How to configure Internet Explorer.
submit
Golovna Optimization of work The Internet Explorer browser is one of the oldest.
Regardless of the great number of analogues at this time, it is still popular among traders. The author of the internet explorer browser is Microsoft company , therefore it must be installed simultaneously from the Windows operating system. However, for IE to work stably, it needs to be tuned, and also be sure to keep up with updated plugins that are being tested, and new versions of software.
Knowing how to fix it
internet browser explorer, will help you independently get rid of the problems that arise from viruses such as automatically switched on

offline mode or blocking activex elements.
Basic browser setup
 In order to go into settings of the Internet Explorer browser, you need to click on the gear in the left
In order to go into settings of the Internet Explorer browser, you need to click on the gear in the left

upper codend Or quickly use the key combination “ALT+X”. In the window you need to select the “Browser Power” item.

Many people are confused about this section of the menu with “Customize your needs.”
However, the plugins are functions and plugins that are connected to the browser, and this section is also responsible. Zagalni parameters The advanced settings tab allows you to select the pages you need to start working on.

In addition, you can select the display of adjacent tabs and the parameters of their behavior.
Can be changed

If you don't want to delve into external adjustments, go to which you can by pressing the “More” button, you can turn on one of the security levels that are included in the system and set their settings: low, medium and high.

In addition to controlling parameters, such as those found in security parameters, you can control many important criteria for the display of pages, such as:
- blocking leaking windows;
- checking the authenticity on the site and saving authorization data;
- bathing with different activex elements;
- Video display, animation and singing type queries.
If you are not aware of this or that other setting, be careful.
- Turning off certain activex parameters may cause problems with the display of page elements or may block them.
- I would especially like to zoom in on:
- allowed the downloading of unsigned elements to start;
automatic launch of servicing elements and recording of permissions for them;

enhancement of offline mode. Privacy tab Internet Explorer's privacy settings allow you to control how websites access your data and requests are processed.

It is possible to turn on one of the levels or set the adjustment manually, checking if the detail is acceptable, and also block it. U additional adjustments
є ability to control the processing of cookies.
In the treatment of sites, it is possible to prioritize the display of elements and consider equal access to the skin resource.
- In addition, it is more manually adjusted What allows you to block or allow leaking advertising, which is sometimes simply impossible to do in any other way.
- Be careful when changing your privacy settings, otherwise you may permanently block communication with the site and prevent offline mode.
- Connection settings
- This adjustment allows:
- turn it on and adjust it
automatic connection

A tunnel connection is created for secure transmission between two points.
This type of connection is also used by various providers to provide access to the Internet using the additional protocols PPTP and L2TP. Adjustment of display on site based on criteria key words asked from “Family Bezpets”. Add manual function for adjustment
Father's control
allows you to block unnecessary resources.
In addition, it includes display of RSS feeds, setup and connection of certificates, as well as enhanced auto-renewal functions.

Programs tab
Use the wiki to select an html editor, a client for working with mail, for writing websites, and also the previously mentioned “Badware Management”. In this window you can edit extensions, programs, spell checkers and quick fixes. Career management is even more important, because with their help you can turn the browser into an advanced tool for a web designer or optimizer and analyst. At the same time, virus programs are most often used here, which often block the work in global measure
.
The one who got here Discount code You can turn on activex elements, turn on redirection to other sites or offline mode, and also block access to social networks.
Additional tab
Adjustments that have not reached the desired level of the basic parameters, but may also have more important values, remain in the “Dodatkovo” deposit.

In addition, you can earn money outside skidannya Internet Explorer, turning to the settings, the tasks for washing up during the installation of programs.
If you are using the current version, you will not find this option enabled or disabled.

