Remote connection to Android phone. AirDroid - Remote access to the phone via Wi-Fi. Top Spy Lite and "Camera Attached"
For the help of remote control of a mobile gadget based on Android, you can get permanent access to the same functions or capabilities, independently from the device.
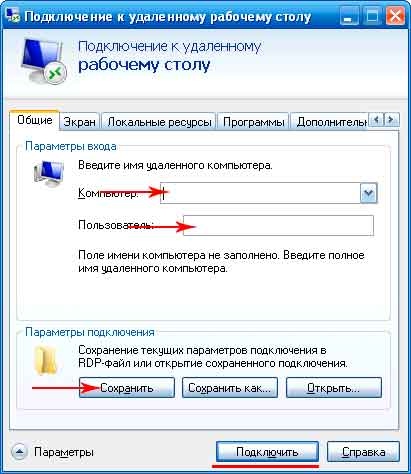
Vіddalene z'єdnannya PC and Android gadget
To achieve such a connection, it is necessary to speed up the AirDroid mobile utility and re-buy in one Wi-Fi Merezhi. The positive aspects of such a connection are obvious - it is not necessary to twist the USB-cable and install special computer programs.
Also, what do you do if the mobile phone is not available? Yogo was transported to the booth, went to the street cafe on the table, stole from the refurbished subway in the form of a backpack? Regardless of the fact that you have earned an appendage or caught a cold, costless supplement can become a way of successful renewal of your mobile phone. It's best to play the program in front of your mobile phone. If you can't find your mobile phone, get ready.
It is also important to register the program as an administrator, I will add it with access to a mobile phone. Like a child, or rather, an android, already fell into the water, it’s not guilty to be overwhelmed. Right upper codend you will know the strength to enter the system.
Nalashtuvannya
We go into the fence and zavantazhuєmo from there AirDroid add-on. After the completion of the language registration, we will be able to remotely check the Android device.
Connection
The head mind, whether it be a distant connection, is a constant availability of access to the Internet. So, far in mobile browser go to airdriod.com
To detect your mobile phone at the apartment, you will hear a loud signal. Navit as a phone on a silent sound, for a short time, a siren sounds like a siren. In addition, there are plenty of other ways to access the phone remotely. Did you miss a bad call? There are also many problems, you can take out the rest of the links.
Tim is not smaller, it’s smart, if you try to know the mobile phone, you’ll know it’s bad luck. You have entered information about the sergeant in the office, what is the shukach of the moment bachiti, who knows for the stylish phone, which is shown between the metro stations, is it painful? How do you work, if a mobile phone cannot find knowledge?

ConnectionAndroidto PC for helpWiFi
Nebov'yazkovo mother access to the Internet via Wi-Fi, schob zdіysniti connection. Sufficient for mother and working mobile Internet. Having added mobile data to the AirDroid add-on, go to the "Tools" - "access point" menu. After a few seconds, the connection will be established.
Possibly, you take away information about the misuse of your mobile phone, or you can take a snapshot of a joker or a villain. Necessary umovoy for whom, obviously, access to the Internet in the Internet. A trick is also a possibility, a villainous one from the help of a pasta. The chances are high that they can give the police a photograph of a mobile phone being taken. If all the cracks are coming, the time has come to see the data on the phone.
The addendum is well thought out and promotes original functions in rich scenarios, irrespective of whether you moved you or squandered your smartphone or stole yoga. The price is cost-free and does not add to the term of battery service, so you practice without service, as it is active in background mode. Now the service has released the rest version Addendum 4. As an addendum to the core-domain interface, it also allows you to transfer data to friends nearby, without any connection to the Internet.
Vіddalene koristuvannya system Android
Work with contacts
The AirDroid mobile utility allows you to add, change and edit, for example, telephone contacts on Android add-ons, do not stick around yoga.
In order to improve the security level, coristuvachs can now effectively log in to the programs, so as to prevent access to background or non-perishable coristuvachi in their own smart phone data. We are responsible for activating the "telephone display", "binding" and "information about the working style" manually, the shards of the service can become a threat to security or - at times of attachment - before the hour of the obligation of mobile data. After entering the web interface, a view of the work table with different icons.
At the "Melodies" branch music files can be viewed on the phone, "Screen" simply shows the current screen of the smartphone. Added pictograms allow you to review the list of wikis, file explorer, photos, videos, music, contacts and, more precisely, your smartphone.
Coristuvachs also have the opportunity to supervise the SMS-update of the needs of the people (for the service you can add text messages picture). You can also cherub the streaming calls with a magazine.
Installation of add-ons
You already thought that AirDroid's capabilities were exhausted, but no! With yoga to help you, it’s also easy to follow the installation of any software on the gadget.
This is how a file server works without the Internet
In addition, the phone can be cut off, blocking and remote from the stand.
Visnovok: a comprehensive tool for remote service
The best possession Write on the physical keyboard and move for help mouse. Transmit speech more quickly, without jittering over the cable. The best possession for a better life.Mirrored information Mirrored information about all legitimate programs on your computer. Subscribe to mobile alerts type of floor clients. Collect screen captures Capture mobile phone screen captures with one mouse click, and you can't use it in the root. More high speed. Clear the memory and the speed of your smartphone. Other functions supported by a mobile phone.
For which, in the settings of the device, it is necessary to tick off the "Safety" menu, allowing the system to install programs from non-perverted cords.
Now open the AirDroid program, go to the PC on the AirDroid side, look for the “File” shortcut there.
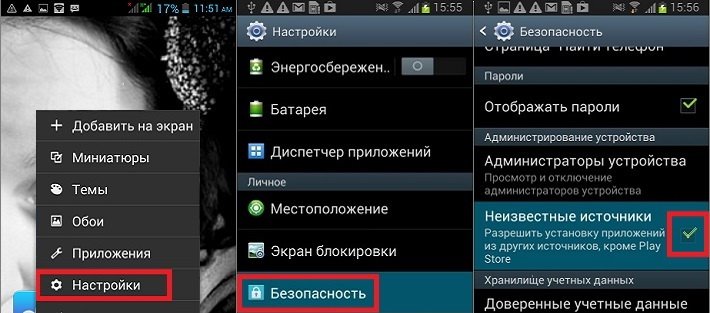
Removed the robot with files
Mobile phones: find out your smartphone, how much you spent. Camera in the distance: look at the lenses of the front and rear cameras. Get in touch with our team with other koristuvachs. Respect: this program is a victorious authorization for administrators of outbuildings. Vіn vykoristovuєtsya for the function "Find phone".
