Audit file access linux. How to audit the security of the server and not turbulent about the turn of events. Victory Linux security extensions
Defender of information is a priority food for any business that works on the Internet. Virus infection and malicious attacks, as well as unauthorized access to information - all cause great financial and reputational risks. That is why, choosing a server platform, the masters of the business must be called the stage of the protection of resources.
And in order to reconsider, how well the system works well, there is no such thing as “dir” in it, at least once a month it is recommended to audit the security of the server.
What to enter before the server security audit
A threat to security can be an insignificant, at first glance, factor, such as incorrect installation of the server itself or outdated security software. The audit helps to reveal weak cases of fraud and to live your own visits for their adoption before the infection or theft of data occurs.
Server administrator to re-verify the installed software, check it remaining updates, evaluating the improvement of the security of the server and the use of pardons, as well as the analysis of the security of the improvement of the access rights of spivrobitnikiv to other resources.
How to audit a virtual seen server with your own hands
Revisiting the security of servers on Windows or Linux platforms can be difficult, for whom it is necessary to have special knowledge in programming.
The safety review can be divided into several stages:
Physical access
A vipadku with a vidilenim server has physical access to the server of third-party environments by default, which secures the data center. Ale Koristuvach can optionally enter a password to access the BIOS.
Intermediate screen
For uninterrupted control of the PZ and ports, it is necessary to properly fix and improve windows firewall. For Linux, you can hack SELinux for access control. You can also order a Cisco ASA hardware firewall or Fortinet FortiGate 60D.
File system
Re-verification of updates
Set the server to automatically cancel that installation update.
Password policy
Install for help local policies Windows security obov'yazkovo vmagati collapsible passwords, the term їх dії, as well as blocking the oblіkovogo record after dekіlkoh not far authorization or entering an empty password.
Log control
Maintain log records for critical infrastructure segments and check them regularly.
Merezheva Bezpeka
For node segmentation and channel security, it is recommended to select VPN and VLAN.
Also next change standard customization and redirect the port services of the merezhnogo obladnannya.
To encrypt traffic, you can use the IPsec service. And for the review of the critical ports, the Netstat utility.
Access control
Separate access rights for shortlisted files to critical files, enable guest access and shortlisted access with an empty password. Viknіt roles and programs, yakі not vikoristovuyutsya, on the server.
Backup
Hurry up with the service of a backup copy of the files, it’s viable and nadіyno. Don't save backup copies unencrypted. If you rent a server, you can choose a place for backups.
Access to databases
Critically important data bases should be stored in different SQL servers. It is necessary to start the launch according to the name of the koristuvach with minimal changes, or in the form of a previously configured white list of IP-addresses.
Antivirus Zakhist
For robotic server Windows installation anti-virus firmware, which is automatically updated, is recommended when working fencing. For Linux installation antivirus is not needed for regular monitoring of server security and control of unauthorized access. For whom you can use the Tiger utility.
Such an audit once a month will help you reconsider the correctness of the server's work, reduce the inconsistency and control the security of the infrastructure.
The security of the Linux server can be even more important for the protection of your data, intellectual power and the hour in the hands of burglars. The system administrator is responsible for the security of the Linux operating system. In this article, we can look at twenty speeches, as if it were necessary to work with your Linux operating system, so that it was safe and securely stolen forever. Yakscho tse home computer, then about security, it is possible, and there is no sensation of turbulence on the flooring, it will be enough to have the right passwords and close access to ports from the internet. Ale, at the time of the public server, varto turn respect for the security of the zakhist.
These instructions are for any distribution, no matter how you win CentOS, Red Hat or Ubuntu, Debian.
1. Encrypted call
The data that is transmitted through the link is submitted for monitoring. Therefore, it is necessary to encrypt the transmitted data there, if possible for additional passwords, keys or certificates.
Use scp, ssh, rsync or sftp to transfer files. You can also mount the remote file system in your home directory with the help of tools like shhfs.
GnuPG allows you to encrypt and sign your data with the help of a special private key. Also, there are functions for key traversal and access to open keys.
Fugu is a graphical tool for transferring files over the SFTP protocol. SFTP is similar to FTP, but the whole session is encrypted here. This means that valid passwords or commands are not transmitted from the open source. And to that such transfers are less irritating for the third parties. You can also host FileZilla, a cross-platform FTP client with FTS support via SSH/TLS and SSH File Transfer Protocol (SFTP).
OpenVPN is an efficient and lightweight VPN client that supports SSH encryption.
2. Try not to trick FTP, Telnet, Rlogin and RSH
For most of the networks, the names of the correspondents, passwords for FTP, Telnet, RSH commands can be interchanged, be it for the assistance of a packet analyzer. The biggest difference is the problem of OpenSSH, SFTP or SFTP, which adds SSL or TLS to the original FTP. Enter the following command to disable NIS, RSH and other outdated services:
yum erase inetd xinetd ypserv tftp-server telnet-server rsh-serve
3. Change the amount of software
Do you really need all the installed web services? Do not install non-traditional software security in order to avoid the inconsistencies of these programs. Use your package manager to look at installed programs and remove all unnecessary:
yum list installed
$ yum list package
$ yum remove package
dpkg --list
$ dpkg --info package
$apt-get remove package
4. One machine - one service
Run different services on up to 4 servers or virtual machines. This is between the number of services, which may be compromised. For example, as an intruder, you can attack Apache, vin denies access to the entire server. Including such services as MySQL, server email and so far. You can tweak software like XEN or OpenVZ for virtualization.
