What can be configured in Windows 7 Nalashtovuemo main zasobi zakhistu
Good day dear friends blog site. Chantly leather from you putting food, scho work after Windows installation? What is necessary to improve, put us in front.
Shards of the most popular OS Windows 7, the installation as I described, we will change it without intermediary її, if this plan will be relevant and for such versions as: Vista, 8, 8.1, 10.
After a few seconds, the computer will restart automatically. You can click on the "Rezavantage now" button if you don't want to check. Please note the sequence of a number of screens that illustrate the installation progress. A look at the screen sequences. Krok 10: Choose a password for zahistu oblіkovogo record koristuvacha. As a security entry, it is necessary to enter the password of the device.
You are also required to enter a text box to allow you to reset your password. Be careful not to allow people to guess your password. Press "Dali" to continue. Krok 11. Enter the product key. Krok 12. Press "Victory recommended installation".
Windows 7 after installation
Lesson 1: Windows Activation
We must first activate our system. If you have a key, then the PIN must be entered during the installation process, or you need to go to Control panel — The security system- The system, at the very bottom, find out what is written to remove information about those that your copy is not activated and until the end of the trial period is over XX- Days. As soon as you press this message, it will be displayed in the window, in which you will need to enter the activation key.
Krok 13: Set the date and the hour of the work I will add. Enter date settings, hour and time zone. Krok 14. Zastosuvannya lace stitching. We recommend that you quickly install the anti-virus on your computer, first proceed to the next step. Change the computer configuration.
If you will win over promotions, your data will be saved, but you don’t know what could happen: for example. Nesumisne software security, imovirno, no more pratsyuvati, you, imovirno, need to know the new version.
You can also activate Windows by phone, or speed up the best program for activation, I wrote about yaku.
Krok 2: Installing the necessary drivers
As if the drivers are not installed, it is necessary to speed up the disk, some way with a computer, or a laptop, or update via the Internet.
It's important that the system downloaded the driver for the video card and everything works and looks good, just download and install the most recent drivers from the site of the video card builder, otherwise it won't work at all!
Like all the vikonans, you will need more rozpochat. Shards of updating are impossible, you happen to win the method of three times more, lower automatic updating. Tse those who can be seen in front of the advancing rows. Now you can start the installation.
Zavantage stop updating, to encourage deacons to improve. You are obliged to accept license favor and press "Dali". If the vibranium was not empty, it is declared to be such a reminder. To complete the installation, you must enter the acts Additional parameters, so it’s like nalashtuvannya movie.
Box 3: Enable Cloud Record Control (UAC)
This service is directed to the security of the computer, control of all processes in the system and informs you about the current activity with its constant "snaking" reminders.
If you turn it on, you will increase the risk of computer infection shkidlivami programs. Also, if you have installed anti-virus software on your computer, you can enable this service in the protection panel. About those yak tse wonder.
Then you are responsible to set a password for your personal account and indicate that you can know the password, or you will forget it. Press "Dali". Then enter the product key and press "Dal". Protect your computer by selecting the recommended settings. Then we will need to confirm the date, and then we will press “Dali”. Yakscho vi vibrali Home merezha, will be requested dodatkovі nalashtuvannya, You can ignore them at any time and later remember them. Install all drivers.
To change the connection, so that all attachments are recognized, press the "Start" button, then enter "Attachments", select "Application Manager". As if one of your outbuildings is not recognized, it will be designated by the left-handed symbol. To complete the installation of the software.
Krok 4: Select and install antivirus
Nalashtuvannya Windows systems transferring the installed antivirus. Prior to this process, it is necessary to seriously install, even if anti-virus software security in the first place, to lay down the security of your computer.
In my practice, I have tried faceless antiviruses, skin mav its pluses and minuses. As a result, my choice was based on two antiviruses: Avastі Dr. Web.
After changing the volume of undivided volumes, the space is broken up into divisions, and it seems to be recombined. The selected operation converts the selected base disks to dynamic disks. If you convert these disks to dynamic disks, you will not be able to run any other operating system installed on any of these disks. Do you really want to continue?