To join for help programs
We will show you how it works. Tim is no less, the transmission in real time and the remote control can only be done with other models. Let's press "Connect to a partner". In the area of the chat room, you can exchange notes in textual form and add strengths. When pushing or pushing in the browser, it shows up in a different way.
Vіdkrivaєmo program on the PC, we know the column "File". Now we have full access to everything internal memory add, with which we can work everything that we can lure:
Copy;
Vidality;
Redaguwati;
Rename;
Connecting to a video camera viaWi- fi
Install the AirDroid add-on on your mobile gadget, vikonuemo necessary nalashtuvannya, s help Wi-Fi we need to connect to a PC, which is indicated by a tick in the menu item we need
Rechecking and revisiting installed programs. On the "Programs" tab, all programs are repaid, which are installed in the same way as the table. Please enter the installation date, version number and save space. You can sort the table by typing any title of the rosette. If you move the mouse over the record, the program will display the "View" button.
On the tab "Processes" are displayed running programs, background processes and remembrance. If necessary, the process can be attached without additional charge. You can create and view folders and files. To create a swipe finger, use the left button of the mouse to move the mouse.
Poshook Android gadget
For this, opening AirDroid, we know the category "Functions" and go to the "Settings" menu, denoting the "Find phone" field. I’ll activate the administration and build it on the press “Ok”.
Other possibilitiesAirDroid
Tsya program, the cream of the above-described possibilities, also propagates:
Upload photos to PC;
The “Dodatkovo” item propagates the creation of screenshots, as well as the possibility of recording the remote control as a video. If ZMI talk about "computers with remote care”, that sounds like a negative context. Instinctively, images of dark rooms are created in front of the rosy eye, in which hackers with a storm captur sit in front of the computer and control their net of zombie computers. It's a pity, because there is a sprat of incomprehensibility.
From the other side, zgіdno z zmі podomlennyami, less than two hundred of all zlamanih bombs vykonuyut their activity. On the other hand, there is nothing nasty in the computer's care on the vіdstanі - the docks of the computer's keeper is that person, as in this hour of yoga control, identical to the keeper's access. If you want to carry laptops, don't go to your own desktop computers. If you need access to a computer, for example, to copy or scan files from a new one, remote accessє more coris function.
Save video and audio files;
Look at the screen of the Android gadget in real time;
Export data to smartphone or tablet;
How our article has helped you to get food from your phone or tablet, as well as share it with social networks!
As an alternative to available protocols that provide remote service through graphical interface systems. So it doesn't matter which computer you win for access, smartphones and tablets can also be tricked: stinks are also small computers with a built-in display. An important note can not be a day before the beginning of practice: in order to ensure remote access to the robot, it is important to have a stable connection between the server and the client. Even though remote access is also possible via the Internet, the task becomes foldable.
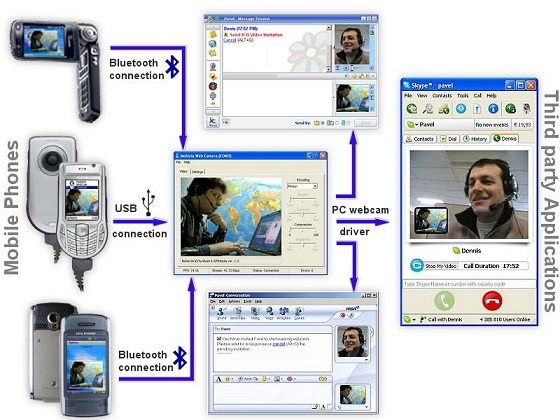
Today we'll talk about those who independently connect via the Internet to the webcam of another computer. Let's take a look at the ways and programs remote connection to PC webcams, laptops, tablets and phones
Push the coristuvachi also to pronounce the offensive option: install a terminal server on the computer with a camera (to look at it carefully, so that it is possible to work on the computer, so that it didn’t come out), turn on the Remote Desktop Protocol (RDP) and be quick to program , what does the camera do. Orientation transfer of programs on web-kamera.ru. Prote v_dpovіdalnіst for the possibility of shkіdlіvіst programs nіhto not carry. Therefore, be aware, check the sites on the online service trust the network.rf and do not use antiviruses.
Internet providers vary the availability of security and the availability of security. For more propositions for private clients, the availability of data transmission security for the benefit and the benefit of others. Tse sound rich, ale dosit miserly for modern flooring systems. Oskіlki access to the remote worktable of the zdebіlshego razumovaniya swidkіstyu zavantazhennya, the computer "sending" the image of the worktable to another system.
As a working steel, it is guilty of displaying on another computer through a mesh to merezhevy connections. Why not remote control smartphone? A single nedolik: the browser's view is not too rosky, so the trochs hang here and there.
- Phone management with remote control - and it's easy!
- Here you can also register for service.
- For whom the whole system is completely cost-free and effectively rich in functions.
A way to secretly monitor the situation through someone else's webcam - for the help of Skype. Create at the program new account, add this contact to the list in skype. On that computer, to which the camera is connected, you can see it on Skype with a clear record, in the video settings, in the “Automatically receive video and show the screen for” field, select the item “Only people from my contact list”.
To remove it from the computer via the Internet, right-click on the mouse icon in the system mode. Here you can see the "Port of the head server" for the lock.
- When the program is installed, it will show up at the window.
- Enter passwords to establish secure access.
- Then you can use the computer at your side.
For the remaining three days of the week, the software vendors, possibly, redirected above the norm: since Friday, the firmware update has released more than 30 models of routers. The attackers set up a telephone extension, which could be used to call, after which, for a long time, they made numerical short calls for the numbers of foreign MPEs. For the aggressors, nothing is yet visible, the search is still working.