5. Trim the Linux kernel and firmware in the current state
Installing security patches - this is an important part to improve the security of a Linux server. The operating system provides all the tools to support the system in the current state and upgrade to new versions. Usi novlennya bezpeke blagovnі zastosovuvatisya aknaishvidshe. Here it is also necessary to tweak your package manager. For example:
Abo for Debian-based systems:
sudo apt update && sudo apt upgrade
You can update Red Hat or Fedora to be notified by email when new security updates are available. So you can fix automatic update via cron, or you can hack aptcron on Debian to tell you about the need to upgrade the system.
6. Use the Linux security extension
The Linux operating system comes with various security patches that can be used to protect against incorrect configuration or shkidlivih programs. Ale, you can also beat this supplementary systems access control for SELinux programs or AppArrmor.
SELinux provides different security policies for the Linux kernel. Here you can control access to any resources of the system for additional roles. Until then, another resource can be denied access to a program only, the role of which allows it to be protected and to acquire the rights of a super-correct person does not matter. SELinux greatly enhances the security of the Linux system, scaling to root is important here the greatest koristuvach. The report is described in the next article.
7. Oblіkovі records koristuvachіv and nadіynі passwords
Use the useradd and usermod commands to create and maintain cloud records. Reconsider that you have a good and strong password, it is the fault of the place to recognize all the symbols, it is necessary for a different register, in the middle of which special symbols and numbers may be used. For example, 8 symbols, for example, one symbol or a number. Crack tools like John the ripper to know the weak passwords of cores on the server, and tweak pam_cracklib.so to secure the password policy.
8. Change passwords every hour
The change command will let you specify the number of days before the date of the primus password change. This information is victorious by the system for the purpose of the moment, if the coristuvach can change it. The settings are located in /etc/login.defs. To remove the old password, enter the next command:
change -l koristuvach_name
To remove information about the password strings, enter the command:
You can also set everything up manually in the /etc/shadow file:
(koristuvach): (password): (Stop_change):(max_days): (minimum_days): (Advanced):(deactivate):(appendix_row):
- Minimum days- The minimum interval between changing passwords, so that you can often change the password.
- Max days- how many days will be the password, after the completion of this term, you will hesitate to change the password.
- Advance- the number of days after there will be a warning that you will need to change the password.
- Applicability string- number of days since the first of September 1970, if the account will be more active.
chage -M 60 -m 7 -W 7 chage_name
So it’s a good idea to fence the koristuvachas to vikoristovuvat old passwords, otherwise all the magic with samples of learning and primus primus change passwords will be zvedenі nіvets.
9. Block public records after recent login attempts
On a Linux operating system, you can type in the faillog command to look around and try log in. Also, for help, you can set a limit for nearby attempts to enter. All information about the recent login is collected from the file /var/log/faillog. To be amazed, type:
And in order to set a limit on the sample input for the song oblikovy record, sing:
faillog -r -u
You can also manually block or unblock the account with the help of the passwd command. To block, vikoristovyte:
passwd -l coristuvach
And for unlocking:
passwd -u
It is also necessary to reverify chi є in the system oblіkovі records with empty passwords. For whom do you need to know:
awk -F: "($2 == "") (print)" /etc/shadow
So perverte, chi no koristuvachiv with a group or id 0. Such a koristuvach is guilty of only one, and not root. You can reverse it for the help of such a command:
awk -F: "($3 == "0") (print)" /etc/passwd
Might be less than one row:
root:x:0:0:root:/root:/bin/bash
Yakshcho є інші - vydalіt їх. Koristuvachі, and especially їhnі weak passwords - one of the most poignant speeches that can break security in linux.
10. Withdraw the entry for the supercorristuvacha
To save the security of the linux system, do not hack the entry as root as root. You can type sudo to take care of the necessary steps and run the command as the name of the supercoder. This command allows you not to reveal the password of the supercorrect to other administrators, as well as to avenge the monitoring tools, the exchange and the supervision.
11. Physical security of the server
Linux server security is the responsibility of physical security. You are responsible for physical access to the server console. Adjust the BIOS in such a way that it does not interfere with the entanglement from external media, such as DVD, CD, USB. Also set a password on the BIOS and zavantazhuvach GRUB, to protect its parameters.
12. Eliminate obscene services
Turn on all services and demons that do not win. Also, do not forget to see the services of auto-advancement. You can view the list of currently active services on Red Hat systems with the command:
chkconfig --list | grep "3:on"
To enable the service, twist:
service stop
$chkconfig service off
Know all the windows of the porting programs:
Those same can be used for the help of the nmap scanner:
nmap -sT -O localhost
Vykorist iptables to close all ports, as if not guilty but available from the fringes. Abo zupinіt inappropriate services as described above.
13. View X server
X server on the server computer - rich zovsim neobov'yazkova. You don't need to run graphical sharpening on the seen Apache server or Email. Vydalіt tse software security to improve security and productivity.
14. Set up Iptables
iptables is a program for setting up the Netfilter firewall installed in the core of the firewall. Win allows you to filter all traffic and only allow you to see traffic. Also tweet TCPWrappers - an ACL system for filtering Internet access. You can prevent anonymous types of DOS attacks from help iptables. Merezheva Bezpeka in Linux important moment global security system.
15. Get the Core
At the /etc/sysctl.conf file, the kernel settings are saved, as they are set up and stopped before the system starts.