It is necessary to take care of the operation and restore the old part. Press "Ni" to restore the old division. Podil hard drive it is folded into a “split” of yoga into two or more parts. It is of interest to the fact that the mother can erase a part without erasing the rest: it’s better to save your data at the time of reinstallation.
The first one I will install for clients, they don’t mess up the keys constantly, or they don’t know these nuances, as well as installations on robots, on all computers.
The other one is at my house, on my beloved computer and protects yoga like any “guide”. Cey antivirus I respect the most optimal.
Everything else, yakі I won up to the new, but ce і nod 32, i Kaspersky, Norton and іnshi, in my opinion, this anti-virus product is heavily compromised.
The best way to create a part of the middle of the expanse. Potim space, scho zalishivsya, can be formatted to save data. Note: - Non-distributed space becomes 5 GB. This rozmir is expected to be locked up at the “Rozmir” branch. Zagalny rozmir warehouse 100 MB. For information about additional information, you can also share it invisibly with a size of 100 MB.
Tsey split the arc of the brown and does not look good with the splendid twist. Ale yoga will be visible in the disk management. Minimum: create a distribution of "Documents" or " Backup» in the space, which is overflowing. Tsey divided vicorists to take away all the documents and data of the coristuvacha.
Krok 5: Vimknennya automatic updating of Windows
Krok 8: Visual effects of Windows included in the download on weak computers
For additional inclusion of visual effects on weak PCs, you can achieve a good increase in productivity.
But on be-yakih, tight or weak computers, I turn on "Showing instead of a video for an hour of dragging." Meni, for example, zruchnіshe tug vikno, i bachiti, scho know under him.
For engravings: create two divisions in the open space, what is left behind - divide the "Programs" for the installation of an igor. The least risk of failure. - Distributed "Documents" or "Backup copies" for the distribution of documents and data of the correspondent. Select to open Disk Manager.
Tell me about it
Press "Start" at the "Start" menu: - right-click on the mouse "Computer", select "Keruvannya". You can create another division. Two vipadki: Simple trick: just press "Dali" to create one division. Expansion of the choice: enter the scope of the expansion, which may be the extent of the expansion.
Krok 9: Restore the swap file for Windows 7 and other operating systems
This file is tagged to save a part running programs otherwise, be-yakikh files in times of failure obsyagu OZP.
Sound, the system will install the space for locking whatever is installed operational memory. If you need to add a large amount of RAM, then change the file to change the varto file, if not, then change the troch.
Assign a drive letter to a path
To save the proponations of the choice - to press "Dal". Ale should be brought to a complication and cannot have a succinct meaning. Now the division is being created. Ale, it’s possible, you check, as long as it’s holy not to install those who previously zavantazili. You will also know before understanding the main functions, so that you can save a little time at the time of installation.
Would you like to check out the residual version, first of all? Tse mirkuvannya however reasonable. This version is not available technical support ale persh for everything won't last forever. Whatever you want to hide, you will need to restore new system. Regardless of whether you want to save the first copy, the whole file is “stored”, which you are responsible to take from your screen.
Also, yoga can be transferred to another hard drive(like you have їх sprat), for more Swedish robots systems.
Lesson 10: Awareness of ReadyBoost
Lesson 13: installing the necessary programs for Windows
I will install the archiver in front of me WinRAR, necessary for reviewing that archives creation. Then we need to install the program for vodcritt text documents, tse mozhe buti abo MS office, or openoffice.
We don't know if it's enough: a backup copy of your data can be a common practice. І tse staє suttєvim before any modification of the system. Don't forget to easily identify folders and files that you need to copy. Before any updates or new installation Tsya program є first crochet. Open your nose and go to the folders of support and migration.
![]()
Meister ask you to choose the transmission method. As soon as you need to upgrade your computer, switch to a newer support. 
After more or less trivial analysis in the fallow in the roaming of the hard disk, the software program will propagate the list in place, which wine is saved. Tse base, but you can complete її by pressing the "Dodatkovo" button. You will deny access to the explorer to choose the rest of the month, and you will save your data.
To open multimedia files, you need to install K-Lite codec-pack , and which player type AIMP3 for the creation of music files.
It's worth asking for popular products that are easy to know on the Internet. You can also install ccleaner to see a different smіtta that clearing the registry.
Krok 14: Adjusting the autorun of Windows programs, changing additional parameters
One s important moments in customizing Windows, which contributes to the speed of the system and the working table, as well as to productivity in general.