If you have a power outage, your computer will become more infected with viruses.
In this case, you need to check it, then delete the registry entry for the entry assigned to the baby, or change its value to zero.
After this, the offline mode will be disabled and the sites will be available again.
Problems with the offline mode arise from the same reasons for viewing pages in the offline mode.
And turn on your viruses and bad programs.
If your browser works perfectly well, it doesn’t necessarily have a bad Internet connection.
Third-party toolbars, add-on tools, cookies, and other settings may also interfere with your browser's performance. Here are some simple steps you can do to optimize your Internet Explorer browser: More ideas that can be brown:

View of toolbars There are a lot of toolbars that will attract attention and be used by the browser, not only interfering with its current appearance, but also increasing the flow of Internet traffic. The browser toolbar is an extension (extension) added to the interface.
At the same time, as additional actions in the browser can expand online capabilities and can even turn out to be negative, otherwise they can lead to negative consequences. The stinks can easily be installed on their own in the “for cleaning” status, coming in a set at the same time as they are expanded cost-free programs , and they sometimes interfere with or conflict with other software on the computer. The skin panel of tools contains many specialized functions, such as search functions, emoticons, musical producer And so on, in this way, you can extract additional resources for your work. To remove actions from toolbars, you need to open the list installing their programs (for Windows 7 press Start
(Start) > Control panel(Control Panel) and in the section
Program
(Programs) click Vidalennya programs(“Uninstall a program”) - remove programs that you do not use. Nalashtuvati nadbudovi(Manage add-ons).
3. Under the letter Represent(Show) select Usi nadbudovy(“All add-ons”).
4. Select your skin, if you want to stick in, then click Vimknuti(Disable).
5. When you are finished, close the window and restart the browser.

Clear cookies and clear browser cache
Few people do not forget to work, and hard drive appears to be a re-examination of the great amount of data that is unfortunately saved by the browser.
To clear your browser cache:
1. Open Internet Explorer.
(Programs) click Vidalennya programs(Tools) , point your mouse's login to the item Safety(Safety) and select Vidality browser history(Delete browsing history). If you do not want to delete cookies and website files from your favorites list, set the Save data from selected websites
(Preserve Favorites website data).
3. Set proportions opposite those types of data that need to be deleted. Control panel 4. Press