Enable execshield buffer overflow protection:
kernel.exec-shield=1
kernel.randomize_va_space=1
Turn on the protection of IP details:
net.ipv4.conf.all.rp_filter=1
Wimknut redirect IP address:
net.ipv4.conf.all.accept_source_route=0
Ignore wide range requests:
net.ipv4.icmp_echo_ignore_broadcasts=1
net.ipv4.icmp_ignore_bogus_error_messages=1
Log all updated packages:
net.ipv4.conf.all.log_martians=1
16. Break the hard drive into pieces
Podil hard drive for distribution in the fallow in the recognition of files to improve the security of Linux OS. It is recommended to work on the distribution for the following directories:
- /home
- /var and /var/tmp
Create extensions for Apache root directories and FTP servers. Open the /etc/fstab file and install special options for the required distributions:
- noexec- don't hack whether it's a program or files that tag on any distribution, only scripts are allowed
- nodev- do not allow symbolic or special attachments to the distribution.
- nosuid- do not allow SUID/SGID access to the software distribution.
17. Vickory disk space
Surround the available disk space for koristuvachiv. To create the /etc/fstab disk quota, remount the file systems and create the disk quota database. Tse to promote security in Linux.
18. Disable IPv6
Internet protocol of the new generation IPv6 in the future to replace IPv4, which is already victorious. But at the same time, there are no tools that allow you to convert security measures based on IPv6. Many Linux distributions allow IPv6 to be rebranded on a promotional basis. Hackers can overpower bad traffic and administrators can't handle it. So if you don’t need this service, turn it on.
19. Switch binaries that don't win SUID and SGID.
All files that are signed for such inclusions of SUID or SGID flags are potentially unsafe. This ensign means that the program will be vikonuvatsya іz the rights of a supercorristuvacha. And tse means that as in the program, as if the difference is a bug, then the local chi in the distance koristuvach You may have a featured file. Find these files for additional offensive command:
find/-perm +4000
Find files from install SGID ensign:
find/-perm +2000
Or combine everything in one command:
find / \(-perm -4000 -o -perm -2000 \) -print
$ find / -path -prune -o -type f -perm +6000 -ls
You will have to report on the knowledge of the skin of the file, in order to understand how much the other file is needed.
20. Downloadable files
It is also necessary to know the files, so that they can change all the files in the system. For which one, type the following command:
find /dir -xdev -type d \(-perm -0002 -a! -perm -1000 \) -print
Now you will need to check that the rights for the group and the spymaster of this skin file are correctly set and that they do not carry security threats.
It is also necessary to know all the files that no one should lie:
find /dir -xdev \(-nouser-o-nogroup\) -print
21. Win a centralized authentication system
Without a centralized system of authentication, the data of the coristuvach become super-obvious, which can bring back to the old oblіkovyh data, and obliteration of oblіkovyh records, as if guilty were already long gone. The service is centralized to allow control over oblique records and authentication data of coristuvachs on retail Linux systems and Unix. You can synchronize authentication data between servers. Ale do not endorse the NIS service, rather look at Open DAP.
One of the most famous implementations of such a system is Kerberos. It allows you to use the authentication of the coristuvachs for the help of the secret key, in the chains, de packets can be interchanged and modified. Kerberos victorious symmetric key for data encryption and help for the robotic key management center. You can improve the remote entry, remote copying, protect the copying of files between systems and other tasks with a high level of security.
22. Logging and auditing
Configure logging and auditing to collect and save all recent attempts to enter and try malicious. For the lock, we have the logs, or, we accept, most of them are found in the papacy /var/log/. Reports about those for which they give songs, we spoke in an okremіy statt.
You can marvel at the logs for the help of such utilities as logwatch or logcheck. The stench will ask you to read the logs. You can not look at the entire file, but only look at what to click on you, and also send your own notifications to the email address.
Keep an eye on the system for help with the auditd service. The program writes to the disk must be audited, like you tsіkavlyat. Audit settings are saved from the /etc/audit.rules file when the system starts, the service reads all the rules for that file. You can do it and fix everything as you need it, or use the smart utility - auditctl. You can create such moments:
- Submit the launch of that vimic system
- Date that hour
- Podії koristuvach (for example, access to the song file)
- Type of account (editing, access, remote, recording, updating only)
- Away or zbіy at vikonannі podії
- Record of subdivision
- Recording change of koristuvachiv that group
- Monitoring file changes
23. Secure OpenSSH Server
Allow me to revisit protocol 2:
Block the entrance to the name of the supercorristuvach:
24. Install IDS
IDS or the intrusion detection system is spoofed to detect suspected, disruptive activity, such as a DOS attack, port scanning, or try to hack the computer with a way to monitor intermediary traffic.
It is good practice to open up similar software security, before that the system will become accessible to the Internet. You can install AIDE or HIDS (Host based IDS) so that you can control all aspects of the internal setup of your system.
Snort - all security software for detecting intrusions from a region. Won zdatna vikonuvaty analysis and logging packets and analyze network traffic in real time.
25. Protect your files and directories
Linux has vіdminnі zasobi protection against unauthorized access to files. However, allowing Linux to be installed and the file system does not mean anything, if the attacker can have physical access to the computer and you can just connect hard drive computer to your system to copy your data. Alevi you can easily steal your files with additional encryption:
- To encrypt and decrypt the file with a password, use GPG
- You can also steal files for help OpenSSL
- Encryption of directories is dependent on the help of ecryptfs
- TrueCrypt - a powerful tool for encrypting disks on Windows and Linux
Visnovki
Now security OS linux on your computer will be richly improved. Don't forget to put collapsible passwords and inodes. Write in the comments your favorite tool for system security.
Power supply security of IT-infrastructure can be of great relevance for any business. Whether it's a group of companies with a lined mesh or an online store with 1-2 sellers.
For a skin server, which is the main source of hosting for sites, it is worth to pay for the security of the protection of data from the host.
Our company serves as a server security audit.