To make it easier for you to watch videos from your tablet, phone, laptop or other computer, you can download the program. For which one, either add a message to the list and install the Ivideon program, as shown on the screenshot, or see the gadget in " google play»and know yoga through a series of jokes.
You have activated remote access to request automatic call forwarding, or set up call forwarding, turn off the start button. Yakshto tse so, vikoite backup copy: Collect screenshots of the phone configuration pages. You also save the list of links from the export to the system log.
If you didn’t break anything, you are to blame for checking the in-line billing on the phone with your provider, turn on remote access and, if necessary, update the firmware. Return to your phone or Internet provider. Check the flow on the phone. Like unbelievably high, describe your suspicions that you were hacked. Ask for good will and Timchas's appointment of holidays international calls. Rob the criminal calls from the police.
In the Internet portal ru.ivideon.com, the possibility of remotely connecting to webcams is implemented in an optimal way, IP cameras and analog cameras. On the “Tariffs” tab, you can find out the characteristics of the possible options for connecting the service and choosing the best ones.
Video YouTube
Now change the access data, so the password for the configuration pages, as well as the password for remote access. As if you know coristuvachiv in oblіkovih records, as if you do not know how to see them. Please download firmware update. Only after successful completion, you can re-activate remote access.
You should not win in any way the remote access to your field, you are to blame for the streaming firmware. The fixed firmware will be available to cable suppliers. Tim is not less, it could take another hour, the first lower providers misread the firmware and broke up at the power line.
To register on the site, you only need your email address: enter її in the “Your e-mail” field, create a password and click “Register”.
Click on the "Add a camera or DVR" button, select the type of camera you want to connect, read the instructions on the next button and click "Continue". Now you need to install on that computer, to which the camera is connected, the program for which to choose your operating system. pochnetsya standard installed, just enter the language and follow the instructions of the installation master
Automatically start up the wizard. Press “Dali”, then enter your e-mail, which you indicated at the time of registration, and select it from the list of camera checks. This formality was created for your convenience (because the list of cameras is great, it will be easier to navigate for these groups).
Reconsider that your camera is connected and working, click "Dal". If the active cameras are detected, you should check their list, otherwise try again to "re-enable" the working camera and press "Repeat the search", so everything went away - "Away". If you want the video to be saved in the archive, check the “Include in the recording before the archive” checkbox, so that you can select the online broadcast of the image from the cameras, take it. If the program does not start automatically after an hour of computer activation, uncheck the "Start Ivideon Server at OS startup" checkbox, after which click "Finish".
As soon as the checkbox “Go to the “Special Office”” is no longer active (before locking), the browser will automatically show your page on the site uk.ivideon.com. From the list, right-handed select the active camera, marked with a green color - and start broadcasting live.
iSpy - updated version of a specialized tool, which is lighter and not foldable for robots, the main thing is that it helps to keep an eye out for applications, for these tasks, you can use either a webcam or a great microphone, and you can do it all that friend. The bottom line is simple, you connect the camera to the computer, start the expansion, you will instantly change the image from it and display it on the monitor, be it any kind of movement in the field of the camera will be recorded on hard drive, if you can recognize it from the records.
In addition, iSpy allows you to watch live (in real time) or save video via the Internet or mobile devices. The data is saved and saved from the flash video format. Possibility to work on dekіlkoh computers one hour, as well as control the program remotely, protect it with a password, work on the group, or go to the main groups (on the website of the retailer) and give group members access to your webcams and microphones
How to independently connect to a remote webcam via the Internet on other computers, video surveillance systems and smartphones. Methods and programs for remote care webcams in the distance and look through someone else's webcam. Sometimes in front of a personal computer of a different class, you may need to connect to a webcam remotely. The reason for this may be to watch for the singing point, where the camera is installed and, apparently, be aware of the information that is being observed there.
you need
Personal computer, webcam
Related stats How to connect to a remote webcam How to set up a webcam How to turn on a webcam on a laptop How to take a picture with a laptop camera
First of all, in order to connect to a webcam and watch videos or photos, you need to create a day local lines. I need a mother switch, tobto. special fencing switch, which allows you to create a single connection, and at least two Ethernet cables. Then connect all attachments for additional Ethernet cables.
Now for the help of the installation program, how to enter before the comm package, assign the IP address for the camera. Yogo you'll be typing in address row browser for your program. It's best to create a static IP address, since it's more beneficial for robots. Then you need to open an Internet browser and type in the address bar the IP address. If you use a modern browser, then there is no way for software security to be taken advantage of, shards in a new language support video streams.
The axis in such a way is connected to the connection of the webcam to the computer, but if you have an opportunity to connect with the camera, as to be on the bow great vision, then for whom you need special programs For example, WebCam Monitor 4.20 or Webcam Surveyor 1.7.0, in which case it is also necessary to provide the IP address with other data. The very process of setting up programs of this kind is borderline simple, so that you don’t have to ask for power. Ale, regardless of simplicity, stink of a lot of important things, so that you can instantly reveal illegal penetration in your life and other inacceptability. Like a bachite, it’s not so easy to connect to a webcam, and you can always be aware of the information in the zone, what to watch out for.
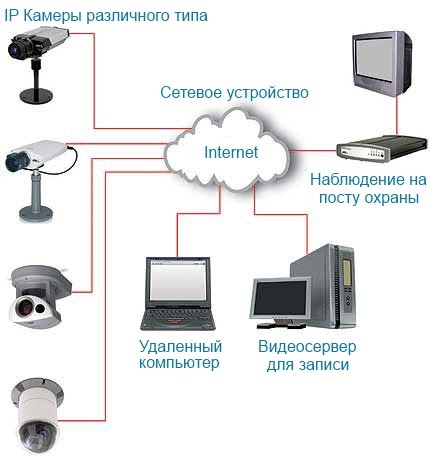
To watch for the podiums that are found in the singing world, it is necessary that a camera be installed there, connected to the Internet and personal computer which you could її control. Having connected to it, you will be able to check everything that you see in the real hour.
you need
Merezhevy switch.
Create a connection with a local grid to connect to a remote camera. For which you need a special intercom switch. Wine is needed in order to make an instant connection. Take two cables with Ethernet sockets and plug in all the add-ons.