(Delete).
Skidannya customize your browser
Sometimes, when you install the program, it may change your browser settings without your knowledge.
You may notice that your browser is acting strangely.
(Programs) click Vidalennya programs If Internet Explorer stops responding to commands or functioning in general, if you encounter notifications about notifications that inform you that Internet Explorer will be closed, or if you are Of course, you might want to reset the settings and configure Internet Explorer. For this purpose, move the lines lower. 1. Launch Internet Explorer.
(Tools) then select For this purpose, move the lines lower. Browser power (Internet Options). 3. At the window
3. Set proportions opposite those types of data that need to be deleted. (Internet Options) click tab Dodatkovo
(Advanced). (Internet Options) click tabSkidannya(Reset).Internet Explorer 5. In dialogue (Internet Options) click tab
parameters fine-tuning press
Install the ensign
viluchiti Features of customization(Delete personal settings) especially if you want to simultaneously view the log of your browsing history, search service settings, Precise, home pages, Anti-virus protection and ActiveX filtering data. By doing this, you are essentially launching the latest version of Internet Explorer..
6. When Internet Explorer completes the transition to standard settings, click
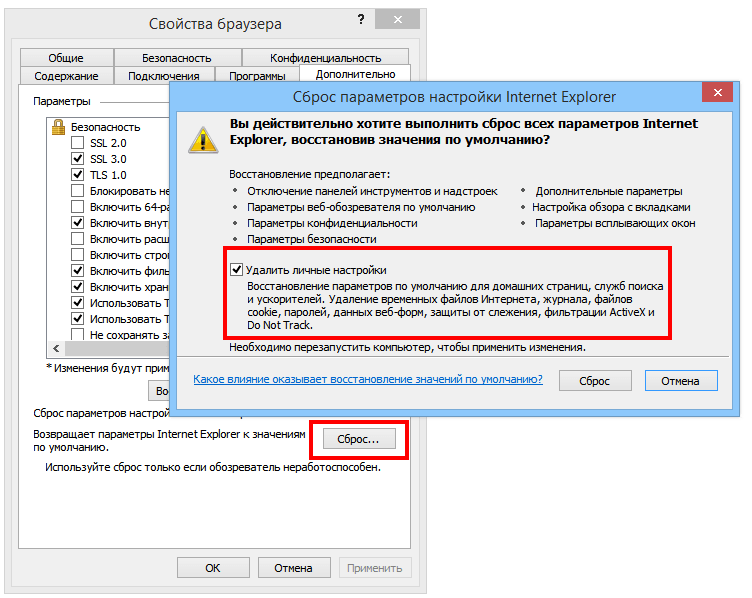
Shut up
(Close), and then OK 7. Close Internet Explorer and start it again.
In the table below you can find out which version of Internet Explorer you can use in connection with the operating system you are using:
To uninstall the remaining version of Internet Explorer, follow the instructions.
Switching to another browser
Because of the absence of Internet browsers, some parts of the skin are more susceptible to others. Some browsers are crashing great quantity
Functions other than the senses are easy to access. The actions work a little better, a little more., All Internet browsers basically offer the same function: allowing us to browse websites. The most popular browsers
Google Chrome
Mozilla Firefox , Internet Explorer, Safari and Opera. There are also other less popular browsers, such as RockMelt, Avant Browser, Maxthon, Deepnet Explorer, Flock, SeaMonkey, AOL Explorer and others.
In most cases, switching from one browser to another is the best and easiest way to solve a lot of problems that we encounter.
If the browser overrides toolbars and plugins, if it does not open the website's activities or retains the content for a long time, you can try installing a different one and see if it works better.
To install a new Internet browser, you will need to use the one you already use to find and use the other one.
Just speed up sound system.
, Such as Google or Bing, to find the browser you want to install, and click on the link to download.
The axis of the page on our site is the most popular browsers that can be used instead of Internet Explorer:
You may also find this article helpful on how to optimize speed and productivity while surfing the Internet while using Chrome and Firefox.
For materials on the Internet portal.
Russian translation: Oleksandr Ryabov
Select section
Nalashtuvati for robots on electronic trading platforms
Possible mercy
As soon as the hour of work on the ETP appears one with a message:
“Mercy! Internet version Explorer below, below 10, you need to run the 32-bit version (to do this, open the folder C:\Program Files (x86)\Internet Explorer and run the file iexplore.exe).
What kind of surgery do you have? Windows system 10, re-open the browser you are opening Microsoft Edge, an icon very similar to Internet Explorer.
2. It is necessary to add the ETP addresses to the correct nodes.
- In Internet Explorer "Service" - "Browser Power" ("Browser Power");
- go to the "Security" tab;
- see "Nadіynі vuzli" ("Nadіynі sites");
- press the “Woozy” button (“Site”);
- Check the box below “All nodes in this zone require verification of servers (https:)” (not all ETPs work with secured https:// connections); *. In the “Add to offensive zone” row, enter the ETP address (http and https);
- insert the website address, followed by a forward slash // insert
and the site address.
- Addresses to be entered may take the form “http://*.kontur.ru/”;
- Press the “Add” and “OK” buttons.
3. For the “Native nodes” zone, allow the selection of Active-X elements.
in Internet Explorer "Service" - "Powerful overview";
go to the "Security" tab; see "Nadiyny universities"; press the “Increasing...” button; In the “Active-X elements and connection modules” section, all parameters are set to “Disable”. 4. Click and install CAPICOM-KB931906-v2102. 5. In IE 9 and above, there may be problems that can be found by speeding up the mode of insanity (Go to Browser Power - Service / settings for the mode of insanity / add to the address of the maydan). Note: this
Zagalni customization
for all UTP. On these squares it is necessary to install».
Now you need to check the box next to the “Vocate proxy server” option, enter the name of the proxy server you selected in the “Addresses” field, and enter the name of the proxy server in the “Port” field, indicating the number of the proxy port.
If this is necessary, check the box next to the option “Do not use a proxy server for local addresses”, and also click on the “Add” button, then enter the parameters for various protocols. Finally, click on the “Ok” button twice: the first time to close the Dial-up or local settings window, and the second time to close the Internet settings window. Ready.