This service includes:
- Analysis of software versions installed on the server, according to the latest current versions, mitigating security problems. As a rule, for web servers, the relevance of the versions of the offensive firmware is important: mail server, web server, cache web server (as such a present one), movie programming interpreter (on which site is written, for example, PHP), ftp server, web add-ons danimi);
- Analyz nalashtuvan web server, nalashtuvan adjunct PZ schodo vіdpovіdnostі main vomogi, shcho pred'yavlyayutsya before security;
- Analysis of the improvement of the operating system. Behind this point, there is an analysis of the main points related to the potential for the attacker to gain control over the server. As a rule, look around the parameters of the ssh server, the options for working with hard disks;
- Analysis of access rights to the main files and folders of the system, to protect confidential information. As a rule, within the framework of this item, there is an overview of the main system folders, the files in the server backup panel, directories with backup copies, the rights of the folder of the files;
— On the server, which perebuvaє pіd pіdzroyu, scho vіn compromises, and can vikoristovuvatysya zlovіgtovvatsya by zlovіgni for shkіdlivyh diy, our fahivtsі vykonyatyat nebhіdnі come in order to clear it from shkіdlіh programs, and to avoid repeating the situation;
Set up a server security audit once a month for regular monitoring possible problems, caused by malicious intrusions on the server
If you don't see any signs of third-party activity on the VPS or on the site, watch out for the next series of revisions and corrections to hijack the server from an evil one.
Nalashtuvannya on the applied level
If a CMS is installed on the server, it will be turned over, and all the rest of the updates will be installed.
Joomla
From the root directory of the site, find the file changelog.txt, from which you can find information about the CMS version. Like it's out of date, update Joomla.
Wordpress
Look for the wp-includes/version.php file to find information about the CMS version. Like it's outdated, update Wordpress.
DLE
Look for the engine/data/config.php file, find the version_id row and check if the version is not out of date.
Also change the files engine/ajax/updates.php and upgrade/index.php (parameter $dle_version).
1C-Bitrix
Look for the /bitrix/modules/main/classes/general/version.php file to find information about the CMS version. Also change the /bitrix/admin/update_system.php file. If the version is outdated, update 1C-Bitrix.
Drupal
From the root directory of the site, find the file changelog.txt, from which you can find information about the CMS version. If it's out of date, update Drupal.
Change the kernel version in the /modules/system/system.info file.
You can also know the version of the CMS through the keypad.
Vykonayte reverbka web server.
Apache
Open configuration Apache file(there may be files httpd.conf, httpd2.conf, apache.conf, apache2.conf) and change the directive to the new one to include information about the web server version:
ServerTokensProd
If there is no directive, then add it to save the file.
Look for the file secure.conf, open yogo for a review and zip yogo together with the stepping butt:
Your secure.conf is not to blame for the nature of your authority in the pointed butt.
Reverse the MRM installations by the team
Apachectl-V
For more security, vicorist mpm_itk, as there is no need for mpm_prefork.
If you want to change the MRM, please re-install it by making backup copies of the configuration files first. After reinstallation, turn over, chi є the site manager and yogo directory koristuvach.
Nginx
Open the web server configuration file (nginx.conf), go to the http section and change the directive to limit the number of connections per IP address:
Limit_zone slimits $binary_remote_addr 5m; limit_conn slimits 10; or (for other versions) limit_conn_zone $binary_remote_addr zone=addr:10m; limit_conn addr 10;
If there are no directives, then add and save the file.
Block User Agents to block non-baggage traffic. Before the http section of the Nginx configuration file add the directive
If ($http_user_agent ~* LWP::Simple|BBBike|wget|msnbot) (return 403;)
Block referral spam by adding the directive to the http section of the Nginx configuration file
If($http_referer ~*(babes|forsale|girl|jewelry|love|nudit|organic|poker|porn|sex|teen))(return 403;)
ISPmanager
On the ISPmanager clarification panel, type in such revisions.
Pereverte, chi obmezheniya access to the panel karuvannya IP-address.
Get it right backup copy danikh, as the won is not included. We recommend vicoristing old disk for backup, to prevent the loss of data at once with the archive.
PHP
Open the php.ini configuration file and add the next directives.
Expose_php=Off - disable transfer of PHP version information to HTTP header; sql.safe_mode = On - enable SQL safe-mode; post_max_size=8M - size limit for data sent by POST method; disable_functions exec, system, passthru, proc_open, shell_exec - enable certain functions for safety reasons.
NTP
Add rows to the NTP configuration file (by locking /etc/ntp.conf) to block recursive requests:
127.0.0.1 127.0.0.1 127.0.0.1 Restrict -6::1
Bind
Add rows to the named.conf file to block recursive queries:
Allow-recursion( 127.0.0.1; 82.146.32.0/19; 78.24.216.0/21; 92.63.96.0/20; 62.109.0.0/19; 188.120.224.0/1;5;2; 94.250.248.0/21;);
Rechecking the copy of the directory to the site
Change who should have the main directory for the site and all the subdirectories.
On the ISPmanager toolbar, go to the "System" -> "File Manager" section and open the site directory. Change, scho at the stovptsy "Vlasnik" and "Group" stand koristuvach-vlasnik site. To change attributes, press the “Attributes” button on the toolbar.

Valid names of the master for the site apache, www, www-data, so you can use mpm_prefork. We recommend that you disable mpm_itk for security reasons.
Like a site to sweep folders access(for example, upload, tmp), then for them the name of the vlasnik 777 is acceptable.
Find./-perm 0777
Vaughn know all the folders and files, by the vlasnik of those є 777.
Nalashtuvannya on equal operating system
rhunter
Tweak the rkhunter utility to reveal the server's potential inconsistencies.