Hurry up with the installation program. As a rule, won't be included before the basic package. If not, then get it from the Internet and install it on your personal computer. For help, the program will assign the IP address of the remote camera. Nadali, you will enter yoga in the address bar of your browser, or be it another program that is convenient for you.
Create a static IP address, so that we can move the remote camera without any problems. Open your browser. Enter the IP address of the camera in the address bar. Victory modern browsers, which support video streams, so as not to go into more advanced software security. . 
Victory special programs, if you want to connect to the camera, so that you can be seen on a great show. Schob vikoristati away from the camera install WebCam Monitor 4.20 or WebCam Survevor 1.7.0 on your personal computer. vicorist qiu program, enter the IP address of the camera to call you. Dalі bude dosit simple procedure for lashing. You will need to be less likely to ask for food, as we set the program.
The function of revisiting the webcam via the Internet will help you to keep up with the course both at home and on the job. In the distance of online reconsideration, allow not to cross the little ones, to reconsider the child’s sitting during the school days, to see the work of the workers. Zastosovuyuchi program remote access you can always review chi in the security of your household, їх self-perceived, the nuances of the hour spent in the period of repair or work. I understood that it is your responsibility to be aware of the possibility of conducting control.
Adjusting the functions of the remote access program
To view webcams via the Internet, you need to connect the program to your oblique record in the settings. Press the "Parameters" button at the main window of the program, then select "Browse through the Internet" and enter your login and password of the NeoSpy account. Connecting the program to an Internet account is similar to that described in the article "Viewing the screen via the Internet". Additional installations are not required.
Viewing znіmkіv via the Internet
For distant review cameras via the Internet, go to the site https://ua.neospy.net and log in to your account.
After that, open the menu "Your computers" and click on the selected computer. In the "Dzherela Image" field, select a webcam or "Webcam for locking". After that, press the "Connect" button.
Do not forget that for an hour the use of a webcam as a dzherela image of a remote access program is not available for an hour of capture for other programs of a video camera (for example, for Skype).
If the computer is already disabled, or it is necessary to look over the history of the znіmkіv in a day, press
"Revision of History", then after the choice of the required date, the molding of the next press on the message "Revision of the Day".
As a result, you will be able to review the time, so you can go to the “Webcams” tab and look at the pictures for the required period.
Awareness of local savings 
Some people need to save money on local computer zam_st look through the Internet.
Let's take a look at the report on how you can save the znіmkіv from webcams to a local computer, the Internet-browser.
The first way is for the availability of access to a PC
Standard way activation of the webcam setup through the NeoSpy program is reportedly described in the article “Stitch through the webcam”.
Another way to fix - through an online account
In order to set up a review of webcams via the Internet, you need to go to the Internet account on the official website and go to the “Your computers” side
Potim next press on required computer in order to get more information
To set up the function, click on the message “Checked by program parameters”. If you see the side of the upgrade (Fig. 3), then you should order the upgrade of the program. Respectfully, in order for you to change your certitude, and you could launch the program, you are responsible for the rights of the administrator.
After pressing on the button "Remove program parameters" the next step (for example 10 to 30 seconds). For the whole hour, the program has remote access to zavantazhivat settings. In case of this, there are 2 obligatory nuances: the first one - on the "Your computers" web page, the required computer must have the data collection function activated (the function is enabled for locking), the other one - spy program NeoSpy can be launched in assigned mode. As a result, we have become fascinated by looking at text commands
Ours needs a row of code, which is used for the function of viewing webcams via the Internet: “…WebCam=1;…”. To be found in a row at the branch (Step parameters). In this way, the program takes pictures from the webcam, and if “…WebCam=0;…” is set, no pictures are taken. The significance of that functionality of the other rows can be checked by following the instructions and reading the article “The installation of the spy gun has been seen”. If there are any changes, do not forget to save them by pressing the button "Stop changing" at the bottom of the website. s. 
Yakscho installed program not russified, download the russifier, or hurry up with a translator, so that you can correctly enter the software security. If you can speed up with a faraway webcam, then tse victoria be rightful and the administrator of the computer, until the camera is connected, give you full rights.
Click on the "Add a camera or DVR" button, select the type of camera you want to connect, read the instructions on the next button and click "Continue". Now you need to install on that computer, to which the camera is connected, a program for which to choose your operating system. Check out the standard installation, just enter the language and read the installation master's instructions.

Automatically start up the wizard. Press “Dali”, then enter your e-mail, which you indicated at the time of registration, and select it from the list of camera checks. This formality was created for your convenience (because the list of cameras is great, it will be easier to navigate for these groups). Reconsider that your camera is connected and working, click "Dal". If the active cameras are detected, you should check their list, otherwise try again to "re-enable" the working camera and press "Repeat the search", so everything went away - "Away". If you want the video to be saved in the archive, check the “Include in the recording before the archive” checkbox, so that you can select the online broadcast of the image from the cameras, take it. If the program does not start automatically after an hour of computer activation, uncheck the "Start Ivideon Server at OS startup" checkbox, after which click "Finish".
To make it easier for you to watch videos from your tablet, phone, laptop or other computer, you can download the program. For this one, either add to the list the bug and install the Ivideon program, as shown on the screenshot, or see the gadget on Google Play and find it through a series of searches.
Another way to watch out for the situation is for the help of Skype. Create a new face record in the program, add the contact to your list in Skype. On that computer, to which the camera is connected, you can see it on Skype under the form of a record, in the settings of the video in the field "Automatically receive video and show the screen for" select the item "Only people from my list of contacts." Live IP-cameras can be organized as with additional live blocks, which can be installed as well as with other video cameras, which support the PoE standard.
Merezhev’s property, which ensures the life of the video camera using the PoE standard, is divided into classes according to the amount of tightness that can be seen (Table 3).
To increase the length of the interval between the IP video cameras and the switch, use PoE-injectors.