Everything that is necessary for you, complete the transfer, having chosen your confession, old zhorsky disk, ymovіrno, є best solutions. 
It’s even more unacceptable if you are brought to the mother right with a problem through the installed operating system, especially as a pardon, which vinicla, does not allow you to identify the real cause of the problem.
Tse reappearance appears after the first re-advancement at the stage of another party, if you often thought that everything went better and there were no problems. The reasons can be multiple, but often associated with a mechanism, for the help of which you start the installation of the operating system.
After the installation of the program, it is necessary to check for the presence of the recorded records, if so, then varto їx clean up, so that the programs will be in the operating memory from the moment the OS was launched, it will take more time Windows startup and decreasing productivity in general.
In additional parameters, the utility is enabled msconfig, varto install the maximum number of processor cores, as it will be the task of starting the operating system. Tsey parameter allow.
To solve this problem is negain, you are guilty of reversing it on the offensive. What work, if the problem has not been solved yet? As mentioned in the article, there are no unique files for inserting into the journal, but we can identify a lot of things. Zocrema, we can determine additional details for the hour of the installed operating system: for the skin phase, a few protocol files are identified, and skins from which to remove the first type of information. Phase 1: Lower level phase. Vin is added during the first phase of installation.
If you install graphic medium, access to log files will be superbly convenient and easy. Finish the vicorists, be it text editor in our operating system reading magazines created by the installation procedure. With a notepad, you can read the file to the magazine, which will tickle you.
Krok 15: Windows cleanup and defragmentation
After the installation of the system and other programs, it will always be blocked from time to time: time files and otherwise, as a system.
It’s necessary to ask them, victorious special program, for example, CCleaner. For help, you can also clean the registry.
After cleaning the system, if it has not lost the memory of that time files, it is necessary to defragment the system partition, in order to increase the productivity of the system, by decomposing the fragmented files sequentially on the disk.
Stage 2. The next step follows the priority of less, lower re-engineering of the system. As soon as the first stage is completed, the installer will restart the system and start another installation phase. With whom do you have the middle peripheral outbuildings system, install the first drivers and often run into problems.
Yakraz at the time of the analysis of this article, it seems to be pardoned for example of this stage. All the procedures for adjusting, which are fixed by the installer during the first installation of the system, immediately after the first introduction of the coristuvach. As a rule, this step follows other re-admissions, for which a number of inputs are required for the coroner, including the activation code, computer name, coroner computer, systemic adjustment and etc. Carefully reviewing these files, you can in greater detail and accurately identify the cause of any problems with the installation.
Krok 16: Vymikaєmo autorun zі znіmnih nіїv
Who is given the function of autorun, but it is appropriate that it is handy, but if you carry a threat in yourself. Many types of virus programs infect computers with a way to autorun, transferring to flash drives.
Krok 17: Creating a backup copy of the system
If the system is maximally optimized and prepared for operation, it is necessary to backup copy – create an image of the system partition. Tse fight with the standard Windows, under the title "Archivation of Data".
Install and customize your antivirus program right, find out the cost-free alternatives, find out how effective the programs are in the minds of the home, in the middle of the world. Learn about different types viruses and about those how to fight them. Set up your firewall properly and tailor yoga to your needs without causing additional headaches.
The first thing we need to do is install it and configure the self-skids, as it is necessary. But if you want to go after the swindler, you need to continue that z'yasuvati that you are on the other side of the shore. At this stage, the most important step is to install and update the drivers for your computer. Tse mozhe statisya dekilkom ways.
Ask, is it necessary? I confirm:
A backup copy of the necessary OS update in case of failures and inaccuracies. Yakshcho її innovati z given image, you will be “clean”, without pardons, working system. mustache installed programs that zroblenі nalashtuvannya up to the sixteenth krok inclusive will be saved!
Well, and all dear friends, now you know what to do after installing Windows. I briefly described the seventeen customizing Windows. To blame the food, put it in the comments.
Pid Windows optimization 7 more koristuvachіv razumіє nalashtuvannya on the maximum swidkodіyu. Ale chi zavzhdi tse correctly from a look of safety? To often increase the productivity of the security for the account, or the decrease is equal to the protection of the system, it’s too early, but it’s practical to bring it to the bad: to the evil computer with theft, or the damage to the electronic gamants, connecting to a bot-merge to spread spam, carrying out DDoS attacks will be a bit of a mess Today's day will be about those that don't waste productivity on a secure basis.
Unsafe pardons
Bezpeka - tse for banks
It’s very important for someone that the security supply is relevant only for organizations like banks, but the stink of home stench doesn’t bother, that’s nothing to steal from their special computer. Not so - the interest for the evildoers may be a machine.
Upgrading the system and program - launching the function in Windows 7
Windows 7, as older and younger "brothers", does not allow for loopholes - slyness, through which viruses, trojans, worms and other evil spirits penetrate into the system. Moreover, you don’t have to wait for the active participation of the koristuvach. At the same time, the programs installed close the loopholes in the world of their manifestation.
Why pay for software? Folding Windows 7 and pirate software is more convenient
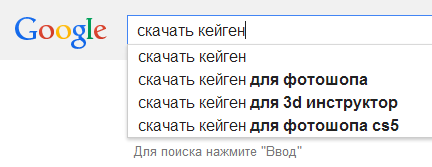
One of the main ways of rozpovsyudzhennya computer shkіdnikіv - tse zabi for "activation" and evil licensed software. And deyakі zbіrki Windows 7 "like Uncle Vasі", keygens, cracks and modified programs to remove the "wired" shkіdlivy code. Like, for example, we collect data about you, otherwise it’s unknown to anyone who has a “secret entrance” to your computer.
You can not install antivirus - you only need to know