To install the utility, type the following command:
Yum install rkhunter - CentOS OS apt-get install rkhunter - Debian/Ubuntu OS make all install clean -C /usr/ports/security/rkhunter or pkg install rkhunter - FreeBSD OS
To update the database of the utility, type out the commands
Rkhunter --update

Rkhunter --propupd
Check the system overhaul with the command
Rkhunter -c --cs2

During the process of rechecking the kilka once, you need to press the Enter key to continue. After completion, information about the result of the recheck will appear.

The results of the verification are placed in the log file /var/log/rkhunter/rkhunter.log, take a look at the yogo for early pardons.
sysctl
Use the sysctl utility to change the kernel parameters of the system. Open the utility configuration file /etc/sysctl.conf and enter the next rows.
Enable the ability to route incoming traffic;
net.ipv4.conf.all.accept_source_route = 0
Enable waiver for ICMP requests over a broadband channel - to help prevent smurf attacks:
Net.ipv4.icmp_echo_ignore_broadcasts = 1
Vymknіt magazine about the wrong pomіdomlennya about pardons:
Net.ipv4.icmp_ignore_bogus_error_responses = 1
Increase memory protection by rewriting memory:
Kernel.exec-shield=1 (CentOS)
Reminder of ASLR memory:
kernel.randomize_va_space = 2
Enable ICMP redirect capability:
net.ipv4.conf.all.accept_redirects=0 net.ipv4.conf.default.accept_redirects=0
You should never win on the VPN server or else special programs, enable forwarding:
Net.ipv4.conf.all.forwarding=0
Highlight SYN-flooding – SYN cookies:
Net.ipv4.tcp_syncookies=1
Set the number of samples to send SYN-ACK packets:
Net.ipv4.tcp_synack_retries = 3
Set an hour, through which server you check the date, as it has not been victorious for a long time (2 years for locking):
Net.ipv4.tcp_keepalive_time=1800
Set the number of reconsiderations of the day, first of all it will be broken:
Net.ipv4.tcp_keepalive_probes=3
Set the socket rebuy hour at the FIN-WAIT-2 station:
net.ipv4.tcp_fin_timeout=30
fstab
Pervert the fstab configuration file (/etc/fstab), in which the information about the disks is stored, split that storage device, and show how the stench is mounted in the system.
vi /etc/fstab
Please note that non-roots have shared the nodev parameter. If /tmp is mounted by a different partition, add nodev, noexec, nosuid for that partition.
rsyslog
Change the file to /etc/rsyslog.conf.
Vi /etc/rsyslog.conf
Give respect to the next rows, like a guilty mother looked:
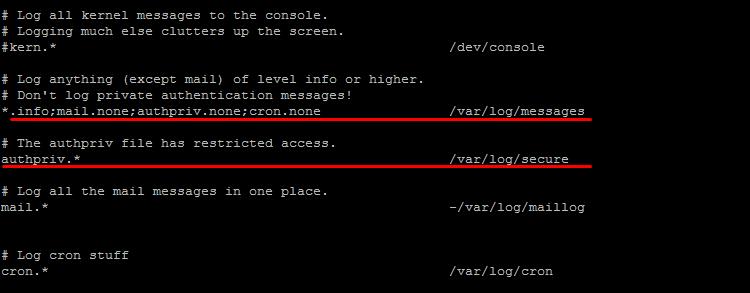
Also, check that the file is not empty, that is. logging is conducted correctly.
sudo
Verify that the sudo utility (or su) has been set up correctly, as it allows you to run root commands and programs with super-root privileges. The settings for this utility can be found in the configuration file /etc/sudoers or /usr/local/etc/sudoers. Open yogo for editing
Vi /etc/sudoers
Find a row, which spellings for locks and allow super-correct root to run commands.

To give all root privileges to run commands as root, add the following line:
ALL ALL=/bin/su or ALL ALL=/usr/bin/su
In order to gain the privilege of running certain commands as root, add the following line:
%users ALL=/sbin/mount - user group can only sudo with mount command user ALL=/sbin/mount - user can only sudo with mount command
Nalashtuvannya on the merezhny river
Reverse, as if porting on the server, and victorious, as if the services were victorious
netstat-tuplnw | awk "(print $4,$NF)" | sort | uniq

For example, the entry 127.0.0.1:53 748/named means that the named service is corrupting 53. Reverse, that among the working services there is no need, except for the rest.
FTP
Set port range for passive FTP mode. To open the configuration file of your FTP server for editing, add the following lines:
for vsftpd.conf:
pasv_min_port=1028 pasv_max_port=1048
for proftpd.conf:
Passive Ports 1028 1048
Don't change the FTP protocol without special needs, use SFTP instead. Even though FTP is still required, add the following rows to the configuration file:
for vsftpd.conf:
Xferlog_enable=YES (ftp log file monitoring) anonymous_enable=NO (fencing anonymous upload uploads) anon_upload_enable=NO anon_mkdir_write_enable=NO
for proftpd.conf:
at the section
iptables
Perevіrte, chi correctly installed firewall. For iptables, type out the command
Iptables-nL
The command to display at the command line is the rules for the iptables firewall. You can also look at these rules and edit the firewall configuration file /etc/sysconfig/iptables - for CentOS OS, /etc/network/if-up.d/ispmgrfw - for Debian/Ubuntu OS.
At the rules of the firewall, close all ports, the room is quiet, which services are victorious, which work on the server. For whom to change the rows
:INPUT ACCEPT :FORWARD ACCEPT :OUTPUT ACCEPT to :INPUT DROP :FORWARD DROP :OUTPUT DROP
Shchab vіdkriti need porti, add rows to the mind
A INPUT -p tcp -m tcp -dport 53 -j ACCEPT -A INPUT -p udp -m udp -dport 53 -j ACCEPT -A INPUT -p tcp -m multiport -sports ACCEPT
de 53 is the number of the port that is required.