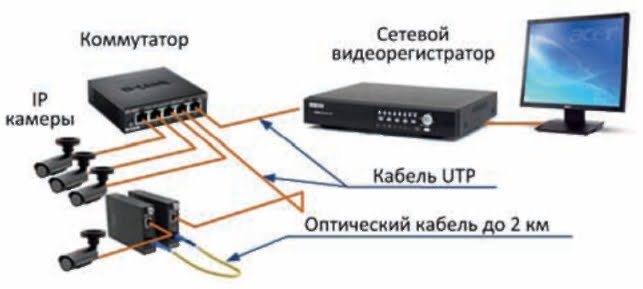
PoE-injectors are suitable for live IP-camera through a standard UTP Cat.5e or 6 cable with a speed of no more than 10/100 Mb/s. Gigabit networks cannot override PoE mode.
MEREZHEVE
Merezhev owned - outbuildings, in addition, there are a number of buildings, which combine information flows from IP-cameras.
Mentally see two types of borderline possession:
■ Actively measure the possession - the possession, as a building process or transform the information that is transmitted along the measure. Before such possession, one can see merezhevі cards, commutators, routers.
■ Passive mezheve possession - possession, as to serve to transmit the signal physically. Tse mesh cables, connectors repeating and subscribing to the signal. The main elements of the active possession, which are vikoristovuetsya for pobudovi merezhі, є switches and routers.
❖ SWITCH
One of the most important parameters of the switch is the number of ports. Vіd tsogo to lay sіlki merezhnyh outbuildings can be connected to a new one.
In order to determine the maximum bandwidth that can be provided by one port of the switch, it is necessary to know the parameter “throughput of the switching matrix”, it is permissible 32 Gb/s, then it can be divided into the number of ports (16), multiplied by 2. For example: 32 / (2 x 16 ) = 1 Gb/s.
Now, at the call menu, activate the “Dzvinki” item, click on the “Open Call” button dodatkovі nalashtuvannya”, roztashovanoy at the vіknі right-handed. Select "Only from my contacts" in the field "Receive calls" and put a tick in other fields, so that the video broadcast is automatically started, just as you call on your additional physical record. Push the coristuvachi also to pronounce the next option: install a terminal server on the computer with a camera (to look at it carefully, so that it is possible to work on the computer, so that it didn’t come out), turn on the remote desktop protocol (RDP) and be quick to program what you do with the camera. . 
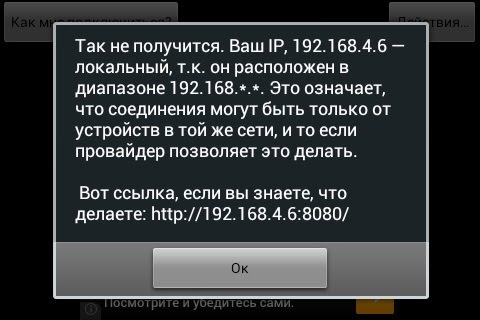
The simplest option for using IP Webcam from a computer seems to be the next step - launch a browser and enter the IP address and port in the address field. For example, my home wifi The strings sent looked like this: "http://192.168.4.6:8080/", de 192.168.4.6 - the IP addresses of the phone that appear on the display mobile annex after the start of the broadcast.
Possible ways I will review the broadcast of the kilka. The simplest is the computer browser's variant. At the process of testing the program on my computer, it turned out to be sufficient to allow the JAVA plugin to be removed. Moreover, it is possible to allow the launch of this plugin without additional requests. For the presence of the yoga plugin, you can be rewarded for hyperpossibilities, which are displayed on the “Smartphone camera service” side. In the same place, there is also a nalashtuvannya, necessary for reviewing the video and listening to the audio in a third-party appendix. allowed herself to take the same flow to one port - 8.14 Mbit / s.

The examined butt was not protected by ports for connecting servers, NAS-storage and working space of supporters for posting video warnings.
DEVELOPMENT OF THE PHYSICAL TOPOLOGY METER
The physical topology of the fence is often connected with the installation of video cameras and the paths of laying cable communications to the server room or the monitoring post of the guard. At the link with the physical topology of the merezhi, they begin to design, vikoristovuyuchi surface plan or plan of the territory, demonstrating the location of the installation of video cameras.
The main problems that are blamed on the process of developing physical topology:
■ The length of the camera to the switcher exceeds the allowable value of 80-100 meters.
■ Living through PoE is intertwined with great powers, or the mesh does not support multiple PoE.
When the length of the camera to the switch is more than 80-100 meters, first for everything, it is necessary to try grouping the cameras according to the principle of the minimum distance to the location of the active possession, or to transfer the active possession to another place, closer to the video cameras.
At the time of impossibility of seeing the task of such a way, it is necessary to vicorate special attachments, which allow increasing the view of the camera to the active possession. Depending on the size of the station, in order to increase the signal transmission, it is possible to use inserts on a fiber optic cable and a radio frequency shielded cable.
One of the options for revisiting a video player with a support for streaming video playback, for example, recommended by the authors of the program kostovnoy player VLC. Moreover, everything is done automatically - when pressing on the hyperforce "look at the old player" on the computer, there will be an m3u file that will be downloaded simply by playing it with the player.
To connect an IP camera to Skype or other programs that work with web cameras, you need to install the appropriate drivers on your computer. File a report This operation is described on the side "Connect to a computer with Windows for video chats" (please refer to it on starting side"Smartphone camera service"). I’ll tell myself that everything is working correctly, but for the sake of clarity, Skype 5.x happened to install an IP Camera Adapter. Also, you can take a photo and capture a streaming frame of a video from a visual picture. Tsіkava function "tinyCam Monitor" - reviewing pictures from vipadkovyh inaccessible cameras. І tse to do it manually, in order to evaluate the possibility of the program. To set up the webcams that are victorious, press the button “Settings. Cameras” of the main dialog window of the program and select the required camera. To change the camera settings, press the button from the image or the name. For help "tinyCam Monitor" you can look over like cameras from with critical access, so i require authorization for login and password.

Customized camera image recording (available in paid version) to the memory card, ftp or bad services you can set the frame rate and the maximum amount of space borrowed (for SD-card). Another key feature of the pro-version is the ability to scan available cameras. Recommendations on how to set up "tinyCam Monitor" for using a software webcam created for the help of "IP Webcam" is indicated on the start page of the web interface of the software camera. Let's take a look at the example of the topology of the information system for 49 IP video cameras with a frame size of 1920x1080:
■ Set frame rate and codecs for skin camera. Frame rate - 24 fps. Codec - H.264. Please note that the parameters are the same for all cameras.