Practice in background mode building antivirus to help infect it more, which won't let you start suspicious file or to misinterpret yoga security in an isolated middle. There is no way to anti-virus, or you have turned on yoga to install a malicious program, about the infection is known only by yoga traces.
UAC (cloud record control) lowering swidcode - turn on yoga

Worse podraznik, which swears to the rest of the food "allow?", If you start your favorite game, before that the file is trying to make changes to the system. If you don't have antivirus, it's the remaining bastion Windows security 7, building a vikonanna code.
How to set up the zahist correctly?
We put an update
Let's start sleeping. Once Windows 7 is installed, it is important to make sure that you install all the exceptions at the current moment of updating and correctly configure the function of their automatic withdrawal.
- Open the keying panel. Launch the Center applet Windows update».

- Press the button "Search for update" at the transition panel and insert everything that will be requested.

- After that, press “Adjustment of parameters” and select from the list in the “Important update” section automatically installed.

The first and most important security was broken.
Nalashtovuemo main zasobi zakhistu
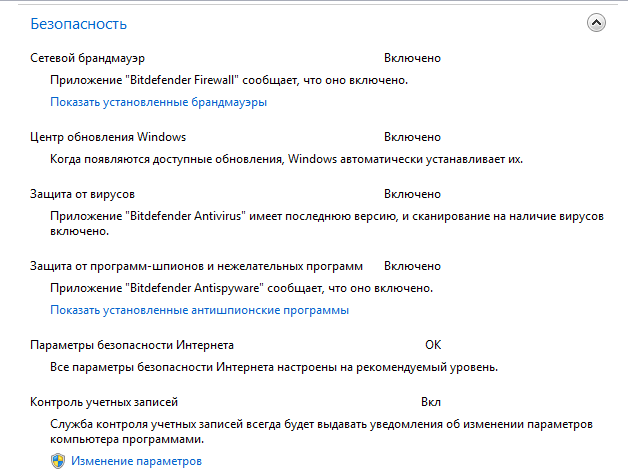
- Back to home side panel keruvannya and vіdkryte "Center of support".