Before that, how to make changes to the firewall configuration file, create a copy of the working file.
Firewall rules can be configured from the ISPmanager firewall panel.
SSH
Open SSH config file:
Vi /etc/ssh/sshd_config
Reverse, chi not commented on the next rows:
Protocol 2 (for a different version of the protocol) IgnoreRhosts yes (do not hack.rhost file) HostbasedAuthentication no (do not authenticate the host) PasswordAuthentication yes (allow password authentication)
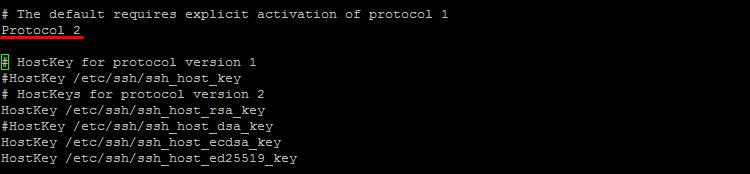
Enable SFTP by adding the line to sshd_config:
Subsystem sftp /usr/lib/openssh/sftp-server
Turn over the mail to check for re-writing and re-send, in the middle of reminding you of no spam.
Click on the mailq command and look at the list of revisions. As the list is already great, it is necessary to reverse the notice, as it may be spam. Assign the sheet guide to the ID (for example, BD65F10DEE4). Team
Exim -Mvh ID_id
display the title of the sheet, and the command
Exim -Mvb ID_id
let me look over the body of the reminder.
In the middle of the headings, the field From: to revenge the administrator, and X-PHP-Originating-Script is the script that sent the notification.
Software security
Change the software security of the server to be inconsistent.
CentOS OS
Enter the command to display a list of files of installed software recently modified:
Rpm -qVa - to display all files, rpm -qVa | awk "$2!="c" (print $0)" - for displaying files behind a bunch of logs.

Analyze how files and how they were changed for the help of such parameters:
S - modified file extension M - modified permissions set behind lock 5 - modified MD5 checksum D - modified major/minor numbers for attachment L - modified symbolic message U - modified file manager G - modified group T - modified file change date (mtime) ) c - configuration file d - documentation file g - file that is not included before the package l - license file r - README file
For example, row S.5....T. c /etc/httpd/conf/httpd.conf means that httpd.conf is the configuration file, changed the checksum and the date of the rest of the change. Oskіlki tse config file, tsі zmіni do not call pіdozr.
Return respect to files, as if for no apparent reason they change the value of the checksum. For such files type the command:
Stat /usr/sbin/sshd && file /usr/sbin/sshd de usr/sbin/sshd - path to the file.
As a result of the command, report information about changing the file will be displayed on the screen.
Win command:
Yum --security update
to install security-update.
Debian OS
Find commands to check MD5 checksums for installed programs:
# apt-get install debsums # debsums -c
Enter the following commands to check the security-update:
# echo 'deb http://security.debian.org wheezy/updates main contrib non-free' >> /etc/apt/sources.list # grep security /etc/apt/sources.list > /etc/apt/secsrc .list # apt-get -s -o Dir::Etc::sourcelist="secsrc.list" -o Dir::Etc::sourceparts="-" upgrade
To install security-update, run the command:
# apt-get -o Dir::Etc::sourcelist="secsrc.list" -o Dir::Etc::sourceparts="-" upgrade
Reverse the presence of all repositories of the gpg version by typing the commands:
# grep -ri gpgcheck /etc/yum.conf # grep -ri gpgcheck /etc/yum.repos.d/ Change your rows so you can see: gpgcheck=1 # grep -ri AllowUnauthenticated /etc/apt/
Rows mind
APT::Get::AllowUnauthenticated "true";
be not guilty.
Non-victorious services
CentOS OS
chkconfig --list
Chkconfig --del service_name de service_name - service name.
Debian OS
Type in a command to display a list of services that do not need to be quoted:
sysv-rc-conf
To enable startup unsigned service hit the command:
sysv-rc-conf in service_name de service_name - service name.
In today's statistics, we know you Best Linux Security Auditing Tools or as our English colleagues seem. Hardening Linux. Also, the topic of the article is a review of the level of security of Linux systems and an assessment of the correctness of configs from the point of view of information security. Zrozumіlo, we do not need to take a look at the programs, but let's put our own whistleblower.
Linux security audit by the authorities
Before the system administrators, and especially before the auditors of information security, it is often necessary to review the protection of a large number of hosts in just a short hour. First of all, for the development of these tasks in the Enterprise-segment, there are specialized tools, for example, just like that. Upevneniy, scho all stinks - from open sources of the OpenVAS engine to commercial products such as Nessus or Nexpose - to our reader. All the while, the software should sound victorious, so that it is old and out of date, and then the software is safe, and then start the patch management. Of course, not all scanners are safe to protect some specific features of the mechanisms for protecting the Linux OS and other products from the open code. Well, and not in the rest of the month, the value of the price of food, even paid products, can afford the company’s own, as they see it right on the budget.
Axis to this year mova pide about specialization recruitment cost-free utilities, as they can diagnose the current level of system security, evaluate potential risks, for example, “download services”, what to erase on the Internet, or an unsafe config for locking, and in some cases, ask for options to fix the problems found by the audit. Another reason for using these tools is to be able to replicate typical scenarios of Fermi re-verification, no matter how many Linux-systems, and to create a documented base of tests at the sight of logs and other sounds.
