "Firewall log" - "log" showing all logs - firewall responses to the activity of other programs.
"Add to the approved program" allows you to select the required program and add it to the allowed ones.
"Add a blocked program", for example, gives you the ability to add the selected program in the fence for the day.
Distributed "Security security policies" in the window, where you can choose one of the installed policies for the program to create your own.
The "Active Merezhevі podklyuchennya" window shows the programs, which show at the moment the merezhnuyu activity.
"Master of Attaching Ports" - with the help of stitches you can attach songs and port and make the computer invisible at the selected meshes.
"Setting the Firewall" - tse vikno to the choice of the robot mode, which duplicates the list, which you can see, on the "Zvedennia" tab. So, set the "Safe Mode" button and put a flag at the "Create rules for safe add-ons" checkbox:

On the offensive deposit "Zahist +" the function was improved by a proactive defender. When installing a firewall, the proactive host is turned on behind the lock. Proactive Zakhist - another ball of Zakhist, which controls the behavior of the program and prevents the infection of the system. The settings for a proactive host are basically similar to those for a firewall.
The item "Launch the program in Sandbox" gives you the ability to launch a sumnivnu program from your own "sandbox". Pratsyyuyuchi isolated from this protected area, short program can't hack the system:

The item "Parameters of the proactive attack" shows the curve of the operating modes of the proactive attack. І, briefly, let's go through tsim lashings.
The "Paranoidal" mode can avoid paranoid suspicion to the point of being less active. A proactive defender will see alerts in case of a skin test, whether it be a program to restore the day.
In the safe mode, the zahist zastosovuє policy is set to coristuvach, and also allows the activity of the programs, as if they are safe.
In the "Clean PC" mode, the host insanely trusts all the programs installed on the computer and allows only for programs to be installed again.
"Study mode". Which regime does not have the right to conduct monitoring independently.
"Zakhist vimkneno". In this mode, the proactive defense is disabled. Vimknuti zakhist not varto. The optimal solution would be to install a secure regime.
On deposit "Rizne" roztashovani dodatkovі nalashtuvannya firewall You can marvel on your own. Looking around and so wiyshov ob'єmniy. Golovne, scho Сomodo Firewall, tse duzhe nadіyny, flexible in management, Russian and no-knit mesh screen. Comodo Firewall is linked with a powerful anti-virus program to ensure your comfort careless work in measure.
In detail, about the work that vibir antivirus software readable.
Krykhitka sin to the father of the priests, and the kriht was asleep:
- Whose Zakhist is good, and whose axis is not better?
I have no secrets, listen, lads.
I publish the thought of someone below.
There really is no shortest firewall, so it doesn’t exist on its own short antivirus or the browser - the skin of the computer's skin is selected by its best software product.
Possibly, at once richly rozcharuvav, ale tse so i є. The axis is majestic Comodo Firewall - the best firewall-free firewall for Windows and I don’t mix, but before the new one I have a sprig of fate miraculously pratsyuvav ESET NOD32 with its zahisnik, and after the new one, avast! Internet Security, also with an intermediate screen.
Vіdmіnniy and tinny bezkoshtovny firewall for Windows

I didn’t blame anyone for swearing at sakhist until I tried the rest of the complex a program for rechecking the firewall.
Vin failed the test and was praised for the decision to change the firewall. Vibіr falling on Comodo Firewall - vіn pass reverification for superiority and sig- nificantly completely without cost.
Today I want to describe to you the actual nuances of yoga installation and installation.
All our life is a joke. Poshuk pennies, glory, kohannya ... the best firewall or browser (folk wisdom).
Before you feed, you can download the installer of the firewall, which will be downloaded after the launch of the web installer - 202 Mb! Why such a wild rose?
That's why in a new place, the zayvih add-on browser was injected into the browser.
I'll show you at once how to install one Comodo Firewall and then you can boldly see the gigantic installer. Ale zavantazhuvat all the same, you need the entire file, for the help of the official site of the compilers, what is more ...
Zustrichav at the border, as if for a long time, relief installation file of which screen, without additional, ale, first, wine is not official, but in a different way, I have put in the effort 🙂 .
Installing Comodo Firewall
Over the course of time, program makers change the interface of their creations, improve them in every possible way, add new functions and remove them without demand ... Stink is right for the price. Whether they have a vipadku, logic, recognition and spirit, they are always overwhelmed with colossal ones - you can look at it in a way that you can grow into a software.






Axis stink zayvі dopovnennya. Check the boxes for them and let's go.


I have already described how to find the best DNS servers So from - COMODO DNS-servers are not only povіlnі, ale and pereljakanі on the whole head.
Having left the top daw, you add your own headline - half of the sites will be blocked. I recommend to another jackdaw.
Obov'yazkovo go to the item "Fix the installation".




The axis of wines, our dear one - like without Yandex!
We can clearly see all the jackdaws.


Looking around at all sides and z'yasovuєmo de znachimos. Since you don’t have your own home local networks, I recommend typing “I’m living in a big city”.
I live! We have installed Comodo Firewall - the best non-commodity firewall for Windows.


Let's now yogo trohi nalashtuemo.
Installed Comodo Firewall
Really, there are a lot of configurations for setting up a firewall - they block the Internet (the axis is one of them). You can make a defender in such a way that you can’t calm down with help, before food.
And you can perekonati yogo pratsyuvati quietly and unobtrusively - you virishuvati, I will bring only a little more joy below.
Go to the setup program.




…and put ALL the checkboxes in the extensions of the extensions (there is so much to do for the sake of the merezhі), and in order to blame you for the problems with accessing the Internet - check the two lower ones.


Here you can turn off the widget on the working table, as you do not need wine.


I'm doing yoga, although I categorically do not like any kind of widgets on the work table. Lightly rereading by right-clicking the mouse on the firewall icon in the tray.


And the axis is the most terrible setting of the firewall, how to transform yoga on the right concrete wall.


Deputy carefree regime you can install...


In such a regime, get ready for a million meals from the driver's side. Zate re-verification for supremacy now your Comodo Firewall is 100% passable.
The power supply to the firewall looks like this.


You can put a tick at the bottom of this vekna (remember ...) and allow vykonannya. Because you know the program, you are trying to get into the merger. Can you still "Obrobit yak" ...


In this rank, we will wake up repeated feeds, for example, how to download the Nexus programs to Clover.