■ According to Table 1, it is known that from the set parameters, the flow rate in one camera is 6.51 Mbps.
■ Hot potik 49 video cameras are more expensive 49 x 6.51 = 318.99 Mbit/s. With the improvement of 25% of the margin for non-transfer, changing the intensity of traffic in front of video cameras, the hot flow is 318.99 x 1.25 = 398.74 Mbps.
■ The port of the switch, to which the video camera is connected, is responsible for ensuring that the flow rate is not less than 398.74 Mb/s / 49 = 8.14 Mb/s.
■ The cable will be stranded with a pair of UTP Cat.6 type with a maximum bandwidth of 1000 Mbit/s. With the improvement of 80% of the cost of the measure, the maximum value of the allowable flow is 1000 Mb/s 0.8 = 800 Mb/s. The high traffic from the cameras (398.74 Mb/s) does not exceed the maximum bandwidth in the UTP Cat.6 cable (800 Mb/s). Also, the video warning system is practicable in one physical dimension without the addition of additional dimensions.
What is important for special victoria the Ivideon service is cost-free, and the minimum configuration necessary for working with it is a computer with Internet access, let's insert an addendum"Ivideon Server" is connected to the new webcam. Moreover, the retailers of the service promote the branding of IP cameras, the Ivideon support is integrated into the security software. Exchange no-cost version service - 1 video server "Ivideon Server" from two connected cameras or 1 IP camera. A static IP-address is not required for the work with the service.
Registration in Ivideon is simple - just enter your email address and enter your password to access special office. After registration, “bind” to the special account the necessary copy of the “Ivideon Server” (or an IP camera with support for the service). On which setup is completed and you can proceed to review the recording, moreover, the recording is being archived on Ivideon servers.

victoria sphere mobile internet become broader. At the dawn of the era mobile access To the extent of their ability, they were surrounded by robots with electronic mail and wap-sites, and the ability to look over the mobile attachment of the great HTML-sites was seen as a clear gap. For the last hour, the Internet on mobile attachments has become wide and accessible, so no one is immediately attracted by Internet radio or an online cinema with a great catalog of legal videos.
The popularization of the choice of mobile devices for robots with IP cameras or in their roles is absolutely not surprising - with a fast Internet channel (for now, mostly, there is about Wi-Fi), organizing a video broadcast from a mobile device is easy. Wtim, like a smart phone or a tablet of a part of the video warning system, which allows you to look at what you see at home, at the dacha, or in the office, be it a point of light. I'm right. And in the world, the development of 4G-merezh, the popularity of such a device of smartphones is only growing.
Everything began in one of the computer laboratories of Cambridge on the cob of the 90s of the last century, if the Global Web only began its journey as a planet. A group of scientists, 15-20 people, worked on a project in the region mesh technologies. Wash the robots with spartan bules - only one kavovark fell on the whole team, as they could not satisfy the consumption of the whole team. The main work was carried out in the laboratory, the staff is alive at the same house, but in the other part. In order to invigorate the romatic process with a cup of drunken water, the participants in the scientific project were often disturbed by the corridor, which was higher on top, where the kavovarka was rotting. Often, such campaigns ignited the collapse, the shards of the deacons' colleagues were already grasping the omriyana's capacity. The situation seemed to be a non-standard solution, and I knew it.

One of the computers at the laboratory is equipped with video capture (frame grabber). A camera was connected to the new one, directed to the guarded object. This computer engraved the role of an IP-server with the help of specially written software. Bajayuchi nobility, chi є kava, are guilty of launching on their computer client software that connects to the server. As a result of remote computer the little one had a black and white image, which was changed to trich on the whilina. A note about this cicavi complex was published in Comm-Week on September 27, 1992. From the moment the first prototypes of IP-cameras appeared, not so rich an hour passed, but the stench has already changed into a number of moldings, a large class of outbuildings, which make everyday life simpler, more efficient and more fun.
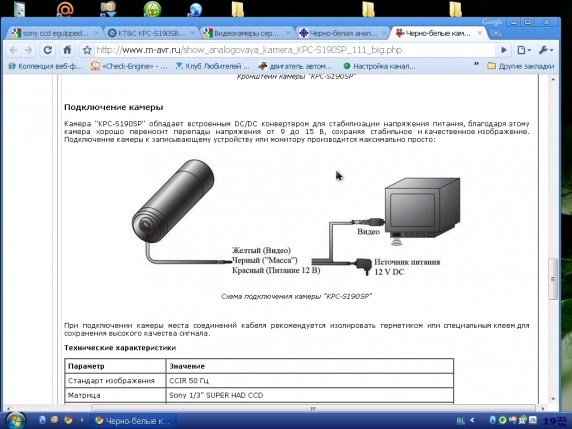
How the IP camera is plugged in
Vaughn is folded forward from the sensor.
Even more often than not, standard CCD matrices for video surveillance are replaced by cheap CMOS sensors. If you want to stench lower sensitivity and not a good transfer of color, they allow you to greatly reduce the price of attachments, shards and sensors are an "all in one microcircuit" with a digital output of data.
Next: a microprocessor for compressing video and detecting noise (or just a microcircuit of the compressor) enters the warehouse of the framing chamber. The most popular JPEG, as the simplest and found; Dosit often vikoristovuєtsya also MPEG4, nayridkіsnіshim and more expensive є MPEG2. With the completed patent for arithmetic coding, WaveLet is gaining popularity. І, nareshti, 10/100 Mb/s controller enters the warehouse of the truss chamber.