Practical Aspects of Linux Security Auditing
If the eye of the auditor marvels, then the test before the test can be divided into two types.
pershy- this is why we call compliance-vimog, here the presence of obligatory language elements is reversed, prescribed by any chance international standards or "best practice". Classic butt - PCI DSS for payment IT systems, SOX404, NIST-800 series, .
Other- this is not a rational pidkhid, which is rooted in nutrition “And what else can you do, to help protect yourself?”. Here there are no obov'yazkovyh wimogs - less your knowledge, that head was bright in my hands. For example, updating the kernel version and / or packages of add-ons, enabling, forcing SELinux, setting up the iptables firewall.
Everything that goes to another approach is accepted to be called a special term Linux hardening, which can be designated as “dії, created behind for the strengthening of the equal external protection of the OS (chi PZ) more importantly by the staff”.
p align="justify"> Compliance requirements are usually re-evaluated when preparing for a PCI DSS-type compliance audit or another certification audit. We will give more respect to the Hardening warehouse. All great vendors promote for their products Hardening Guidelines- Helpers, scho retaliate for the sake of that recommendation, how to make it possible to protect, pay staff security mechanisms and the specifics of the PZ. So, similar helpers are available from Red Hat, Debian, Oracle, Cisco.
Hardening is the term for the world of information security, which means the process of securing the security of a system (programs) for the sake of reducing її irritability, as a rule, from a variety of staff utilities or mechanisms of defense.
Before speech, we already had an article about the adjustment of the Hardening options, but in that article it was itself about the adjustment. We will check our system for additional specialized utilities, so we will conduct a security audit, estimate the current level of protection, and then we will wind up the security option, as it will be necessary in the future. Well, it’s more like an option: if the server is already fixed from the point of view of security, our tools can be reversed and, it’s possible, suggest, what can be done.
Linux Security Audit Tools
Lynis - auditing system hardening testing
Installed on macOS:
 Initialization of tests
Initialization of tests  Test results from the System Tool and Boot & Services group
Test results from the System Tool and Boot & Services group  Test results from the Kernel and Memory & Process auditing group
Test results from the Kernel and Memory & Process auditing group  Test results from the User and Group & Authentication group
Test results from the User and Group & Authentication group
Before the audit, thoroughly check what is available New version Lynis:
If you want to put the name of the auditor, which is when running the test, just add the parameter -auditor
sudo lynis audit system - c - auditor Daddy |
At any stage of the Linux security audit, the verification process can be continued (Enter) or pinned (Ctrl+C). The results of these tests will be written to the Lynis log in the /var/log/lynis.log directory. Fuck that the log file is overwritten with a skin offensive launch utilities.
For testing on a permanent basis automatic mode you can consider a separate Cron scheduler for the help of the -cronjob key. In such a way, Lynis starts up after a given template (config) and does not display any interactive prompts, power up in advance. All results will be saved in the beam. For example, the axis of the script is to run the utility with the parameters for locking once a month:
#!/bin/sh AUDITOR="Automated" DATE = $(date + % Y % m % d ) HOST=$(hostname) LOG_DIR="/var/log/lynis" REPORT = ”$LOG_DIR/report-$(HOST). $(DATE) DATA = ”$LOG_DIR/report-data-$(HOST). $(DATE). txt” cd /usr/local/lynis . /lynis -c -auditor "$(AUDITOR)" -cronjob > $(REPORT) mv/var/log/lynis-report. dat$(DATA) #End |
Save this script in the /etc/cron.monthly/lynis directory. І do not forget to add paths for saving logs (/usr/local/lynis and /var/log/lynis), otherwise it may work incorrectly.
You can look at the list of available commands for wiki:
A short instruction on the robot with the utility:
man lynis |
Options for possible statuses behind the revisions are interspersed with the following list: NONE, WEAK, DONE, FOUND, NOT_FOUND, OK, WARNING.
 Status view example
Status view example Launch of okremy tests at Lynis
Really, it is necessary to carry out deeds of singing tests. For example, as your server loses more functionality Mail Server or Apache. For which you can twist the -tests parameter. The command syntax looks like this:
Of course, the functionality of Lynis is expanded by various additions, which can be added independently, or you can add new ones to the directory.
Warnings will be redeemed after results. The skin begins with the text ahead of time, then we instruct the temples to indicate the test that it has generated. At the offensive line, the virishenya of the problem is propagated, as it were, obviously, obviously. For the fact, the rest of the row is the URL address, for which you can look through the details and know additional recommendations, how to fix the problem.
 Visnovok recommendations, how to fix the problems found
Visnovok recommendations, how to fix the problems found Profiles
The profiles that control the audit are assigned to files with extensions.prf located in the /etc/lynis directory. The default profile is called, preempted, default.prf. Rozrobniki do not please the rule of yoga without intermediary: whether you change it, if you want to add it to the audit, it’s better to add it to the custom.prf file, which should be in the same directory.
Create and edit custom profile:
touch/etc/lynis/custom. prf sudo nano /etc/lynis/custom. prf |
For this file, you can assign a list of tests, which may be required to be included in the Lynis audit. For example:
- FILE-6310: revision of distributions;
- HTTP-6622: nginx install test;
- HTTP-6702: Apache installation test.