How do you wish to work in Opera browsers 9, go through the menu menu Tools -> Settings -> Additional.
Now go to the “Merezha” tab, located in the section of water.
Customizing the toolbar
superior, ferocious to the point View This menu will ensure access to the most frequently set settings.
At the menu View You can add and clean the panels behind your tubs (Fig. 1).
In order to add or remove buttons on standard toolbars, change their size and rearrangement order, select the command Toolbars à Nalashtuvannya, The result will display a panel (Fig. 2), where you can change the icons.
At the menu View You can also customize different browser panels: Search, Search, etc.
(Fig. 3). View Invite website developers to determine the size and image of fonts on the page. However, these parameters may not be optimal for you. You can set the text display mode in your browser settings. For what's on the menu point the mouse cursor at
Font size
and select
required size
(Fig. 4). View Of course, you have come across the situation when, instead of the text of the page, the browser sees a set of characters that is not readable. For which option you need to check whether your browser is coding correctly for this page..
The codes of Kiril (KOI8-R) and Kiril (Windows) often get confused. (Internet Options)..
Most web pages contain information based on which the browser can install the necessary coding.
Since such information is available on the web site every day, and Internet Explorer has an automatic selection function, the code will be selected automatically. To enable the automatic code selection function, you need to go to the menu Internet Explorer browser (Fig. 5) put an ensign at the item Autovibir Because the additional auto-selection did not allow you to determine the correct coding, but apparently, because the coding itself is necessary in a particular situation, you can select it manually using the vikory command
“Zagalni” tab
and contributions Zagalni(Fig. 6) can be called so called “ Home page", this is the page where you start looking at Web resources.
Timing files on the Internet Apparently, in order to quickly look through the pages that you have already seen, they are stored on the hard drive of your computer singing hour Saved by dad Temporary Internet Files. This organization of saving speeds up the display of frequently accessed Web pages, since the browser can open them from your hard drive The names of sites that are not accessible offline will appear in gray color, and those whose information is cached on the hard drive will appear in black (Fig. 7).
Obviously, the more space you have on your computer under cached storage, the greater the reliability that the information will appear saved on your disk again. To enable the automatic code selection function, you need to go to the menu To increase your Internet cache, go to the tab “Zagalni” tab at the divisions and select an item Parameters
, the result will display a single panel (small 8), from which you can adjust the maximum permissible folder size for saving timely files on the Internet. Zbilshennya of the Miss, reserved for the folder, the Zberigai Files, the sbilshiti, the lunge of the wound outlining the web-striking of the Keshi Vashi comp'yuter, is obviously a prote, the census of the zoom..
disk space
On the next screen of the master (small 10) you can set a mode in which there will be an advance payment for the same pages where the basic pages will be sent.
Moreover, you can install clay in a posilan.
Next, you will be asked to select a method for synchronizing the page (Fig. 11).
There are two options: follow the “synchronize” command or use a new layout.
If you select the “new layout” mode, the Master instructs you to select the synchronization frequency and indicate the synchronization hour (for example, today at 23:00).
- “Privacy” tab Internet Explorer ensures the confidentiality of the user and the security of his/her personal identification information.;
- Internet Explorer privacy features include:
- safety parameters that indicate the processing mode
cookies
privacy alerts, which notify you when the website you are visiting does not comply with your selected privacy settings;
To be safe with P3P, the Web resource is required to describe its privacy policy in order to indicate what information about private users it records, how it saves it, and what cookies it creates. Denmark described is formalized in accordance with the P3P specification and placed in the root directory of the site. Internet Explorer reads Denmark file
it removes unnecessary information.
The main channels for the flow of confidential information are third-party sites (they are also called third-party sites), which are sites that are addressed in parallel with the node that is being looked at.
- A third-party is any Web site that is not displayed in the browser window.
- The websites you view may contain content from third-party Web sites, which may, in turn, set cookies.
- In Internet Explorer 6.0, a security guard has been installed that blocks cookies of third-party sites, such as:
It’s not reasonable with P3P because they didn’t declare their privacy policy; supply the individual with information without the explicit consent of the koristuvach; to supply information to a particular person without the explicit knowledge of the koristuvach.
To change your privacy settings, go to the tab