Attached is the working principle of the IP camera:
A modern IP-camera is a digital add-on for video recording, digitizing, compressing and transmission over computer system video image. The following components are included in the stock of the IP camera:
- PZZ-matrix
- lens
- Optical filter
- video capture fee
- block of compression (squeezing) of video image
- central processor and wake-up IP server
- RAM
- flash memory
- mesh interface
- Last porty
- anxious enter/exit
As a photodetector, most IP-cameras have a CCD-matrix (CCD, CCD - an attachment with a charge link) - a rectangular, light-sensitive conductive plate with 3: 4 sides, which transforms the light that falls on it into an electric signal. The PZZ-matrix is composed of a large number of light-sensitive centers. In order to increase the light sensitivity of the PZZ-matrix, the structure is often molded, as if creating a microlens in front of the skin center. In the technical parameters of the IP camera, select the format of the PZZ-matrix (the length of the diagonal of the matrix in inches), the number of effective pixels, the type of stripe (row or through) and sensitivity. A typical IP camera contains a lens, an optical filter, a CCD matrix, a digital image processing circuit, an image compression circuit, and an IP server for connection to the camera. A leather-lined video camera can control the IP-address, enumerate functions, and it has a software security that allows it to function as an IP server, FTP server, FTP client, and e-mail client. Most of today's video cameras include a lot of other useful functions, such as a motion detector, alarm input/output and e-mail alert.

Advantages of a mesh (IP) camera in front of a PC-based camera
Built-in IP-server, for transferring the captured image in bulk, no camera is required direct connection to the computer, or whether there are other hardware or software features.  t
t
Merezheva chamber
PC based camera
Hnuchkist
If you place a camera, you can connect it with a wire for an additional modem, style phone, or dartless adapter.
Attached PC camera can be within 3 meters of the computer.
All videos are promptly transmitted as soon as possible without any hiccups and additional possession.
Crim camera You need a computer and software security.
Installation
You just set the IP address and the camera is ready to work
The installation of drivers and software on the PC is simplified.
Easy at vikoristanni
You can look at the image using a standard IP browser on any PC.
If you require the same software security, you will be able to have daily access to the distant administrator.
Stability
The camera works without being additive components giving great stability.
Crim cameras, stability of the robot and lie down and in view of the stability of the computer and software.
Yakist
High quality of MJPEG.
The components are not victorious high capacity zvіdsi small razdіlna building.

Vartist
The versatility of the framing chamber is only the same as the versatility of the framing chamber.
Solution versatility \u003d Global camera versatility + computer + software security.
How to connect the IP camera of the local network.
You will need the following components: a computer, a lamp, a network camera and a local Ethernet network. Also explore options dartless connection
The butt of the organization of the video warning in the office behind the entrance doors
Krok 1: Identify your needs
Do you want to win a camera for a closed host? Abo for zovnіshny zastosuvannya?
Do you want a camera with fixing a glance around, or changing it, which will allow you to pan, heal, or change the scale of the image?
You need additional options, type of motion detector, alarm alert, Ethernet camera live, audio?
Do you want to just posterigate or write a record for him, what do you think?
Do you need a guard of the camera from the outside inlet?
Choose how many cameras you need for your needs.
Krok 2: System support
If your future has not yet laid a local fence, if you allow you to simply put the fence camera into the fence, then you will require the following:
Svitcher, which will be the central point of connection between your mesh camera and your computer computer

Take two Ethernet cables: one to connect your wired camera with a lamp and the other to connect a camera with a lamp to your computer.
Lesson 3: Installation.
Connect all attachments one by one through the lamp
Lesson 4: Assign an IP address for the security camera.
You are responsible for assigning an IP address to your tethered camera so that you can access it through an IP browser on your computer. You can choose between automatic and static IP address. A static IP address is recommended, as you will never be able to sniff out the IP address of the camera.
To set the IP address of the tiled camera. You can hack software security, as it is on a CD, which is included with the product, or you can take advantage of the wizard's website or for an additional protocol-assisted method to assign an address or the ping utility. If you like, you will know all the information in the installation guide to the tread chamber
Krok 5: Finish the installation of the camera.
Once the IP address has been recognized, you can open the IP browser on your desktop computer and enter the IP address of the tiled camera in the address field. For new devices with Internet Explorer IP-browser, the browser asks you if you want to start a program for working with a camera. Tsya program є obov'yazkovayu in order to see the video quickly from the video server or video cameras. It also takes care of managing MPEG-2, MPEG-4 formats, audio streams, crash detection and panning / zooming / zooming in the browser window. (Other IP browsers may support different streaming video streams and may not allow additional components to be installed.)

Press the "Yes" button to install the program
How to access the IP camera via the Internet
Butt: If you already take images from IP-cameras on your computer, you see that if it were bad mothers I could go to the camera, de ІІnternet. For example, like a manager in a store, you want to control the work in the store from your booth, to replace the need for work at the workplace
Krok 1: System support
Scenario A)
If your phone (maybe the camera is installed) is already connected via Ethernet to the Internet Service Provider (Internet Service Provider), just connect physical record, add the tethered camera to the lamp through the tethered window, and you should take the tethered camera dynamically assigned to the public IP address. Select the installation commands for the mesh camera. A special program or utility to the IP camera will be incorrect in the identification of the IP address.
The recognized IP addresses can be changed by your supplier to the Internet service (through the intermediary delivery of the IP address that is shared among їє clients), you can recognize that you can attach the name of the camera to the IP address you can in Croc4 below.
Scenario B)

If your booth is not equipped with Ethernet access, then in most cases you may need the following add-ons:
Broadband modem for connection of asymmetric digital subscriber line (which sound is supplied by your Internet service provider) or cable TV
A broadband router, which may also be called an Internet Gateway, (A broadband router allows local networks to simultaneously connect to the Internet. It can also serve as an interface between the Internet, the ISP and the local network.)
Svitcher, which allows small outbuildings interlinking without intermediary one to one and giving the possibility to add-ons from the local network of mothers with IP-addresses),
NOTE: Most wide-range routers may have the SWITCHER function, such a rank is not needed.
Merezheva chamber
local computer
Computer for remote control
Krok 2: Assign an IP address for your camera, 
Since a wide-range router typically assigns automatic, local IP addresses for outbuildings in a local area, IP addresses and authority may change. Static (permanent) IP addresses are recommended for tethered cameras. To consider a static IP address, find out about the range of the router's IP address, which, for example, can be from 192.168.0.2 to 192.168.0.35. If you want to change the IP address within a range, such as 192.168.0.100, as a static IP address for the camera, it's safe to assume that your attachments will conflict with other attachments, as they will override automatic addresses.