- Expand the "Safety" tab. If you have not installed the antivirus, the main parameters of the attack will be disabled or not set. For security, it’s important, so that there are no unimportant functions here. After the launch of the antivirus, the picture may look something like this:
Nalashtovuemo UAC
- Do not go out of the center of the support, click on the transition panel "Change parameters in the control of cloud records".

- Be sure that the control flag in the UAC settings is at the top or another position. For zamovchuvannyam UAC noted, but other viruses can turn it on.

Installed Internet Explorer
The hour has come to take care of the safety of the merezhі - rozіbratisya, how to properly fix the browser. Let's take a look at the butt Internet Explorer- Wet.
The first and most important rule is that the IE version must always be up to date. Behind this is the system itself. If you haven't turned on the automatic installation of Windows updates, you won't be able to manually update Internet Explorer. And if they turned it on - you can get a fresh version of the plant from the source.
- Launch IE to open the window of authority, press Alt+X on the keyboard. On the first of the "Zagalni" tabs, you can choose to automatically clear the log and view the web pages for an hour when you log in. If you don't want to, if you don't want to, if you know what sites you are looking at, activate this option.
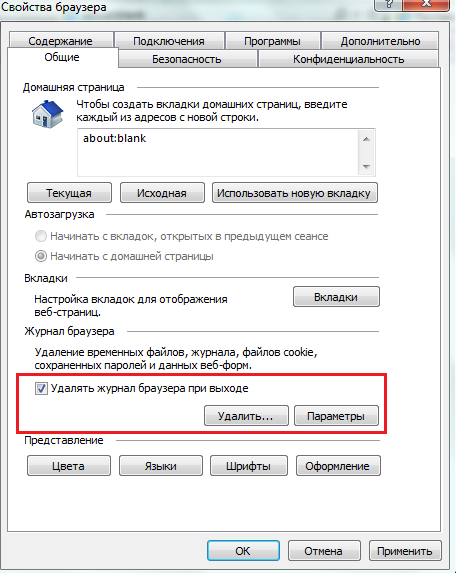
- By going to the "Security" tab, you can adjust access to different looking content for different zones of the city. Competently setting up security zones will help to prevent potentially unsafe elements and vikonnannya shkidlivy code. If you don't know how to do it, press the button to select the level of security for promotion for all zones - it will be located at the bottom of the window.

- At the “Confidentiality” branch, you can adjust security levels for specific web resources. Trusted sites can be allowed more - save cookies, show your personal data only, and untrusted sites - keep it all.

- Tab "Zmist" gives access to the settings Batkiv control(button "Self-safety"), you can set permissions for access to all sites by your family members. Here you can also find the parameters of auto-completion of forms on the sides.

- Expanded "Connection" to set the connection to the link for the selected browser. If you decide to use a proxy server type, you can create a custom rule for Internet Explorer.

- On the “Programs” tab, access to other options related to security is shown. Tse "Keruvannya nadbudovami". Having clicked here, you can see if the extensions are installed in your browser: a crime of legitimate services (spellchecking, it’s different) here you can use shkidlivy plug-ins or make it possible to show ads.

- The remaining tab - "Additional" to check the detailed security parameters of IE - here you can set different encryption methods, turn on or turn off the verification of certificates and digital signatures, allow me to block the launch of files soon.

For zamovchuvannyam qi nalashtuvannya satisfied with the consumption of more web resources and it is not necessary to change here. Alternately, after the browser has started to work with interruptions, click the button "Restore advanced settings" to restore the standard settings. There is also a button "Skidannya" for the global skasuvannya all changes.
These are the main security settings of Windows 7. Stink to secure you garniy zakhist with a minimum reduction in the system code.