To disable the song test, use the skip-test directive and enter an ID for the test. For example, like this:
# Is nginx installed? skip-test=HTTP-6622 # Is Apache installed? skip-test=HTTP-6702 |
Assessment of hardening state
Based on the results of all tests in the skin test audit utility (trochs below the distribution of propositions), you will find a distribution that looks something like this:
Lynis security scan details : Hardening index : 57 [ ############.........] Tests performed: 216 Plugins enabled: 0 |
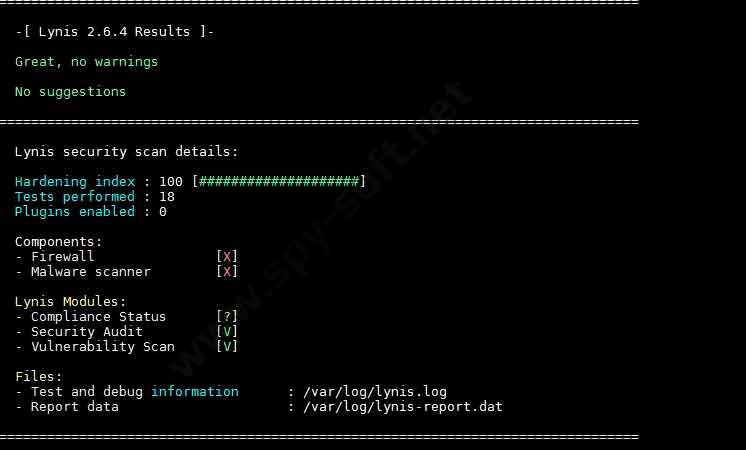 Estimated hardening state
Estimated hardening state
This result, expressed in number, shows the number of tests passed and the system security index, which hardening index- final date, for the help of which Lynis evaluates the high level of server security. And it's important not to forget that the safety index changes in the fall due to the number of corrections ahead of time and following the recommendations of Lynis. Therefore, after correcting problems, a repeated security audit can show a different number!
All manipulations with the system in the supercorrosive mode affect sawy respect and increased viability. Vikonuyte only tі dії, yakі usvіdomlyuєte і like vpevnenі. Don't forget to keep backups and snapshots.
Lunar - a UNIX security auditing tool
Apply to the launch of commands from the CLI:
 Revisiting your settings when launching Lunar
Revisiting your settings when launching Lunar Running Lunar in security audit mode to without making changes to the system:
Translation of tests:
Starting in recovery mode, then from changes made to the system:
 An example of running tests for the Apache web server
An example of running tests for the Apache web server
Nix Auditor - a CIS Audit made easier
Nix Auditor is a script for verification, which checks the security of Linux-systems for the CIS indicator. Targeting RHEL, CentOS and other RPM distributions.
The retailers claim the following benefits for Nix Auditor:
- scanning speed- It is possible to carry out a basic revision of the OS in less than 120 seconds and immediately remove the sound;
- reverification accuracy- the Nix Auditor robot was revised to different versions distributions of CentOS and Red Hat;
- moodiness- documents with documentation before the program are on GitHub, so the code can be easily adjusted to the type of OS and the set of system elements, as it is necessary to change it;
- the simplicity of the victoria- Finish up the start script, we'll finish it, and it's already ready for re-verification.
An example of typing commands for grabbing a utility from a GitHub repository and for launching a script:
git clone https : //github.com/XalfiE/Nix-Auditor.git cd Nix-Auditor chmod +x nixauditor . /nixauditor |
 An example of seeing information after the launch of Nix Auditor
An example of seeing information after the launch of Nix Auditor
Loki - Simple IOC and Incident Response Scanner
The Loki utility is not a classic tool for conducting a Linux audit, but it can also be used to search for evil, but it can often be used to practice auditing.
Like the retailers sing, the axis gives us such a possibility Loki - Simple IOC and Incident Response Scanner:
I. Chotiri ways to manifest evil:
- filenames (depending on the regular expression of the full path to the file);
- revalidation to Yara rules (search for compliance with Yara signatures for files and process memory);
- re-verification and analysis of hashes (comparison of scanned files with hashes (MD5, SHA-1, SHA-256) of existing files);
- re-verification zvorotny zv'azku C2 (leveling the end points of the technological connection with C2 IOC).
II. Additional revisions:
- rechecking the Regin file system (via –reginfs);
- review of anomalies of systemic and cortical processes;
- scanned unpacked SWF;
- rechecking the SAM dump;
- Checking DoublePulsar - a test to find a backdoor that hears port 445/tcp and 3389/tcp.
Trochs torknemos that as a program vyznaє fact evil. Typical signs (Indicators of Compromise), which indicate that the computer has been compromised (tobto zlamaniya), can be:
- the appearance on the computer of shkidlivosti (viruses, backdoors, kryptorivs, etc.)
- the appearance of new and possibly new files, so stinks are not detected antivirus engine like malware code;
- abnormal activity (connection to remote hosts, listening to ports by unknown programs, etc.);
- abnormal activity on disk devices (I / O) and the increase in system resources (CPU, RAM, Swap).
Before the cob of installation, it is necessary to install a sprat of fallow bags. There is colorama (gives console row retrieval), psutil (process remapping utility) and, though not yet installed, the Yara package.
Come on, let's get started. Installing in (there may be Yara package installs before, which is behind Kali Linux installs):
cd loki / python2 loki-upgrader. py python2 loki. py-h |
Installed in Ubuntu/Debian:
sudo apt - get install yara python - yara python - pip python - setuptools python - dev git sudo pip2 install - upgrade pip sudo pip2 install - U setuptools sudo pip2 install psutil netaddr pylzma colorama git clone https://github.com/Neo23x0/Loki cd /home/download/Loki python2 loki-upgrader. py python2 loki. py-h |
Installed by BlackArch:
sudo pacman -S yara python2 -pip python2 -yara sudo pip2 install psutil netaddr pylzma colorama git clone https://github.com/Neo23x0/Loki cd /home/download/Loki python2 loki-upgrader. py python2 loki. py-h |
Butt vikoristannya
Startup options available:
optional arguments : H , -- help show this help message and exit |