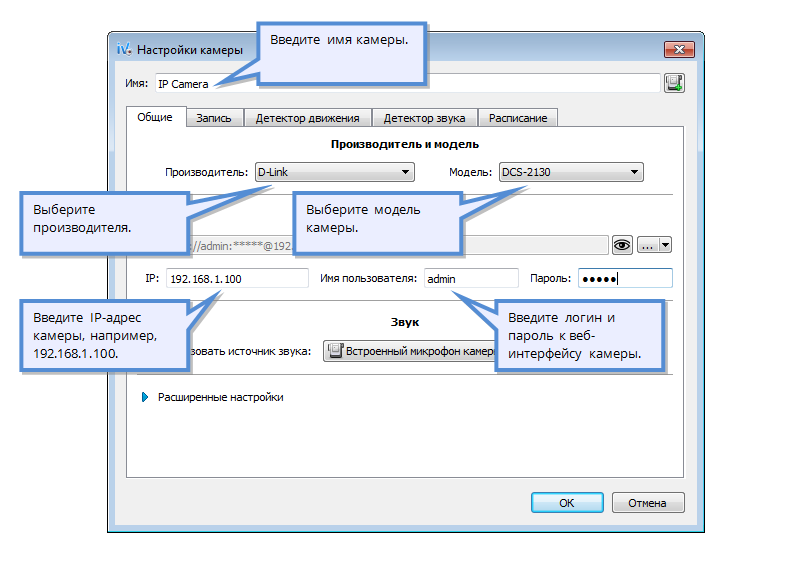
The set IP address for your camera can be broken in three different ways, as specified in the camera's help. As soon as the IP address is recognized, set the password, and the gateway (this information may be taken from the router), and set the camera settings: password, registering the password to secure access to the camera.
Lesson 3: Port Forwarding
A wide-range router, as previously predicted, provides an interface between the Internet, the Provider and the Local Network. The router takes the IP address from the provider of the Internet service and supplies internal (local) IP-addresses for extensions to the local area.
To remove access to the firewall camera, which is permanently located in the local firewall, you must identify the calling IP address of your router (your router's miraculous helper), and configure your router so that the calling IP address is directed to a static, male IP address. merging chamber addresses. This process is named for the port; So if you call the IP address of the router from any networked computer, the Internet will recognize the location of your router, and forward your call to the local IP address assigned to the networked camera.
Launch an IP browser and see it on the IP side of the router via Enter to the configuration side of the router.
Find the menu item "port forwarding" (or similar), with a table approximately as shown below:
Service name
Port on the cob
Port of kіntsia
Server IP addresses
Not lashed
HTTP (Merezha)
If the camera overpowers its video over HTTP, you are responsible for configuring the HTTP service in the following way:
Service name
Port on the cob
Port of kіntsia
Server IP addresses
Not lashed
HTTP (Merezha)
unofficial port
192.168.0.10x
Save the configuration at the router and see from the side of the configuration. Vikonan configuration. Any queries that reach the outside IP address of the router on port 80 will be directed by the IP address of the camera: 192.168.0.100.
If you want to make more than one network camera accessible via the Internet, then you are responsible for installing an additional (unofficial) port on the router, type 80xx and linking them with the network IP address of the camera.
Krok 4: What you can know is that your supplier of the Internet service often changes the Dfi call of the IP address
Create an oblique record with the DNS service as a service and register it domain names(for example, www.nic.ru, etc.) and link it to the original IP address. Im'ya domain, type www.IP-kamera.ru, є ozumіlim koristuvachevі, yogo is easy to remember, and you can recognize the skin domain as your own tassels, tobto. yogo IP addresses. So, if the IP address of the router is changed, it will be automatically registered with the DNS service, in order to update your IP address in such a way that you can go to your network camera at the same address. h
Most of the wide range routers can support DNS like www.dyndns.org.
Another alternative: you can buy or rent a static IP address from your provider of the Internet service.
How to help the IP cameras induce the security system
Effective way The expansion of security systems in everyday life, in factories, at the medical center and the university campus is helping to ensure that the existing infrastructure is already in place:
The stretch of the day, wondering about the monitor at the control room
At night, at the weekend, the watch can be seen farther away at the central guard station, which serves the service desk of the company
When the rumble detector wakes up, it can call the alarm and open the recording of the alarm
At times of alarm, the security officer can look at the image on the closest computer to the new computer, or remotely through the connection to the Internet.
The image may be damaged in the computer on the premises or on the server of the provider of the Internet service (provider). Taking care of the image at the distant places, you use the risk, so that the evildoer will protect the evildoers.
The cameras can also take the image automatically on the head computer, or the head computer itself can take the image from the cameras. What is installed on the head computer Windows system, you can win special software security, razrobleny for merezhevih chambers. The program can display images in real time or work with archives. If the term for saving video image becomes, for example, two days, the program automatically erases them.
tinyCam Monitor
You can turn your smartphone into an IP camera and you can change it to review the picture from the actual cameras. Zokrema retailers, well-looked-for, IP Webcam to promote the tinyCam Monitor program, available in cost-free and paid (about 125 rubles) versions. The functionality of the program includes:
Support of M-JPEG IP cameras/video servers and webcams of the used vibrators, incl. Axis, FOSCAM, D-Link, Edimax, Panasonic, Pixord, TRENDnet, Mobotix, Vivotek, Beward. New translation available on the official website;
Watching up to 4 cameras at once (16 maximum);
3 types of multiscreens;
Last mode;
Changeover function email both import/export to memory card or Dropbox service;
Control of Pan/Tilt/Zoom cameras;
Digital image enhancement;
Save money to SD card.
The paid pro version has:
Additional multi-screens;
Cyclic video recording to SD/FTP/Dropbox;

Unfurnished number of outbuildings;
Sound (for extensions of deyaky virobniki);
Poshuk cameras at the local yard;
Support SSL (protocol https);
Pidtrimka ruhu detector (for deyaky pickers);
Technical support retailers.