Confidentiality (Internet Options). move the bar up to increase the zakhist level and down to set the lower zakhist level (small 14). A description of the setting modes is given in the table. Please note that changing privacy does not affect cookies that are already stored on your computer.
By pressing the button
on the panel (Fig. 14), you will go to the panel where you can select
Additional parameters
Privacy: disable automatic processing of cookies and select the mode for accepting first-party and third-party cookies (Fig. 15).
Security tab
Internet Explorer divides the Internet into zones of different levels of security, which allows the necessary level of protection for each website.
A low level of security is established for the washing facilities in the “Nadiyny Vuzli” zone.
Internet Explorer will allow cookies from Web sites in this zone to be stored on your computer and read by the Web sites on which they were created.
Obmezhenі vuzly
For this area, a high level of security is established for washing areas.
Internet Explorer blocks all cookies from websites in this zone.
“Zmist” tab Access restrictions If you use a computer at home and are afraid that your children may look at these pages, access to which should be limited, you can access the settings that are posted on the deposit Zmist on the panel
Powerful look around
(Fig. 19). You can limit access to thematic groups of sites or install a tight barrier to access to specific sites. It’s difficult to kidnap a child from all singing-themed sites, unless you have information about specific sites that you want to block access to, it’s much easier to earn money.
For example, at the deposit
Allowed universities
You can enter a list of sites blocked for review (small 20).
Authentication problem
Authentication is the basis for secure communication.
Correspondents try to prove that they are the ones they think they are, and at the same time they cry that their correspondents, in their own way, don’t see themselves as anyone else.
The special certificate is verified by the supplier to confirm the identity of the buyer who accesses the website that issues the certificate.
The Web site certificate confirms its reliability to those clients who use the service thoroughly.
A certificate that certifies the “speciality” of the website is necessary, for example, when sending confidential information via the Internet to the website or when importing software from the website.
The basis of authentication is encryption using a private key. The certificate contains an identifier with a private key. The private key is shared with the owner of the certificate, which allows him to digitally sign or decrypt data encrypted with the private key.
A digital signature on the certificate, and an electronic identification of the buyer, which informs the recipient that
information given
It arrived efficiently to the first correspondent and was not changed at the delivery stage.
If the user's website is stolen, the remaining one will automatically find the owner's certificate.
As a result, the user receives information about the data that is securely connected and the data transmitted by the user will not be accessible to third parties (Fig. 21), and when entering more detailed information in the IE browser, explanation about the mode of exposing a stolen node (Fig. 22) . To remove the ability to overpower encrypted or digitally signed messages, you will need to revoke the special certificate and configure Internet Explorer to work with it. include information about the retailer in the programs that are distributed throughout.
If customers purchase a security program that is signed with an authentication code and verified by a certification authority, they may be able to withdraw the security program from the same company that signed it and that the security program has not been changed since subscription.
Such a system is the basis for protecting the rights of others, for example, in the event of the occurrence of viruses in the code.
Based on code authentication, users can safely revoke the signatures of ActiveX controls, signatures of Java applets and other programs.
Software distributors are also included in the authentication of the product, which is distributed throughout Merezha, as well as compiling the details of their software. Any company that wants to expand software or external information via the Internet will need a similar system. Client's Microsoft programs, such as Internet Explorer, Exchange, Outlook,
Outlook Express
- , supplied with protection systems that also include an authentication system for the program code that is downloaded via Merezha.
- It is necessary to pay attention to everything that the system has been re-insurance from Merezha.
- Similar to the component model, elements such as ActiveX or Java applets can be downloaded to your computer whenever you browse a Web site.
When a customer accesses a Web site that requires animation or sound, program code is often downloaded to the client’s machine to implement the required function. In this case, the user runs the risk of being infected by a virus or other unsafe code. in order of authentication.
In this session, clients can trust the following procedure of attraction.
Customers can also select the command “Always trust the verification procedures with this vendor” to speed up the verification procedure.
Customers can access additional information about the certificate (Fig. 25).
Installation of certificates of types
Certificate issuers create special, so-called root, certificates that confirm the validity of their private keys.
Each specific type of certificate is a basic root certificate: one for e-mail certificates, another for new special certificates, and a third for servers.
Some browsers are issued with a set of such certificates.
If, when viewing Internet resources on your site, you visit a server with a certificate from an unknown vendor, you will be prompted to accept this certificate and, rather than replace the root certificate of the same vendor, you will be prompted to You can install this certificate and recognize the actions of servers with certificates that have been revoked from this one. I see.
A variety of digital certificates can ensure secure transactions on the Internet, since they allow you to associate the identity of the certificate holder with a pair of keys (public and private).
Obtaining a special certificate
The procedure for retrieving a certificate looks like this: you go to the certificate issuer’s Web server, fill in the data necessary to retrieve a specific certificate, and select the value of the private key (must not be less than 1024 bits). Before submitting the form, your browser generates a pair of keys: public (unlocked) and private (closed) - and enters them into a password-protected database. The private key is shared only with you - it is not your fault if it is disclosed to no one else, including the certification center.
Nafpaki,
secret key
must be completed together with other data entered before the certification center for inclusion of the certificate.
It is impossible to find a pair behind the private key - the private key. After issuing a certificate, the certificate authority will authorize you the certificate or provide you with a URL whose credentials can be collected. After obtaining the certificate from the certificate issuer, the browser automatically starts the installation procedure. Access restrictions Installation and issue of certificates You can enter a list of sites blocked for review (small 20). In Internet Explorer there is a certificate manager - Internet Explorer Certificate Manager (Fig. 26).
It allows you to install and remove client certificates and certificates of certificate authorities, or, as they are known, CA (Center Authority). Rich CA is already looming root certificates Rich CA is already looming.
, installed in Internet Explorer. You can choose from any of these certificate installations to verify the authenticity of the code, the reliability of the time stamped in the documents, the stolen mail, etc. To install or delete certificates, go to the tab
.
Select item
Apparently, modern browsers, such as Internet Explorer and Netscape Navigator, manage internal caches, which allows you to use up a lot of disk space on your machine, which is used to cache documents you have already looked at.
The browser periodically updates documents in cache to keep them fresh.
However, the amount of cache on a PC is small; small PCs rarely cache more than a gigabyte of disk space, so the amount of documents that are saved is small. On a local computer, it is difficult to see a large amount of memory, but this can be done on the provider’s proxy server - a computer that runs a special program that caches data that feeds all the clients of this provider. If you use a computer at home and are afraid that your children may look at these pages, access to which should be limited, you can access the settings that are posted on the deposit Zmist Great providers can see tens or hundreds of gigabytes for their clients. Some traders are afraid, however, that by storing cached documents from a proxy server, they will be able to remove old documents, but there is no technology that allows them to be lost. There are low criteria for praising the solution for caching on a proxy server. For example, since the object of designation is confidential, it is not considered confidential.
In the same way, there are criteria to determine whether a cached document can be sent to the client. For example, if the term for the document has passed, the server will not send it to the client, but will request a new document. In this way, fresh documents (with an undefined term of attribution) are downloaded immediately, and since the proxy server has doubts that the document is fresh, it can be requested from the Web server and the document is changed.
It is entirely possible that a document with a term of attachment has not yet been “zipped”, and therefore has not been updated, and in this case the Web server informs the proxy server that this document has not yet been “zipped” and it can be delivered you ask the client. In other words, there are all the steps needed to quickly access a proxy server. And enter the proxy server address and port - these addresses can be identified by your provider. (Internet Options). I benefit from the services of the Zenon company, and in my opinion, proxy.aha.ru. Then go to the item.
(Fig. 33) and indicate One proxy server for all protocols Please note that working through a proxy server is optimal. The most obvious rule is that since you have less access to any Web server than a proxy server, there is no point in accessing through a proxy server. Or, for example, if you are running Java applet on your server, you need to constantly be amazed at how correctly your security software, then, obviously, you are not controlled
latest version applet. On the panel shown in Fig.
33 Dodatkovo,